A new email worm identified by email security provider Proofpoint is specifically targeting Australian users.
The DanaBot worm was first identified in early May, masquerading as an email from “Roads and Maritime Services” with what it claimed was an E-Toll account statement.
The worm reappeared later in May under various guises as bills or tracking codes.
In each case, the email contains a web link pointing to a Microsoft Word document with an embedded Macro.
The Macro contains a Windows Powershell command that downloads an external executable with the payload of the malware.
According to Proofpoint, the malware is designed to specifically target Australian users, even going so far as to check the IP address for the user’s geolocation when the Macro executes and rejecting any IP address not in Australia.
DanaBot monitors the infected system for online banking and cryptocurrency transactions.
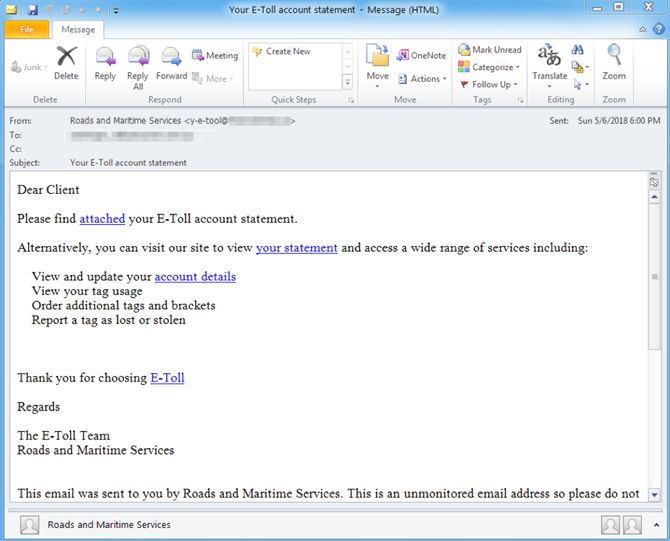
The DanaBot email. Source: Proofpoint.
It monitors and logs browser activity on a suite of key sites, and monitors processes associated with cryptocurrency.
According to Proofpoint, the malware was released by a single actor known as TA457, an operator known for producing and releasing targeted banking trojans.
Proofpoint said that this was part of a trend, signalling a move away from ransomware threats backs into more traditional spyware-style malware with more precise targeting of recipients.
“After nearly two years of relentless, high-volume ransomware campaigns, threat actors appear to be favoring less noisy malware such as banking Trojans and information stealers,” noted Proofpoint in the threat report.
“The social engineering in the low-volume DanaBot campaigns we have observed so far has been well-crafted, again pointing to a renewed focus on quality over quantity in email-based threats.”









