The ransomware gang behind a string of cyber attacks affecting the likes of Rio Tinto and the Tasmanian government has leaked more data onto the dark web – this time impacting Crown Resorts.
Last week, Australia's largest gaming and entertainment group Crown Resorts revealed it was investigating a potential data breach stemming from a third-party incident at the file transfer service GoAnywhere.
According to a Crown Resorts spokesperson, the company was contacted by a ransomware group which claimed to have “illegally obtained a limited number of Crown files”.
Now, after a week of near-silence from the gambling conglomerate, a collection of highly sensitive data may have been dumped onto a dark web blog.
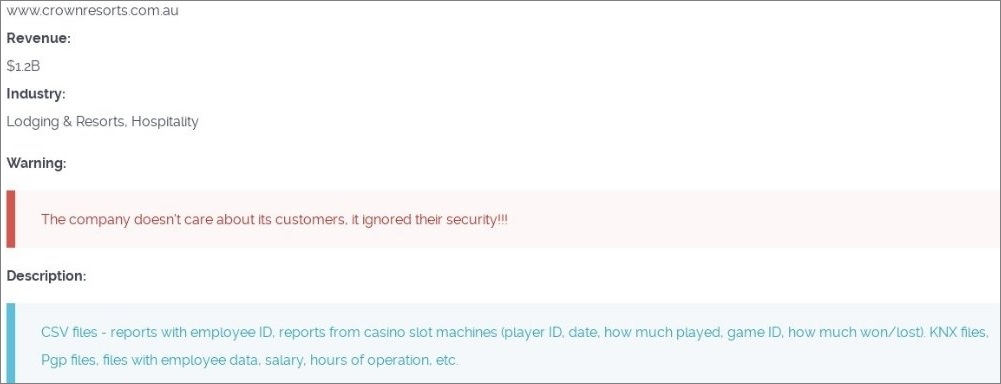
Ransom gang Cl0p's dark web blog displayed a sample of data said to include employee salary information and reports from casino slot machines.
According to the post, the allegedly stolen data contains information on “how much played” and “how much won/lost” from casino slot machines – the post also mentioned “player ID” values, though it is unclear whether any players are actually identifiable.
Furthermore, the Russia-linked hacker group claims to have stolen and leaked some highly sensitive security files from the gaming and entertainment giant – those being KNX files, which are typically used in commercial building automation to manage things like lighting, air conditioning, energy management and security systems; and PGP files, which are widely used for encryption and authentication purposes.
The dark web post surfaced some time between Tuesday and Wednesday, alongside a caption from Cl0p reading “the company doesn't care about its customers, it ignored their security!!!”
While a Crown Resorts spokesperson initially reported no customer data had been compromised, the company released an update on Wednesday confirming some files have been released on the dark web.
“Today we can confirm that a small number of files have been released on the dark web, including employee time and attendance records and some membership numbers from Crown Sydney,” a spokesperson said.
“We can confirm that no personal information of customers has been compromised as part of this breach.
“We are proactively notifying all impacted individuals and are updating membership numbers of those affected out of an abundance of caution.”
Crown Resorts has not responded to Information Age’s request for comment.
A screenshot of the Cl0p blog post. Image: Twitter/@Cyberknow20
Cl0p's recent attacks stem from a zero-day vulnerability (CVE-2023-0669) found in file transfer software GoAnywhere.
While the vulnerability was eventually patched on 7 February, the Cl0p group claims it has stolen data from more than 130 organisations – including mining giant Rio Tinto and the Tasmanian government – after exploiting the bug.
Cl0p's spree of attacks has been likened to mass ransomware events such as the notorious 2021 Kaseya hack which impacted around 1,500 organisations, and has already been labelled one of the largest cyber security events of the year.
Tasmanian government says bank account details at risk
The Tasmanian government, which relies on GoAnywhere as a third-party file transfer service, has discovered sensitive financial data including names, addresses, invoices and bank account numbers may have been accessed in a developing cyber security breach.
For over a week, the Tasmanian government has been investigating a security incident which may have resulted in the loss of government-held data.
On Monday, Technology Minister Madeleine Ogilvie indicated no government-held data appeared to have been compromised in Cl0p's hack of the third-party service.
In an update on Wednesday, however, Ogilvie said investigations had found a risk that financial data held by the Department for Education, Children and Young People had been accessed.
“I understand reports such as this may cause concern in the community,” she said.
“That's why we will continue to keep the Tasmanian community updated and advise where support can be accessed.”
Ogilvie stressed there was “no confirmation” that the information had been stolen, and further emphasised “no Tasmanian government IT systems have been hacked”.
She also advised Tasmanians to regularly check their bank accounts, and pointed those with potential concerns to their financial provider or the Australian Cyber Security Centre, which is now handling the ongoing investigation.
Cl0p's dark web blog currently reads “Coming soon…” under a listing for the Tasmanian government.










