If your printer is set up to email scans or faxes straight to you or a colleague, you may be caught out when Microsoft and Google this month block many peripherals, security cameras, and other devices from accessing their email services using old, insecure ‘basic authentication’ capabilities.
First introduced in 1995 as part of the ubiquitous Simple Mail Transfer Protocol (SMTP), basic authentication (also known as SMTP AUTH) has long been used – both in desktop computer and mobile applications, as well as in network equipment, peripherals, and Internet of Things (IoT) devices – to enable the automatic scanning and sending of documents using just your email username and password.
After you enter your credentials in their configuration screens, the devices can log into your Microsoft Outlook, Google Gmail or other accounts to email you status alerts – enabling security camera systems to send alerts and photos when an intruder is detected, for example, or letting network firewalls tell network administrators when unusual activity suggests that an intruder is trying to break in.
The feature is also widely used for ‘scan-to’ features of printers, faxes, and scanners that automatically emailed documents to a personal email address – but if your device is set up to use a Microsoft or Google account, it will stop working completely when the companies shut off SMTP AUTH on 16 September (for Microsoft Outlook accounts) and 30September (for Google Gmail and Workspace).
This will be an unexpected and significant headache in offices that rely on these features – and most people won’t even know there’s going to be a problem: if your company’s IT specialist entered the details when setting up a device years ago, it may have just been humming along quietly since then.
In large companies, “it is not uncommon to set things up and then just forget about them [because] you don’t even know they’re working,” Deral Heiland, principal IoT security researcher with security firm Rapid7, told Information Age.
Heiland, who maintains a test lab of IoT devices in his office, recalls buying a second-hand office printer that still had the email username and password of its previous owner – a law firm – entered in its configuration screen and still usable for sending emails.
After SMTP AUTH is disabled, he said, “if a business or organisation has decided to use those features, then things could break.”
Email providers have been telegraphing the changes for years – and while large companies’ IT teams may have been preparing, Heiland warned that small and medium businesses (SMBs) and individuals may be less aware of what outside support teams have done – meaning that they are likely to “be caught off guard by this and lose capabilities.”
This printer will no longer be able to use Microsoft and Google email services when the tech giants shut down SMTP AUTH this month. Photo: Supplied
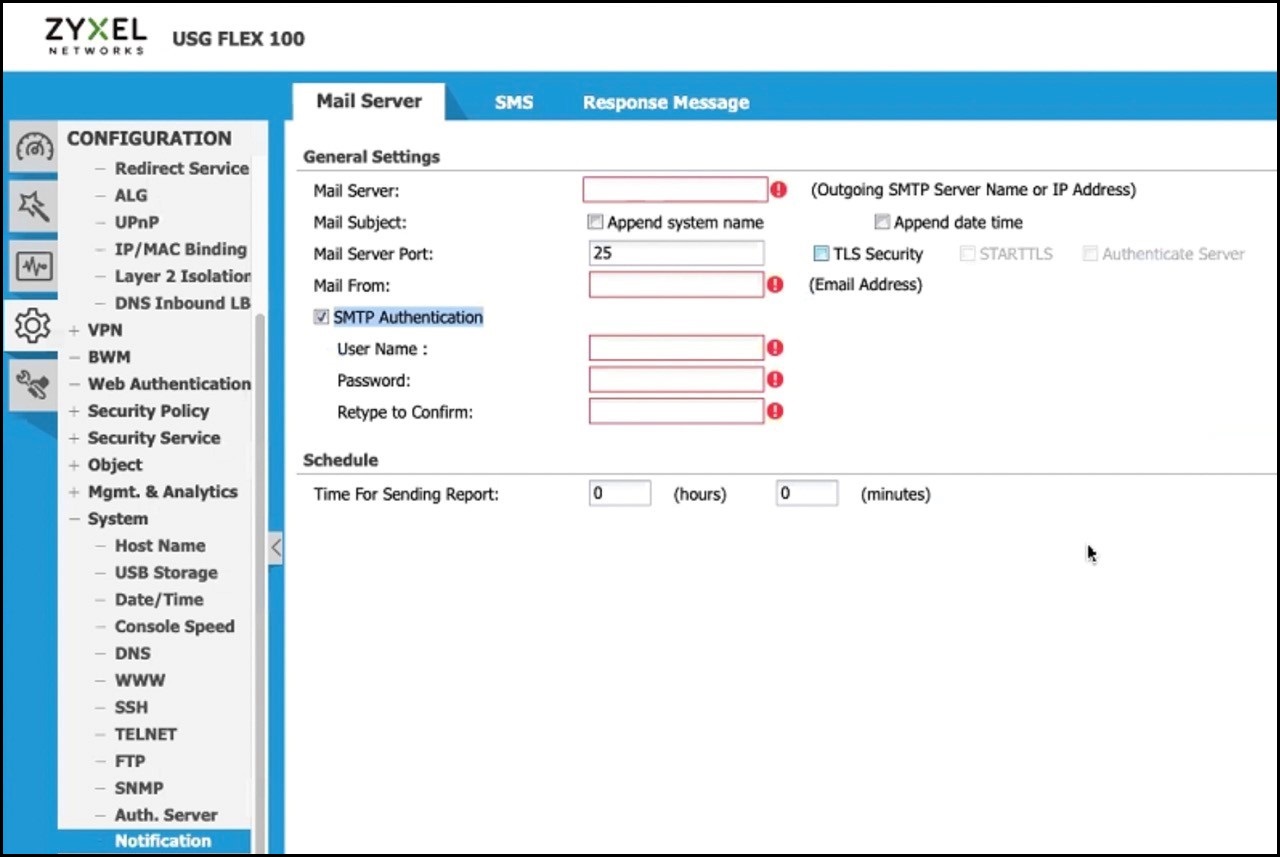
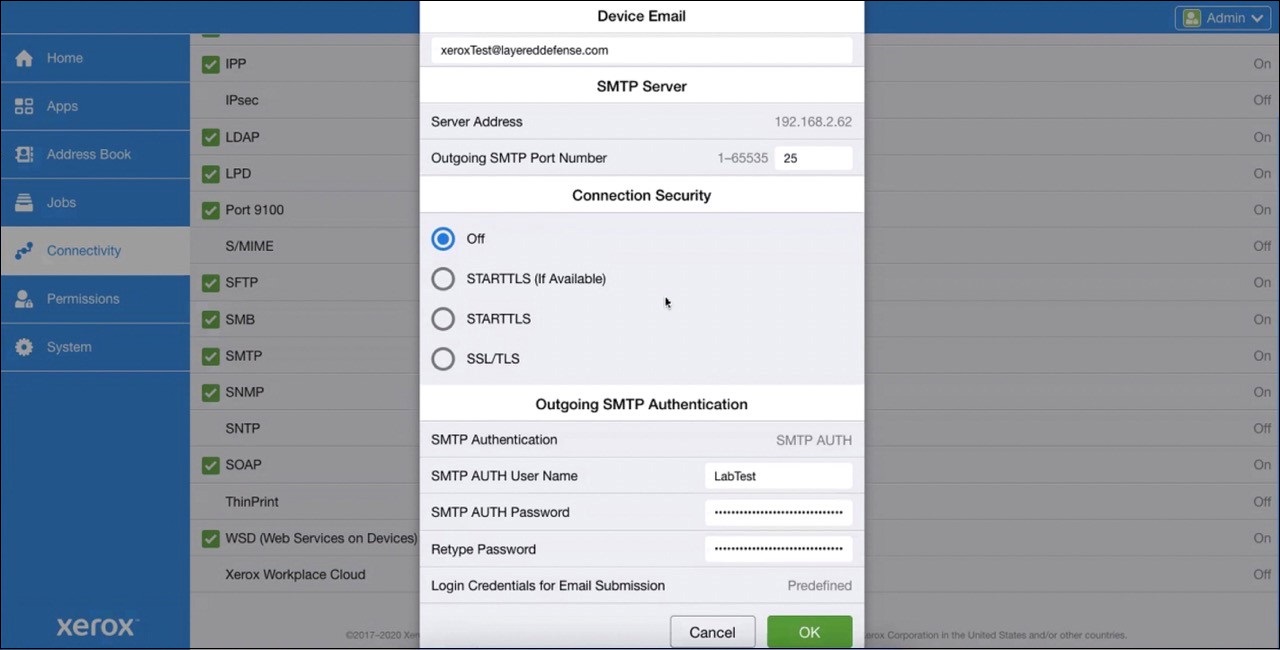
In one impromptu test, two out of three devices that Heiland checked – a Xerox enterprise printer and a Zyxel small-business firewall – turned out to only support SMTP AUTH, meaning they, like potentially millions of other devices installed around the world, are about to lose their ability to communicate with Google and Microsoft email servers.
Burning the bridge to an insecure past
With billions of email account details in wide circulation online and each one a potential way for cyber criminals to sneak into a company network, the change – which was announced in 2019 and has been progressively implemented across the industry – is designed to fight often automated credential stuffing attacks by transitioning users to OAuth 2.0, a newer global standard that uses application programming interfaces (APIs) to actively verify and authenticate users and devices for access to email and other services.
Systems administrators should check Internet routers, firewalls, and other devices to make sure they won't lose important alerting capabilities. Photo: Supplied
The “antiquated” SMTP AUTH method for signing into email, services, Google warns, “puts users at an additional risk since it requires sharing… credentials with third-party apps and devices that can make it easier for bad actors to gain unauthorised access to your account.”
If you use mobile apps or your desktop web browser to access services, you’re probably already using OAuth 2.0, which powers the now ubiquitous ‘Sign in with Google’, ‘Sign in with Apple’, and similar authentication services – all of which generate a unique ‘token’ that your computer or phone store and use to access your email and other services.
Support for OAuth 2.0 has become ubiquitous through software updates in mobile devices and desktop computers – but even the most security-conscious companies can easily forget that they are running dozens or hundreds of devices that may rely on SMTP AUTH to work, and are so old that they cannot support OAuth and will never be updated by their manufacturers to do so.
That means once SMTP AUTH is disabled, those devices will still work but won’t be able to email as they used to – although Heiland notes that enterprising systems administrators could extend their life by directing the devices to intermediary relay servers that support both old and new authentication methods.
“This will be a transition point that I think will catch people off guard in some cases,” he said, advising that “this would be a good time to bring in the IT people.”
“If you’re not paying attention to it, this could be disruptive for your organisation.”