2020 has seen a huge boost in cyber activity with security firm Crowdstrike finding the number of potential intrusions detected in just the first half of this year eclipsed the total for all of 2019.
Quick transitions to remote working have caused organisations around the world to add on new infrastructure, creating an “ever-increasing attack surface for motivated adversaries”
“Additionally, the pandemic created opportunities for adversaries to exploit public fear through the use of COVID-19-themed social engineering strategies,” the company said in a report released by its Overwatch analysis team.
Bad actors have used coronavirus as bait for phishing campaigns since at least March this year and the number of COVID-related scams has only risen with the Australian Cyber Security Centre finding, on average, two Australians were losing money or credentials to COVID scammers every day.
Recently, there has also been a lot of attention on state-sponsored bad actors looking to disrupt critical infrastructure or gather information for a database on prominent citizens, but the Crowdstrike data suggests that run-of-the-mill criminals tend to be the most common cyber threats.
“For each state-sponsored campaign uncovered by an OverWatch analyst, the team sees approximately four eCrime intrusions,” the report says.
“A likely explanation is that eCrime actors continue to achieve enormous success with ‘big game hunting’ campaigns, and the availability of commodity malware through ransomware-as-a-service (RaaS) models has contributed to a proliferation of activity from a wider array of eCrime actors.”
That RaaS business model means malware developers don’t have to do the attacking to benefit – instead they can sell their code or hire affiliates whose job it is to infect businesses with ransomware.
And there’s no doubt that ransomware is lucrative.
Fitness watch company Garmin reportedly used a third-party ransomware payment service to pay its attackers being locked out by the WastedLocker ransomware.
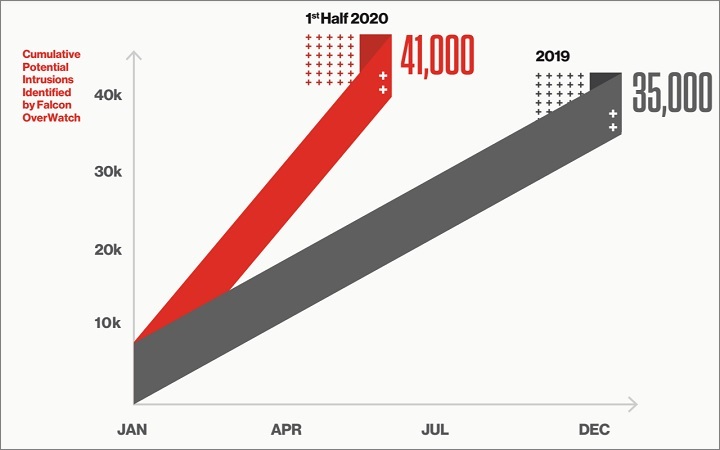
2020 has been a bumper year for cyber attacks. Source: Crowdstrike
Technology firms like Garmin have been the most targeted by cyber crooks this year, followed by companies in the manufacturing, telecommunications, and finance industries.
Naturally, travel industries have seen fewer attempted attacks.
VP of Crowdstrike’s OverWatch, Jennifer Ayers, said the shifting targets shows how bad actors are “ready to pivot to meet changing objectives or emerging opportunities”.
“Just like everything this year, the threat landscape has proven unpredictable and precarious as eCrime and state-sponsored actors have opportunistically taken aim at industries unable to escape the chaos of COVID-19, demonstrating clearly how cyber threat activity is intrinsically linked to global economic and geo-political forces,” Ayers said.
“Organisations must implement a layered defense system that incorporates basic security hygiene, endpoint detection and response, expert threat hunting, strong passwords and employee education to properly defend their environments.”
Yet as valuable as endpoint detection and threat hunting services may be, the Crowdstrike data once again shows that bad actors leverage valid credentials more than any other technique to gain access to a system, persist within it, and escalate privileges.
Unfortunately, Australians have been historically terrible at spotting credential-stealing phishing attacks with data from Proofpoint last year finding we were much more likely to fall for phishing attempts than our international counterparts.
And it can be an expensive mistake as Melbourne cosmetics company Heat found out last year when a ransomware attack cost it more than $2 million.










