Your smart home set-up contains a surprising vulnerability to laser pointers.
Researchers from the University of Michigan and Japan’s University of Electro-Communications have found a way to remotely control home speakers and smart phones using laser beams.
They tricked microphones commonly used in smart phones and home speakers into reading laser beams as though they were speech.
This was achieved by proportionally matching the frequency of the laser with the output of the microelectrical-mechanical system (MEMS) microphones.
By encoding voice recordings onto laser beams, the researchers were then able to mimic commands and control voice activated devices from long range.
“We show how an attacker can use light-injected voice commands to unlock the target’s smart-lock protected front door, open garage doors, shop on e-commerce websites at the target’s expense, or even locate, unlock and start various vehicles (eg Tesla and Ford) if the vehicles are connected to the target’s Google account,” the research paper says.
The failed devices
Seventeen popular devices were tested, including Google Home, Amazon Echo, Facebook Portal, plus a range of smart phones and tablets.
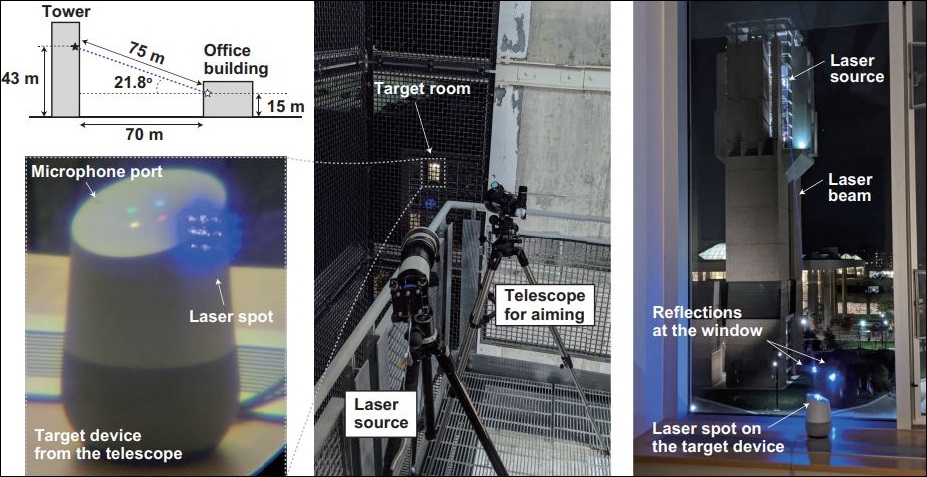
Using the full length of their research lab, the team tested its laser-hacking set-up at a distance of up to 110 metres.
They even took the laser and targeting telescope outside to a nearby building and fired down, at an angle, through a window into their lab, and gained control of a Google Home device.
“We note that despite its low 5 mW power and windy conditions the laser beam successfully injected the voice command while penetrating a closed double-pane glass window,” the paper says.
“We conclude that cross-building laser command injection is possible, at large distances and under realistic attack conditions.”
The attack on smart speakers was replicated outside of ideal lab conditions.
Home speakers were by far the most vulnerable to this attack vector, thanks in part to speaker authentication settings being turned off by default.
Even on devices with more prevalent speaker authentication – such as smart phones that are not typically used by multiple people – the researchers discovered that the recognition software used by Apple and Google only verified wake words (“Hey Siri”, “Okay Google”).
If that could be forged, or attackers obtained a recording of the user saying the commands, then the authentication could be easily bypassed.
Vroom, vroom
Alarmingly, other devices connected to Google accounts were accessible – including cars.
“Many modern cars have Internet-over-cellular connectivity, allowing their owners to perform certain operations via a dedicated app on their mobile devices,” the paper says.
“In some cases, this connectivity has further evolved (either by the vendor or by a third-party) in having the target’s car be connected to a [voice controlled] system, allowing voice unlocking and/or pre-heating (which often requires engine start).
“Thus, a compromised [voice controlled] system might be used by an attacker to gain access to the target’s car.”
The research team successfully locked and unlocked a Tesla Model S, as well as starting and stopping both the charging and climate control systems, all through the laser beam.
By opening the FordPass app, they got similar results with Ford cars, and were even able to start the engine remotely – although it cut out when trying to shift out of park.
Replicating results
Fortunately, building a smart-home hacking laser system is not exactly cheap or easy.
According to the researchers, “the laser current driver with analogue modulation port is the most specialised instrument in the attacker’s set-up], costing them around US$1,500. A cheaper driver would run up at least $US300.
Then there’s added cost of a laser pointer, amplifier, tripods, and telescope – not to mention the know-how needed to successfully deploy the equipment.
Prior to publishing their findings, the researchers shared their results with Google, Amazon, Apple, August, Ford, Tesla, and a major supplier of MEMS microphones.