More than 4 million browsers have been infected by a China-based threat actor that published browser extension apps as a front to distribute malware.
Researchers at Koi Security found a China-based threat actor, dubbed “ShadyPanda”, managed to deploy and successfully market a range of browser extensions to an audience of at least 4.3 million users across Google Chrome and Microsoft Edge.
After attracting users to a range of seemingly legitimate extensions – including widget app ‘WeTab’ and cache clearing extension ‘Clean Master’ – the threat actor gradually rolled out automatic updates which contained a strain of malicious spyware that could track users’ browsing habits.
As of 1 December, Koi found at least five extensions with four million users were still “actively collecting every URL visited, search query and mouse click”, then transmitting the data to servers based in China.
“Some of ShadyPanda's extensions were featured and verified by Google, granting instant trust and massive distribution,” wrote Koi researcher Tuval Admoni.
“For seven years, this actor learned how to weaponise browser marketplaces – building trust, accumulating users, and striking through silent updates.”
The long game
In what Koi described as a “seven-year malware campaign”, ShadyPanda’s exploits were traced back to 2018 when the group published the first of five seemingly legitimate browser extensions.
Offering internet speed tests and other productivity features, these extensions worked as advertised for years – no spyware included.
“The strategy: build trust, accumulate users, then weaponise via a single update,” wrote Admoni.
The threat actor advertised its spyware as legitimate extensions. Source: Information Age
By mid-2024, when the extensions had accumulated some 300,000 installs, ShadyPanda used Chrome and Edge’s automatic update mechanisms to push out an identical strain of malware across the apps.
From there, ShadyPanda benefited from full access to browser application programming interfaces (APIs) and a virus which could continuously receive and execute new instructions by the hour.
Koi explained the malware’s most common activity was monitoring “every website visit” and exfiltrating encrypted browsing history to servers based in China – effectively constituting “complete browser surveillance” for anyone running the extensions.
Considering the level of access ShadyPanda had acquired, Admoni warned the extensions’ behaviour could easily evolve over time.
“This isn't malware with a fixed function. It's a backdoor,” said Admoni.
“ShadyPanda decides what it does.”
“Today it's surveillance, tomorrow it could be ransomware, credential theft, or corporate espionage.”
Huge payload in Microsoft Edge
According to Koi, ShadyPanda’s seven-year campaign was just the beginning of its exploits.
In 2023, the collective pulled off a sizable “affiliate fraud” where 145 supposed wallpaper and productivity browser extensions were used to inject affiliate tracking codes into purchases at eBay, Amazon and Booking.com.
After scoring hidden commissions on an untold number of purchases through this scheme, ShadyPanda went on to deploy a browser-hijacking tool under the guise of a productivity app in early 2024.
Though lucrative, both these schemes saw ShadyPanda’s extensions frequently reported and taken down within months of being released.
The threat actor ultimately found their stride after five other malicious extensions – including its flagship WeTab tool – achieved mass popularity in Edge.
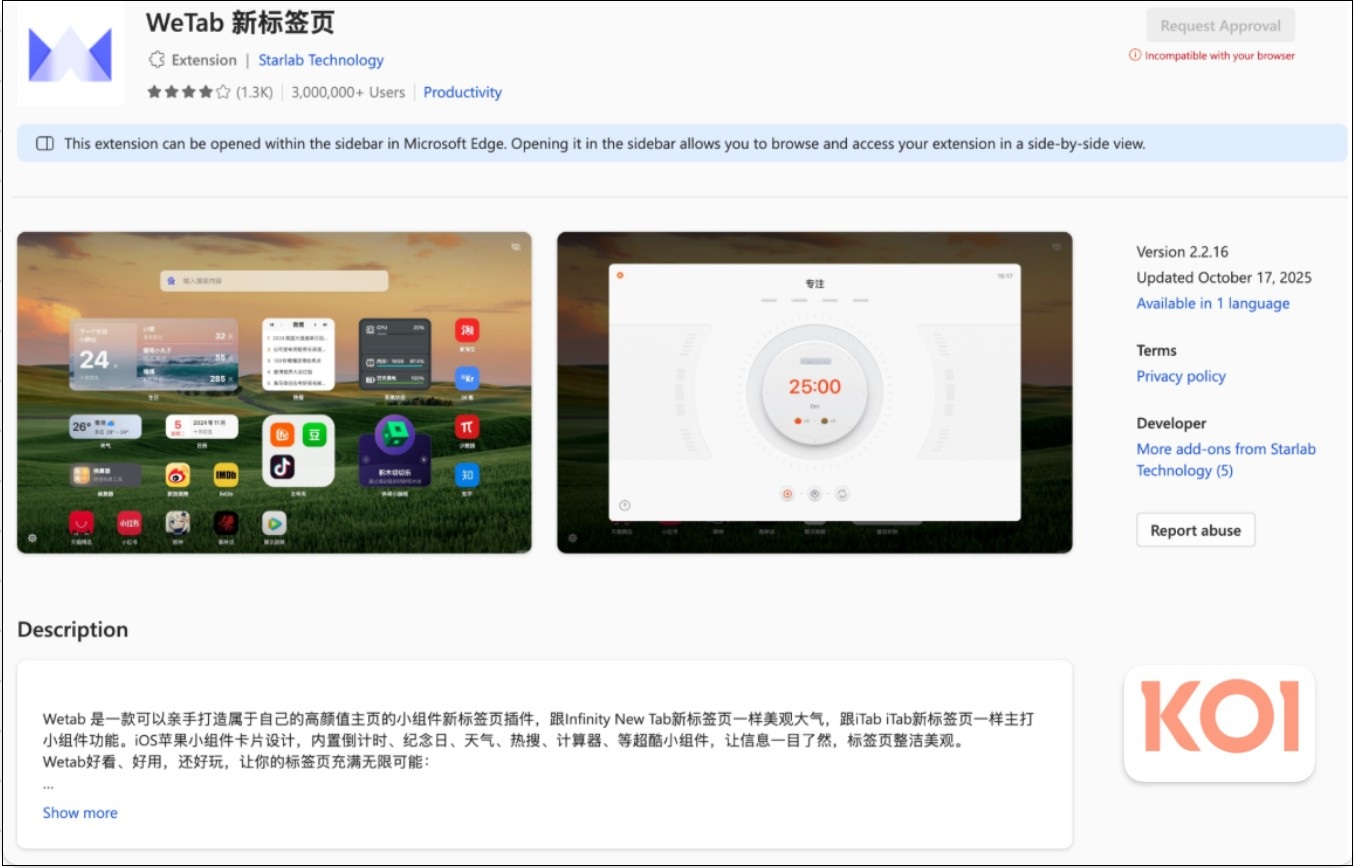
WeTab and its spyware achieved 3 million downloads alone. Source: Koi
Launched in 2023, the five extensions accrued more than four million installs by December 2025.
Koi described WeTab – the most popular of the apps – as “comprehensive” spyware that collected and exfiltrated user data to 15 servers in China.
Among the pilfered data was every URL visited by users, keystroke-level monitoring of search queries, “pixel-level” mouse-click tracking, and detailed page interaction data (such as time spent on a page and user scrolling behaviour).
Notably, Koi found WeTab and its sibling apps were still active on Edge’s extension marketplace at the start of December.
Information Age understands ShadyPanda’s extensions have since been removed from Edge, though WeTab is still available on Chrome at the time of writing.
Despite Koi providing examples of the spyware in action, the publishers of WeTab have openly disputed the findings.
“We conducted multiple rounds of internal security self-checks on [WeTab] and found no remote code execution backdoors or malicious behaviour as described in the security report, nor did we execute arbitrary third-party scripts without the user's knowledge,” read a translation of WeTab’s statement.










