The Emotet malware botnet is back online less than a year after a coordinated international police operation disrupted its operations.
Emotet uses an army of unsuspecting hacked machines to send a high volume of spam emails that contain malicious attachments.
Cyber security researcher Brad Duncan shared examples of the kind of emails currently being sent as part of the spam campaign now being conducted by Emotet’s new operators.
They have subjects like “Re: Missing Wallet” or “tax invoice” and encourage the potential victim to click on a Word or Excel document.
Once open, the document encourages the user to enable macros which it uses to download the Emotet malware that can take over a victim’s email threads to propagate itself or download secondary malware like the Trickbot banking trojan.
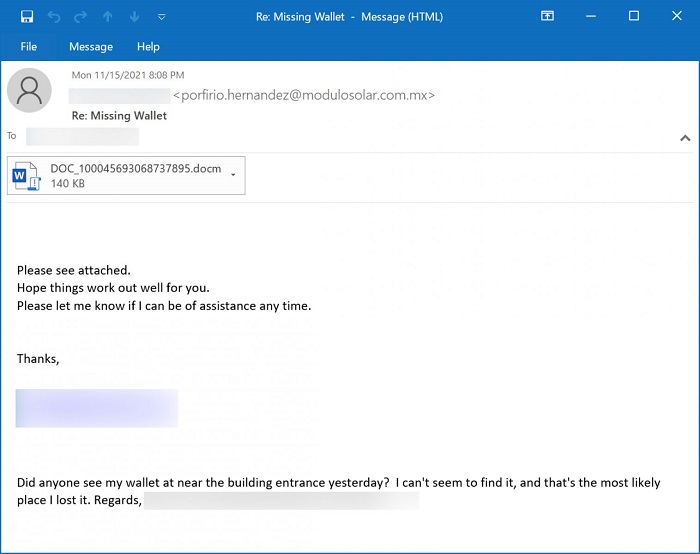
An example of the latest Emotet campaign. Image: Brad Duncan
Adam Meyers, Senior VP of Intelligence at cyber security firm CrowdStrike, confirmed the return of Emotet, adding that it was likely now being run by a group called Wizard Spider.
“Wizard Spider is a sophisticated eCrime group whose arsenal also includes malware such as Ryuk, Conti, and Cobalt Strike,” he said.
“The takeover of Emotet by Wizard Spider impressively shows how resilient the eCrime milieu has become now.”
Emotet’s return is a disappointing result for the international law enforcement effort that, in January, took down hundreds of servers being used to distribute and control the botnet.
That was only six months after a mysterious hacker hijacked Emotet’s payload, swapping it out with memes and animated gifs in what appeared to be a battle to control the malicious network of compromised machines.
Just did a conference call with some peeps tracking Emotet.
— Kevin Beaumont (@GossiTheDog) November 16, 2021
It’s back and retooled. Code and infrastructure has had updates, it is better secured now. It must be somebody/somebodies with access to original source code.
Will lead to more ransomware operators inside orgs shortly.
Emotet has also had some minor upgrades from its new operators which Sherrod DeGrippo, Vice President, Threat Research and Detection at Proofpoint, said included integration of two new file attachment types for malware delivery and changes to its API encryption.
“We continue to see thread hijacking, similar attachment names, and the use of Word documents and password-protected ZIP files in delivery as previously observed,” she said.
“A number of the files’ names look legitimate and the payload URLs are still distributed in sets of seven, along with the same Botnet ID generation to name a few.
“Emotet has consistently been one of the largest volume threats on the internet for years. This return is significant for the threat landscape and represents a significant threat to organisations’ security posture.”
A previous advisory about Emotet from the Australian Cyber Security Centre (ACSC) recommended a series of mitigation actions including the review of Microsoft Office macros, patching operating systems, scanning emails, and segmenting networks.










