Australians must be extra cautious about what messages they click on in coming weeks, after Australia Post’s three-day hiatus on package pickups created a new window for cybercriminals tweaking the Flubot ‘smishing’ attack to tap uncertainty around COVID test results, vaccines, and deliveries.
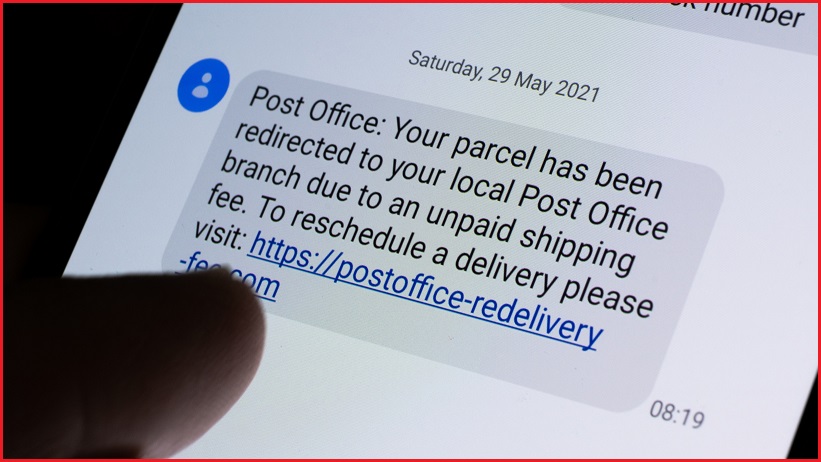
More than 5,500 Australians have told the ACCC Scamwatch service that they have received text messages created by the malware, which purports to be a notification about a new voicemail or package delivery and requests the recipient tap on a link for more details.
The messages typically include an ID number comprised of random letters and digits, as well as a link to an application that will install malware to steal sensitive data from the device.
They also typically include a number of obvious spelling mistakes, which are always a tell-tale sign that something fishy is going on.
Flubot is designed to compromise Android phones, and will attempt to download and install an application called ‘Voicemail71.apk’.
Once this application is installed, cybercriminals can read your text messages, send text messages from your phone, make phone calls from your number, and access your contacts. They may also be able to steal passwords and banking details.
With awareness about the fake-voicemail tactic increasing, in recent weeks Flubot’s creators have adapted its payload with a different approach that now pretends to be a delivery notification for an incoming package.
Messages provide a link promising updates about a “package outstanding in your name”, “your parcel with DHL”, promising to track an imminent delivery, or similar.
Australian mobile users have been flooded with the messages in recent weeks, after the malware was updated to use Australia’s +61 country code.
Telstra, for its part, is monitoring customers’ SMS usage for unusual surges in message volumes, and warned that it may suspend the SMS capabilities of customers that fail to remove smishing malware like Flubot from their phones.
Seizing the opportunity
The new approach coincides with Australia Post’s extraordinary decision to suspend parcel pickups from ecommerce companies between Saturday and Tuesday due to “record parcel volumes in parts of our network impacted by COVID-19”.
With nearly 500 Australia Post employees isolating on any given day and “parcel volumes as high as Christmas peak period”, the company said in a recent message to its business customers, the pandemic “is putting pressure on our network like nothing we have experienced before.”
The pause in parcel pickups will, the company said, help it “responsibly clear record volumes… to a safe and manageable level”.
With millions of Australians likely impacted by the delays that the pause will create, Australia Post’s move may well prime the market for a redoubled Flubot campaign promising updates on delayed parcels.
Australia Post is a perennial favourite target of cybercriminals, with so many scams leveraging its logo that the company maintains an index of new scams categorised by month.
Cybercriminals count on dovetailing with Australia Post’s already heavy reliance on SMS messages, with the company reporting in its latest annual report that it sent 230 million SMS messages to its customers – and 118 million packages – during the June 2020 quarter alone.
Australia post delivered 400 million packages during its last financial year, and is investing to increase its capacity to 700 million packages annually by 2025.
Flubot exploded in Australia during August following the malware’s overseas success this year.
The UK’s National Cyber Security Centre warned about an explosion in Flubot that saw millions of messages sent across Vodafone’s network alone.
The low cost and ease of access to SMS messages have made text messages a favoured channel for cybercriminal campaigns, with Australians this year losing $5.19 million in over 25,800 reported incidents, according to Scamwatch.
That made SMS the second most-used method for scammers this year, after phone calls (83,980 reports) and ahead of email (22,374) and internet (7,004).