EXCLUSIVE: User accounts from over 60 Australian businesses are being itemised and sold for less than a dollar on fraudulent marketplaces across Discord, Telegram and the web.
Information Age has encountered two online criminal shopfronts where customers can buy access to stolen accounts at popular Australian franchises, including event ticket resale company Tixel, tools retailer Total Tools, cinema chain Hoyts and more.
In many cases, customers are simply looking to steal the benefits of someone else’s account – whether cashing in on a free drink promotion from Boost Juice or hijacking concert tickets purchased through Ticketek.
Thieves also use the account’s store credits or attached payment details to go on illicit shopping sprees.
For example, one of the illicit shopfronts offers unfettered access to stolen accounts on ‘Buy Now, Pay Later’ platform Payright, where buyers can run up thousands of dollars in debt for a buy-in as low as $20.
Food, retail and streaming accounts typically sell for less, with buyers able to quietly roost in Stan or Disney+ accounts for a one-time fee of between $2.50 and $5.50.
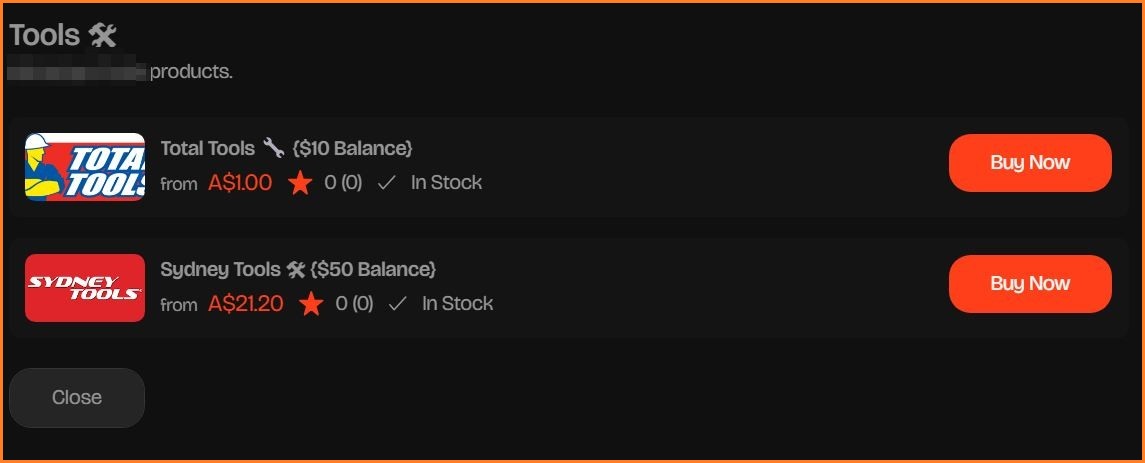
Fraudsters sell user accounts for Aussie brands. Image: Supplied
Speaking with Information Age, researchers at Sydney-based cybersecurity company Saltt Technologies say those responsible for the racket typically target businesses which have a “key exploit driver”, such as offering “loyalty points, stored balances, cash out options and stored payment methods, including credit cards”.
According to Saltt cybersecurity consultant Daniel Farynski, the scheme relies on credential stuffing attacks: a brute-force method where stolen login details are checked against multiple platforms to catch users who recycle their username and password between accounts.
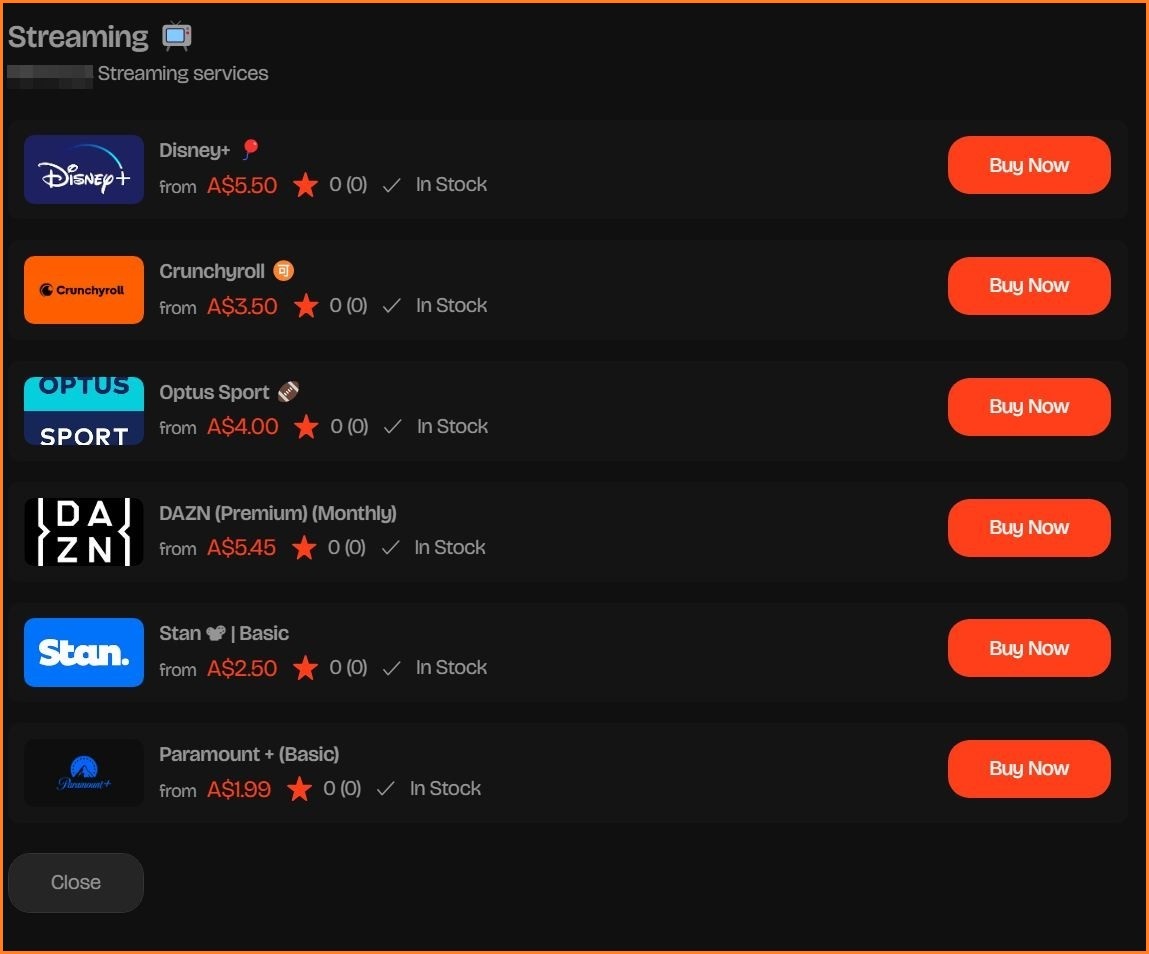
Why pay for streaming when you can steal it? Image: Supplied
“They then categorise user accounts by value, listing the username, email and password on their marketplace,” Farynski says.
“Accounts subsequently get purchased, sometimes for less than a dollar, then fraudulently used in various ways, including the use of the victim’s attached payment method.”
Account traffickers run up purchases
On social platform Discord, fraudsters run a dedicated channel where nearly 800 members can find shop updates, receive limited-time discounts, and collect temporary codes to validate orders on stolen Uber Eats accounts.
Information Age viewed this channel and found dozens of users openly celebrating their fraudulent wins.
One user screenshots a stolen Reading Cinemas account with about 10 cinema tickets worth of credits, another shares a picture of some newly unboxed shoes from shopping platform Ozsale, while shoppers regularly post photographs of drinks from tea franchise Chatime.

A group of three cheer over some stolen Boost Juice. Image: Supplied
The purchases aren’t just limited to drinks, clothes and movie tickets – after buying login details for experiences and gifts company Red Balloon, two account traffickers posts images of seemingly expensive steak dinners while another films a hiking trip booked with a stolen voucher.
Indeed, those running the Discord store boast “we can get you in” to any concert or event on Australia’s largest ticketing platforms, including Moshtix, Ticketek and Megatix.
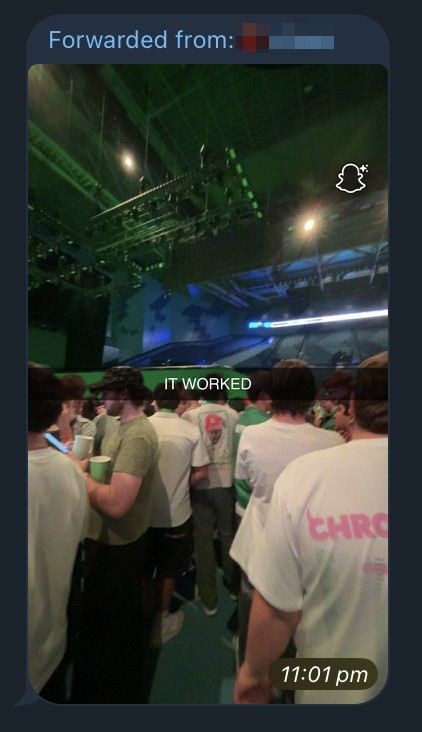
Concert goers enjoy someone else’s Tyler the Creator tickets. Image: Supplied
According to Farynski, buyers have also targeted a small number of “financial businesses” which offer a “cash out option” of stored balances.
‘100% Aussie-based’ fraud
Not only are the majority of impacted businesses based in Australia, but the websites claim to be “100% Aussie-based” and “tailored for Aussies”.
“We’re proudly based in Australia, giving us the local edge to deliver exactly what you want — and need,” reads one of the fraud websites.
Despite selling stolen services and facilitating fraud, the websites mimic legitimate online shopfronts by adopting terms of service, customer reviews, and FAQ pages.
Fraud site boasts round-the-clock support. Image: Supplied
Farynski says the stores maintain this facade to prevent their Discord server from being taken down by user reports.
Such takedowns have repeatedly resulted in the threat actors “losing all their chats and members”, though nearly 560 people follow the markets on messaging app Telegram to stay up-to-date on any outages.
Accounts handballed since 2023
Farynski says the credential stuffing attacks started as early as 2023 when customers started to notice unsolicited transactions at the likes of Boost Juice, liquor store Dan Murphy’s, and fashion website The Iconic.
While conducting an incident response for a client in early 2025, Saltt found over 60 Australian businesses were being actively exploited.
Given the marketplaces rely on stolen login credentials, Farynski says most attacks can be prevented through multi-factor authentication.
But despite reaching out to those breached, many victim businesses have instead opted to “brush it under the rug”.
“Approximately 20 per cent of businesses that were informed took action, with the vast majority of businesses opting to ignore emails despite their legal obligation to notify the Office of the Australian Information Commissioner (OAIC) under the Notifiable Data Breaches (NDB) scheme,” says Farynski.
Ownership of the marketplaces appears to have switched hands “at least a few times”, with most involved demonstrating “relatively low” cybersecurity maturity.
Indeed, Information Age found multiple buyers on Discord use identifiable profile pictures or are otherwise traceable to public profiles on gaming platforms, while Saltt determined a former marketplace owner was based in Sydney after finding their pseudonym was clumsily linked to a personal social media account.
“The entry barrier to performing these attacks and subsequently selling the compromised user accounts is very low,” Farynski says.
“This attracts many low-level threat actors to attempt exploitation across various targets, namely, Australian businesses.”










