Google has found a number of hacked websites containing malware that exploited an iPhone zero-day kernel vulnerability.
Known as a ‘watering hole attack’, infected websites were chosen because of their popularity with a specific group of people.
Any user unlucky enough to visit one of the sites had their iPhone implanted with spyware that could monitor their location, view the contents of encrypted messages, and even access saved passwords.
Ian Beer from Google’s security analyst team, Project Zero, said in an in-depth blog post that the attackers had full access to targeted iPhones for at least two years.
While analysing one of the exploit chains, Beer expressed surprise at the methods used by threat actors.
“It’s difficult to understand how this error could be introduced into a core IPC library that shipped to end users,” Beer said.
“While errors are common in software development, a serious one like this should have quickly been found by a unit test, code review or even fuzzing.
“It’s especially unfortunate as this location would naturally be one of the first ones an attacker would look.”
In the blog post, Beer shows the staggering level of access that attackers had on the implanted iPhone.
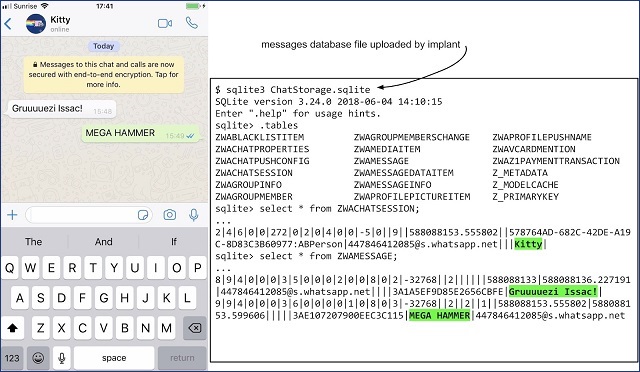
The implant could monitor end-to-end encrypted messages. Source: Google Project Zero
Passwords, messages, contacts, photos were all being sent from the implant, unencrypted, through HTTP.
“Everything is in the clear,” Beer said.
“If you're connected to an unencrypted WiFi network this information is being broadcast to everyone around you, to your network operator and any intermediate network hops to the command and control server.”
Apple patched the vulnerability in iOS update 12.1.4, removing the implant from affected phones.
Who built the watering hole?
Google did not announce which websites were infected with the malware, but said the affected sites received “thousands of visitors per week”.
Nor was there any indication about who might have operated this sophisticated and multi-layered surveillance attack.
Not long after the Project Zero blog post was online, TechCrunch and Forbes both reported that the watering hole attack had been targeting Uyghur Muslims – suggesting the involvement of Chinese state actors.
Damn, had this story last night and Zack scooped me. https://t.co/I0f3p1Z8Wa
— Thomas Brewster (@iblametom) September 1, 2019
Beer may have alluded to the surveillance of Uyghur Muslims in his post, saying that security protections – like those built by Apple – will not always protect users from deliberate attacks.
“To be targeted might mean simply being born in a certain geographic region or being part of a certain ethnic group,” Beer said.
“All that users can do is be conscious of the fact that mass exploitation still exists and behave accordingly; treating their mobile devices as both integral to their modern lives, yet also as devices which when compromised, can upload their every action into a database to potentially be used against them.”
China has been operating a widely condemned surveillance regime on the Uyghur-majority Chinese region of Xinjiang – to the extent of installing spyware on tourists’ phones.
Chinese surveillance technology research has been linked to Australian universities.










