Leaders of a prominent ransomware group have told their affiliates that hospitals and nuclear power plants are no longer off limits after a consortium of international law enforcement agencies – including the Australian Federal Police – hacked the group, stole its decryption keys, and attempted to take its dark web sites offline.
The group, known as Blackcat or ALPHV, has been terrorising businesses and governments with ransomware for the best part of 18 months.
According to an advisory from US intelligence agencies this week, ALPHV/Blackcat had encrypted the IT systems of over 1,000 organisations and received around US$300 million in payments since its first appearance.
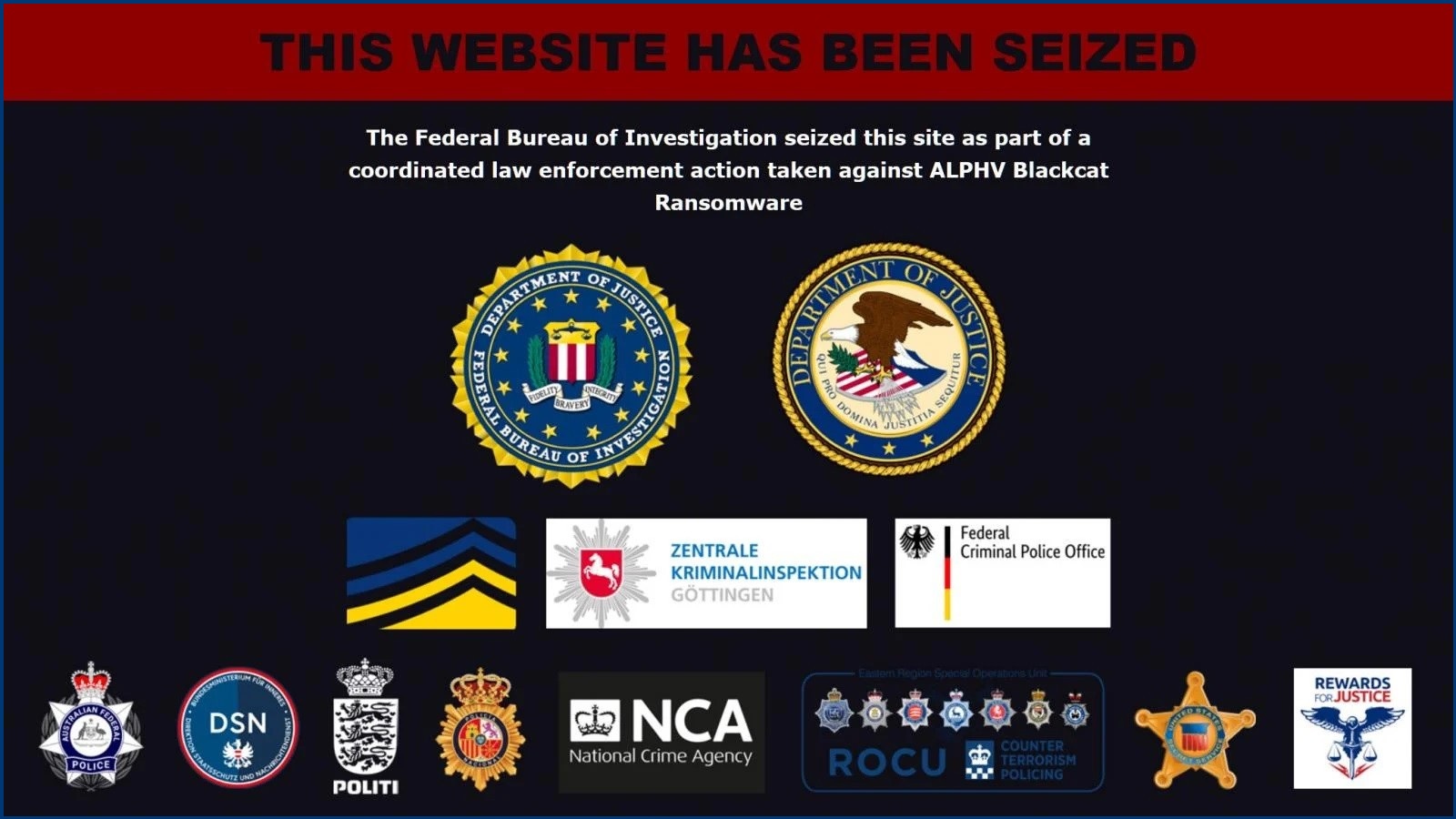
On Wednesday, a US Federal Bureau of Investigations (FBI) led operation to disrupt ALPHV/Blackcat hit a tipping point when the ransomware gang’s dark web leak site – a somewhat public repository for stolen data that criminals use to threaten and extort their victims – appeared with a splash message saying it had been seized.
In a press release, the FBI boasted that it had hacked into Blackcat’s computer network and taken some of the group’s decryption keys which it was handing out to victims.
The Australian Federal Police said it had worked with the FBI and was distributing decryption keys to local victims of this particular ransomware group.
“We have so far identified 56 Australian-based victims across both corporate and government sectors and we are engaging with victims to provide decryption keys to restore their systems where we can,” AFP Cyber Command assistant commissioner Scott Lee said in a statement.
Real estate agent LJ Hooker, law firm HWL Ebsworth, and a slew of other Victorian businesses are among the publicly known Australian victims of ALPHV.
Disrupting the business model
Ransomware groups like Blackcat tend to operate using a distributed business model that sees different people running the business (by laundering ill-gotten cryptocurrency and communicating with victims), developing the ransomware, and delivering the final payload.
Typically, the attack on a business is done by an affiliate – a kind of hacker mercenary who breaks into a network and drops the ransomware, receiving a cut of any money that was extorted by the rest of the criminal enterprise.
Unsealed US court documents describe how FBI agents posed as potential affiliates to see how the backend of Blackcat’s Tor site worked.
Then, they managed to get hold of “946 public/private key pairs for Tor sites” used by Blackcat – though the FBI didn’t explain how – which they used to steal decryption keys and take the ransomware group offline, for a short while at least.
Within a few hours, the ALPHV/Blackcat Tor site had changed again with a new splash page saying the website had “been unseized”.
An attached message said, in Russian, that the FBI had compromised one of the group’s data centres and speculated that one of its hosts had “maybe even” helped law enforcement gain control over the network.
“The maximum that they have is the [decryption] keys for the last month and a half,” Blackhat said according to a machine translation posted by Bleeping Computer.
“It’s about 400 companies, but now more than 3,000 companies will never receive their keys because of them.”
Blackcat then sent a chilling message to its affiliates that the business was changing as a result of the FBI’s actions – removing apparent restrictions that the leaders placed on its freelance hackers.
“We are introducing new rules, or rather removing all the rules except one,” the message said. “You cannot touch the CIS [the Commonwealth of Independent States, a bloc of former Soviet states led by Russia].
“You can now block hospitals, nuclear power plants, anything and anywhere.”
The group also posted a link to a new leak site.
Information Age can confirm the new site appears operational and includes mention of three new victims in blog posts dated after the FBI’s site seizure.
Reports indicate that other ransomware groups have sprung into action following Blackcat’s disruption, with the likes of Lockbit openly trying to get affiliates to jump ship.
Blackcat said it has upped the revenue for affiliates to 90 per cent of the ransom payment in a bid to keep its hackers on-side.