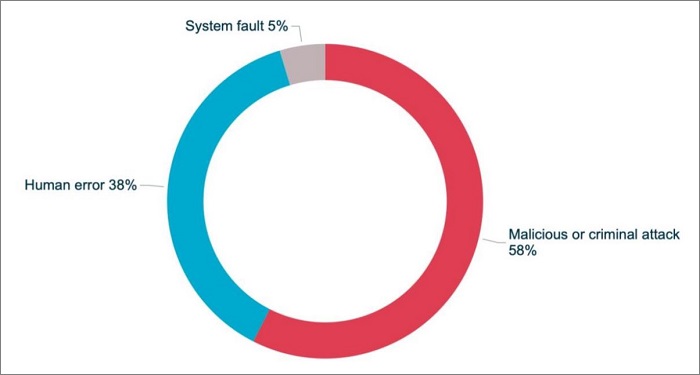
Australian organisations notified the Office of the Australian Information Commission (OAIC) of 539 data breaches in the last six months of 2020, bringing the yearly total to 1051.
Under the Notifiable Data Breaches scheme, organisations and government agencies that collect private data in Australia must notify the OAIC and affected people whenever a data breach occurs.
Of the 539 breaches occurring between July and December last year, the number of incidents caused by human error increased by nearly 20 per cent, according to the Notifiable Data Breaches report.
Data breaches caused by human error tend to be simple mistakes such as sending personal information to the wrong email recipient, unintentionally disclosing the information, or simply forgetting to use BCC in a mass email – as the Department of Foreign Affairs and Trade did when sending bulk communications to Australian travelers stuck overseas last October.
Privacy Commissioner Angelene Falk said the amount of breaches cause by human error was troubling.
"The human factor is also a dominant theme in many malicious or criminal attacks, which remain the leading source of breaches notified to my office," she said.
"Organisations need to reduce the risk of a data breach by addressing human error – for example, by prioritising training staff on secure information handling practices."
Despite the rising proportion of breaches attributed to human error, malicious or criminal activity are still the most common cause of data breaches in Australia, accounting for 58 per cent of incidents in the latter half of 2020.
Sources of data breaches across all sectors. Source: OAIC
Ransomware, malware, and other forms of hacking all featured but phishing was a dominate method for stealing credentials making up a full quarter of all cyber incidents leading to data breaches.
Gary Jackson, VP for APAC at Tenable agreed that the human element ought to be one of the first steps organisations go through to shore up their systems.
"By and large, the modus operandi for most cybercriminals – whether they be rogue actors or state-sponsored – is the path of least resistance: they’re getting in through the low hanging fruit," he said.
"Getting the basics right, addressing vulnerability patching diligently and implementing the right security control has now become critical because the criminals aren’t going anywhere."
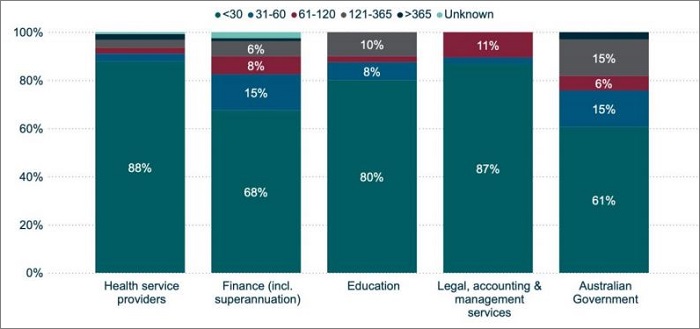
Days taken to identify breaches by top five industry sectors. Source: OAIC
While most breaches were uncovered and reported early, the OAIC said it "has seen significant variation" in the time taken to investigate then notify affected people of a breach.
"Unnecessarily delayednotifications undermine the NDB scheme by denying affected individuals the ability to take timely steps to protect themselves from harm," the OAIC said.
Of the top five industry sectors in the latest OAIC Notifiable Data Breaches report, health service providers and legal, accounting and management services had the best response times, identifying 88 and 87 per cent of breaches within thirty days respectively.
Australian government agencies fared the worst with only identifying 61 per cent breaches within 30 days.
Government agencies also had the highest proportion of breaches (15 per cent) found in the 121-365 day bracket.
CTO at Crowdstrike, Michael Sentonas, said identification and report time is a crucial factor in data breaches.
"When you are the victim of a data breach, the time it takes you to identify and respond to the attack is critical," he said.
"Whilst 78 per cent of entities notified the OAIC within 30 days of becoming aware of an incident that was subsequently assessed to be an eligible data breach, 23 entities took longer than 120 days after they became aware of an incident to notify the OAIC.”