The Australian cybersecurity expert behind Have I Been Pwned — a prominent website used to track information leaked in data breaches — says he has fallen for a “very well-crafted" phishing scam which has leaked thousands of email addresses and some location data.
Troy Hunt, who created Have I Been Pwned in 2013, revealed on Tuesday that an attacker had gained access to his account with email marketing platform Mailchimp and stolen details of around 16,000 current and former subscribers to his blog.
Hunt said the attack began when he received an email purportedly from Mailchimp which claimed his account’s email sending privileges had been “restricted due to a spam complaint” and he needed to review his account to regain access.
He said he had received “a gazillion similar phishes before” which he managed to fend off, but added “tiredness was a major factor” why this one successfully convinced him to log into what he thought was Mailchimp's website, thereby sharing his login credentials and a two-factor authentication code.
“You know when you're really jet lagged and really tired and the cogs in your head are just moving that little bit too slow?” Hunt wrote of the incident on his website.
“That's me right now, and the penny has just dropped that a Mailchimp phish has grabbed my credentials, logged into my account and exported the mailing list for this blog," he added.
“… I wasn't alert enough, and I didn't properly think through what I was doing.
“The attacker had no way of knowing that (I don't have any reason to suspect this was targeted specifically at me), but we all have moments of weakness and if the phish times just perfectly with that, well, here we are.”
Email triggered ‘just the right amount of urgency’
Hunt said the phishing email he received was convincing because it “created just the right amount of urgency without being over the top”.
“It socially engineered me into believing I wouldn't be able to send out my newsletter so it triggered ‘fear’, but it wasn't all bells and whistles about something terrible happening if I didn't take immediate action,” he said.
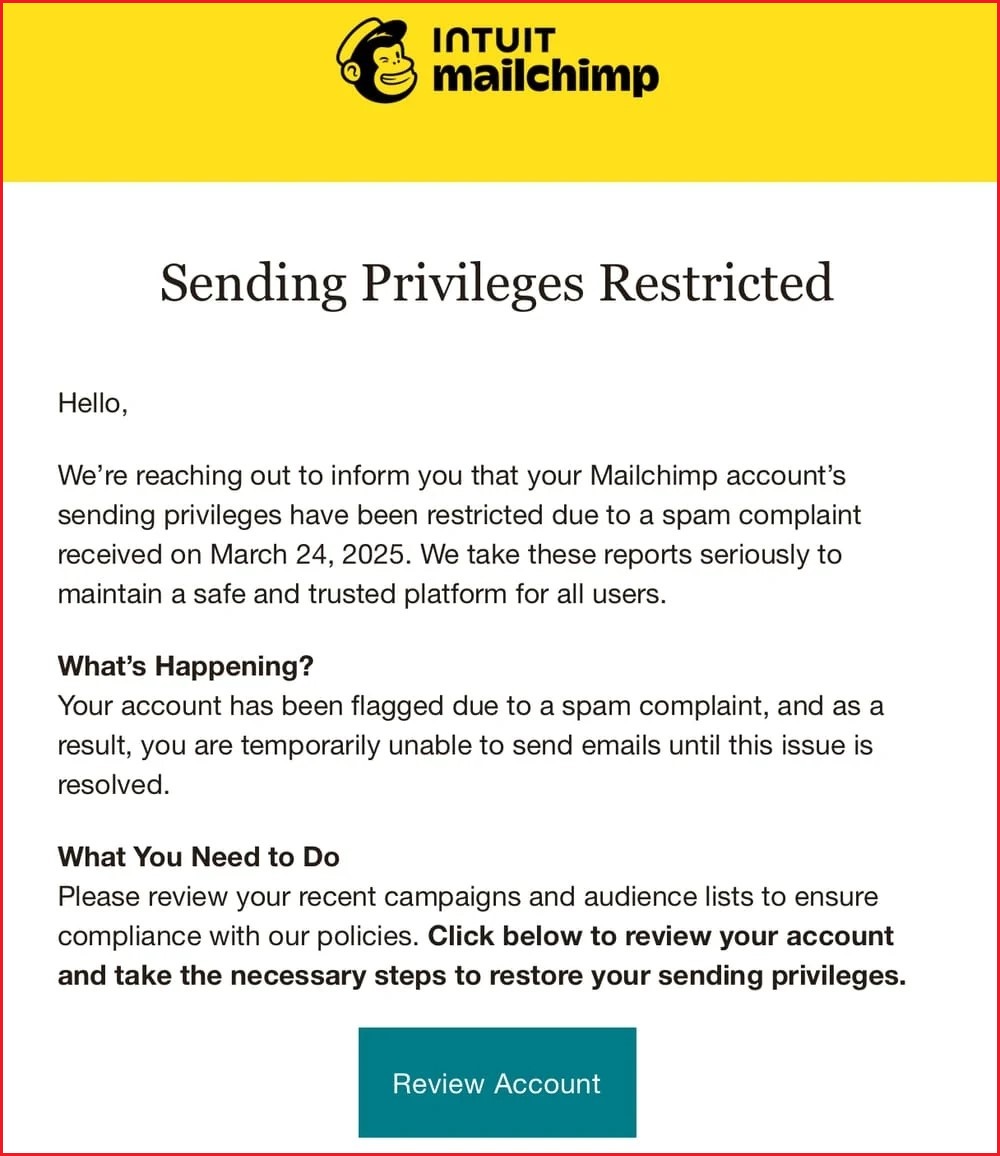
The phishing email Troy Hunt said he received, which claimed it was sent by Mailchimp. Image: Troy Hunt
Hunt expressed disappointment that Mailchimp’s system did not automatically delete from its system the email addresses of people who had unsubscribed, which he said made up more than 7,500 of the leaked addresses.
The leaked data also contained some “rough” geolocation data and IP addresses, Hunt added.
He said his experience had highlighted the value of passkeys — an emerging security protocol which uses biometrics and is designed to be phishing resistant.
Hunt said he decided to be “transparent and expeditious” in reporting his experience publicly because this was the advice he provided when working with companies which had been breached.
Mailchimp was contacted for comment.
‘Absolutely anyone can fall victim’
Paul Haskell-Dowland, a cybersecurity professor at Edith Cowan University and a member of the ACS Cyber Security Committee, said Hunt’s experience showed “absolutely anyone can fall victim to scams and phishing attempts, regardless of age, education, or experience”.
Phishing campaigns could simultaneously target millions of people and there would always be some individuals with “personal circumstances that make them more vulnerable at that moment in time”, Haskell-Dowland added.
“No one is immune and everyone is a potential target,” he told Information Age.
Unexpected emails which demanded action be taken should be met with cautious consideration, Haskell-Dowland said.
“If the email is for a service that you recognise and that you actually use, go directly to the service provider's website,” he said.
“Clicking on links in emails is, as we know, potentially dangerous.
“There are so many ways to hide the real destination and emails can be spoofed very easily.”
Haskell-Dowland argued most people are likely to fall victim to a scam “at some point” in their life, so should not feel ashamed when it happened.
"It happens every day, to every type of person,” he said.
This is too many levels of meta for my head to grasp 🤯 pic.twitter.com/Pr0iFQGNlh
— Troy Hunt (@troyhunt) March 25, 2025
‘Massive spike’ in phishing-as-a-service
As demand for paid cybercrime services grows on the dark web, cybersecurity companies have also reported a rise in phishing-as-a-service (PhaaS) attacks.
US cybersecurity firm Barracuda Networks said it had witnessed “a massive spike” in such attacks, with more than 1 million recorded by its systems in the first two months of 2025.
“The platforms that power phishing-as-a-service are increasingly complex and evasive, making phishing attacks both harder for traditional security tools to detect and more powerful in terms of the damage they can do,” the company said last week.
British cybersecurity firm Darktrace said it detected a phishing attack roughly once every second in 2024, and had witnessed an increase in threat actors targeting third-party services such as Mailchimp.
The company said around a third of the attacks it detected in 2024 used “novel social engineering techniques like QR codes and AI-generated text”.
Tony Jarvis, Darktrace's chief information security officer for the Asia-Pacific, said organisations needed to understand that while AI could bolster cyber defences, it was also being used to “supercharge the abilities of threat actors to deliver highly-sophisticated attacks at unprecedented speed and scale”.
“That means humans can no longer be relied on as the last line of defence,” he said.










