Hackers are using fake job offers to deliver spyware in a spear phishing campaign tied to North Korean state actors, cybersecurity researchers have found.
The phishing emails contain job descriptions supposedly advertising positions in US defense and aerospace firms in order to lure workers in these industries to open malicious documents, found the McAfee Advanced Threat Research (ATR) team.
“Our analysis indicates that one of the purposes of the activity in 2020 was to install data gathering implants on victims’ machines,” the cybersecurity firm said in a blog post.
“These DLL implants were intended to gather basic information from the victims’ machines with the purpose of victim identification.
“The data collected from the target machine could be useful in classifying the value of the target.”
Posing as recruiters for military projects, the bad actors offer specific industry professionals jobs like system engineer for the F-22 fighter jet program.
In the email attachment is an innocuous-looking Word file which supposedly contains the job description but also gives the hackers a foothold in the target system.
Unlike the mass phishing attempts used by spreaders of malware like Emotet, the document in this instance is not used to trick its victims into enabling Word macros.
Rather, the malicious document – when opened – triggers the downloading of a macro-laden Word template from a remote server, meaning the Word document itself appears free of dodgy macros.
The McAfee ATR team calls this “template injection”.
“This is a clever technique we observe being used by multiple adversaries and is intended to make a document appear to be clean initially, only to subsequently load malware,” McAfee said.
“Some of these template files are renamed as JPEG files when hosted on a remote server to avoid any suspicion and bypass detection.
“These template files contain Visual Basic macro code, that will load a DLL implant onto the victim’s system.”
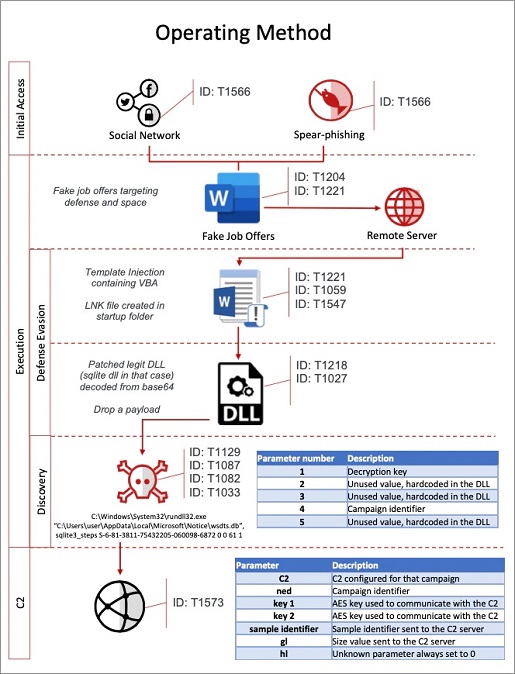
The method used by North Korean hackers to inject spyware in defense contractors. Source: McAfee
This DLL drop is also designed to avoid detection by being built from legitimate DLL libraries and only triggering its operation under specific circumstances.
After downloading yet another DLL, the malicious code begins communicating with a command and control server located on legitimate – but compromised – network infrastructure based in Europe or the US, exfiltrating information about the target machine.
The attackers avoid detection on this outgoing data by mimicking the User-Agent string pulled from the victim’s web browser settings.
Such a sophisticated and targeted campaign is clearly directed at the long-term surveillance of military information.
The Centre for Strategic and International Studies calls the breach of defense companies a “significant cyber incident”.
McAfee traced the techniques used in this spear phishing campaign with similar activity in 2017 and 2019 which was attributed to a hacking group called Hidden Cobra.
Also known as Lazarus, Kimuky, KONNI, and APT37, Hidden Cobra is a group tied to North Korean and was reportedly responsible for the devastating WannaCry ransomware and its sequel, Hoplight.
While its activities are less immediately destructive in this instance, Hidden Cobra could already have stolen military information pertinent to the strategic interests of North Korea – or it could be laying the groundwork for future campaigns against the vulnerable targets it has already infiltrated.
Along with appropriate endpoint security, McAfee recommends enterprises keep their staff informed of the threats from phishing campaigns that can successfully evade detection.
“The attackers leveraged spear-phishing with well-crafted lures that would be very difficult to detect initially by protective technology,” the cybersecurity company said.
“Well-trained and ready users, informed with the latest threat intelligence on adversary activity, are the first line of defense.”










