Cybersecurity researchers have found a new malware on the Google Play store.
Joker — named after one of the trojan’s command and control domain names — delivered a component that silently signed unwitting users up to premium subscription services.
It was packaged in 24 apps that had been downloaded nearly 500,000 times.
Google has since removed the apps from its store.
In a post on the CSIS Security Group blog, malware analyst Aleksejs Kuprins explains how the trojan slowly siphoned money from its victims.
“The automated interaction with the advertisement websites includes simulation of clicks and entering of the authorisation codes for premium service subscriptions,” Kuprins said.
“This strategy works by automating the necessary interaction with the premium offer’s webpage, entering the operator’s offer code, then waiting for a SMS message with a confirmation code and extracting it using regular expressions.
“Finally, the Joker submits the extracted code to the offer’s webpage, in order to authorise the premium subscription.”
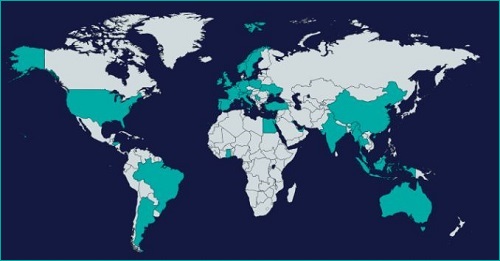
Kuprins said subscriptions of $10 per week had been made through Joker and that it went after users from specific countries including China, India, Australia, the US and UK.
Joker targeted users from 37 countries.
Like the recent iPhone vulnerability, Joker was well-built, sophisticated, and had the capability to monitor infected phones by scraping contacts and reading SMS.
“This malware kit stands out as a small and a silent one,” Kuprins said.
“It is using as little Java code as possible and thus generates as little footprint as possible.
“Whenever the malware extracts a code from a SMS message — it also reports it to the C&C after the job is complete.
“Hypothetically, the botnet operator can craft a job, which would result in all incoming SMS messages being stolen.”
He could not attribute Joker to any specific developer, but Kuprins said the malware’s command and control centres and “some of the bot’s code comments” were written in Chinese – which could hint to the developers’ location.
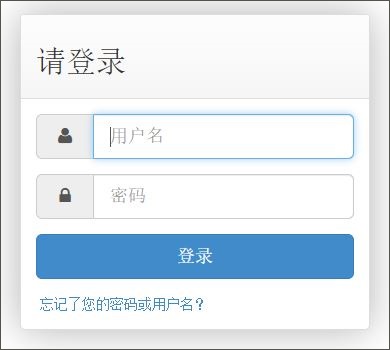
Screenshot of the login page for one of Joker’s online command and control centres.
In order to avoid being stung by malware, Kuprins said Android users need to maintain awareness about what their apps can access.
“We recommend paying close attention to the permission list in the apps that you install on your Android device,” he said.
“Obviously, there usually isn’t a clear description of why a certain app needs a particular permission, which means that whenever you are downloading any app — you are still relying on your gut feeling to some extent.”
App-based malware could soon be a thing of the past with the upcoming introductions of subscription-based app stores.
Google has announced it will soon release Google Play Pass which — like its rival, Apple Arcade — will give users a curated set of apps they can access for a monthly subscription fee.
It’s almost time ⏲️ Google Play Pass is coming soon. pic.twitter.com/vTbNmRehLm
— Google Play (@GooglePlay) September 9, 2019
Here is the full list of all the apps affected by Joker:
Advocate Wallpaper
Age Face
Altar Message
Antivirus Security – Security Scan
Beach Camera
Board picture editing
Certain Wallpaper
Climate SMS
Collate Face Scanner
Cute Camera
Dazzle Wallpaper
Declare Message
Display Camera
Great VPN
Humour Camera
Ignite Clean
Leaf Face Scanner
Mini Camera
Print Plant scan
Rapid Face Scanner
Reward Clean
Ruddy SMS
Soby Camera
Spark Wallpaper