EXCLUSIVE
Sydney-based agency Wendy Wu Tours has been given seven days to negotiate with a criminal ransomware gang which claimed to have breached the company and published stolen Australian passports.
The established touring company has operated in Australia for some 25 years and flies “thousands of travellers” to Asia every year.
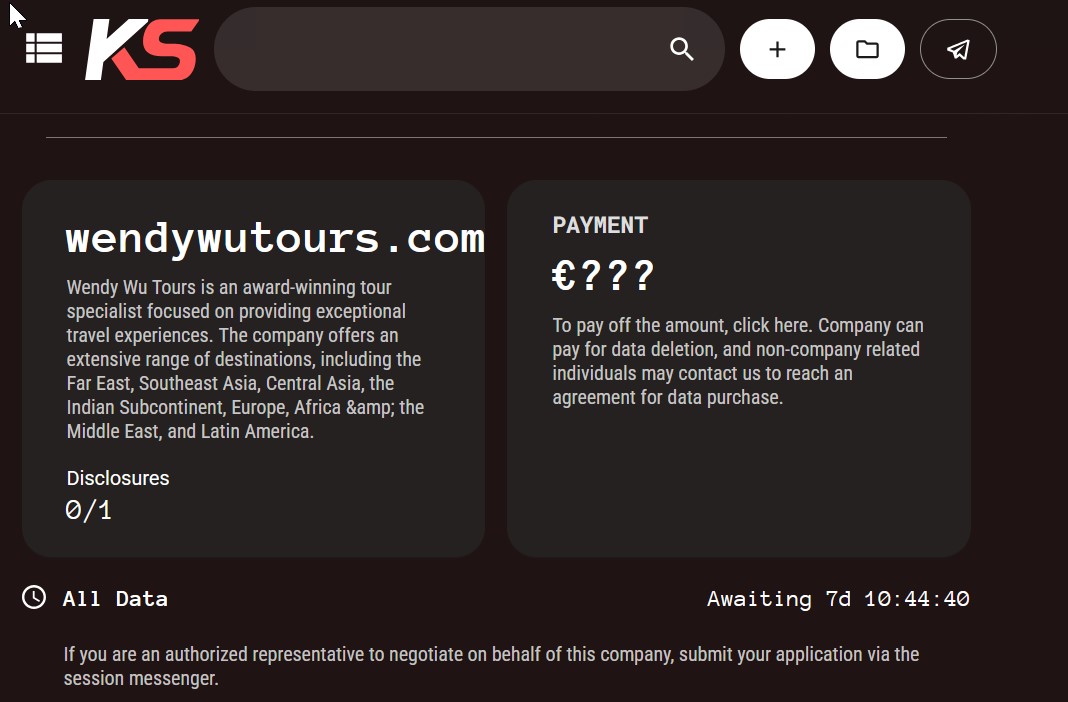
On Tuesday night, threat actor KillSec posted a data breach listing for Wendy Wu Australia on its dark web site, demanding a ransom negotiation for an undisclosed amount of data it claimed to have stolen from the company.
Wendy Wu Tours has not verified KillSec’s claim, though Information Age observed a sample of alleged Australian and UK passports has been leaked to KillSec’s dark web site.
Simon Bell, managing director at Wendy Wu Tours Australia, said the company was investigating.
“We are reviewing the claim in light of recent reports,” he told Information Age.
“We take such matters seriously and will provide updates as appropriate.”
The ransom gang neglected to explain precisely what data it has stolen.
Next to the sample of allegedly stolen passports, KillSec’s listing called for Wendy Wu Tours to pay an undetermined sum of euros for it to delete any stolen data.
“Company can pay for data deletion, and non-company related individuals may contact us to reach an agreement for data purchase,” wrote KillSec.
At the time of writing, a countdown timer gives approximately seven days for a company representative to “negotiate” over the allegedly stolen data.
“If you are an authorised representative to negotiate on behalf of this company, submit your application,” wrote KillSec.
The Dark Web listing for Wendy Wu Tours. Photo: Supplied
KillSec’s “low-skill hackers” target mid-sized entities
Ransom gang KillSec grew to prominence in 2024 for a string of global ransom attacks against healthcare, finance and government organisations.
Notably, cybersecurity company BitSight observed KillSec was responsible for the “highest number of ransomware attacks” in January 2025.
With the gang first being observed in October 2023 through a ‘job listing’ for cybercriminal talents on Telegram, KillSec has gone on to operate a lucrative ‘Ransomware-as-a-Service’ (RaaS) model where affiliates can effectively deploy ransomware for a cut of any extorted gains.
Nalin Arachchilage, associate professor in cybersecurity at RMIT University, said KillSec’s model reflects a “growing trend” where cybercriminals make ransomware tools widely available, allowing even “low-skilled hackers” to launch sophisticated attacks.
“This ‘ransomware on demand’ approach has led to a surge in extortion cases, making businesses of all sizes vulnerable,” Arachchilage told Information Age.
Arachchilage said Wendy Wu’s alleged data breach highlighted an “alarming shift” towards cybercriminals increasingly targeting mid-sized Australian businesses.
“These companies often hold valuable customer data but may lack the robust security measures of larger corporations, making them attractive targets,” said Arachchilage.
“With RaaS becoming more accessible, we’re likely to see more of these attacks, especially in industries where digital transformation is outpacing cybersecurity investment.”
Threat analyst SocRadar meanwhile estimates KillSec may operate from the “Eastern Europe-Russia region”.
In late February, the United States Cyber Command reportedly paused its cyber offensives against Russia.
Aussies shirk ransom attempts
Information Age has observed at least five other Australian KillSec listings since late 2024, including an alleged February breach against Australian education centre Albright Institute of Language and Business.
Notably, all Australian victims listed by KillSec prior to the Wendy Wu breach had their allegedly stolen data published to the gang’s dark web leak site, suggesting none of KillSec’s Australian victims have been willing to meet the gang’s ransom demands.
According to an annual ransomware survey from advisory firm McGrathNicol, 84 per cent of Australian ransomware victims in the past five years opted to pay their attackers (averaging $1.35 million per event), though mandatory ransom payment reporting requirements introduced November last year are expected to impact these figures.
“The fact that KillSec has consistently published stolen data suggests Australian businesses are standing firm – a stance that aligns with global best practices and discourages further attacks,” said Arachchilage.
“Government messaging and last year’s mandatory ransom payment reporting requirements likely play a big role in this.
“By requiring transparency, the policy removes the secrecy around ransom payments, making it harder for companies to quietly pay off attackers.”










