Bad actors in a recent phishing campaign have left stolen credentials sitting on websites that were subsequently indexed and made searchable by Google.
The campaign, documented by cybersecurity firm Check Point in a blog post this month, saw hackers imitate email notifications for a Xerox photocopier.
Attached to the phishing emails was an HTML document which, when clicked, would send the user to a website with a pop-up that looked like the Microsoft authenticator on top of a blurred image of the supposed Xerox-scanned document.
The Javascript behind the phish prompted users to enter multiple passwords by telling them their password was incorrect before eventually redirecting the victim to a legitimate Microsoft site.
Interestingly, the hackers collected credentials in sites that remained visible on the public internet, despite their nefarious intentions.
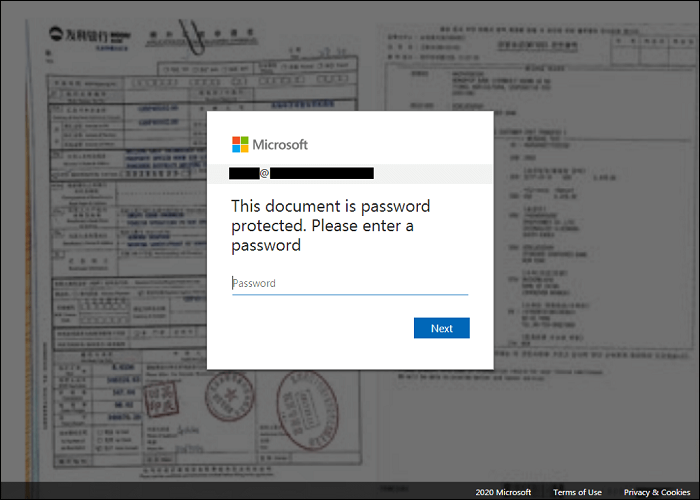
Be careful of phishing emails or your password could go public. Image: Check Point.
“We found that once the users’ information was sent to the drop-zone servers, the data was saved in a publicly visible file that was indexable by Google,” the Check Point researchers found.
“This allowed anyone access to the stolen email address credentials with a simple Google search.”
Using a mix of hijacked but otherwise reputable websites and their own infrastructure, the hackers were able to evade detection from standard security software that checks against known links used by bad actors.
The vast majority of commercial antivirus scanners and domain blacklisters partnering with the VirusTotal tool also neglected to pick up malicious code in the attachment.
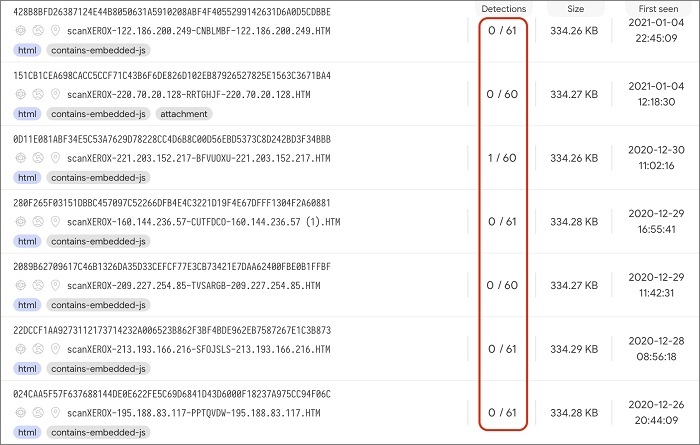
This phishing campaign was relatively undetected by antivirus software. image: Check Point.
Check Point even found spam emails sent from compromised accounts of legitimate German web hosting service, 1&1.
In order to avoid falling foul of would-be hackers, Check Point recommends you remain wary of lookalike domain names and spelling errors in emails, and to be careful when opening attachments.
“To protect yourself against this type of attack, be suspicious of any email or communication from a familiar brand or organization that asks you to click on a link or open an attached document.”










