The office of the Western Australian Premier was targeted by a cyber attack from a hacking group with alleged ties to the Chinese military, according to cybersecurity researchers.
In early January, an infected computer in the Indonesian Embassy sent an email to the WA Premier’s office containing a malicious Word document titled ‘The Indians Way’.
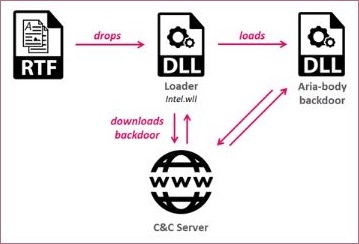
Had it been opened, that file would have dropped a loader into the target’s Word startup. The loader would then have tried to download and execute the Aria-body backdoor from a command and control (C&C) server.
With the Aria-body dll added to one of many potential Windows processes, the hackers could have accessed files, monitored internet traffic, and possibly even run a keylogger.
The email bounced.
Following a report about the Aria-body backdoor from Check Point cybersecurity researchers, the New York Times ran a story naming the Prime Minister’s office as the target.
Shortly after, the Times posted a correction saying that Check Point “misidentified the Australian target” of the attempted cyber attack and amended the story to include the WA Premier’s office.
When the WA Premier, Mark McGowan fronted up to a press conference on Friday morning, he admitted he “didn’t know anything” about the incident until he was shown the Times story that day.
“As to who does these things or what happens or whether it is even true, we will try and get to the bottom of that,” McGowan said.
A WA government spokesperson has since confirmed that the email was deflected by security systems.
"The incident was reviewed by the Australian Cyber Security Centre and the department's email security system,” the spokesperson said.
“No further action was necessary.”
WA’s opposition went on the offensive with the Shadow Minister for Innovation and Disruptive Technologies, Zak Kirkup, saying it was “a concern” that the premier didn’t know about the cyber incident until it was reported in the Times.
“Why didn’t he know?” Kirkup asked.
“The Premier’s office contains highly sensitive commercial information of our largest companies, including internationally exposed mining and oil and gas companies.
“This information in the wrong hands could undermine or commercially disadvantage our largest employers and impact our already struggling economy.”
The Naikon group
Check Point attributed the attack to hackers known as the Naikon advanced persistent threat (APT) group.
In 2015, Kaspersky had spotted Naikon infecting countries in the Asia-Pacific region as part of what appeared to be a “cyber-espionage campaign”.
“The attackers appeared to be Chinese-speaking and targeted mainly top-level government agencies and civil and military organisations,” Kaspersky said.
Check Point’s latest report on the group says Naikon has been going after “government entities including ministries of foreign affairs, science and technology ministries, as well as government-owned companies”.
“Given the characteristics of the victims and capabilities presented by the group, it is evident that the group’s purpose is to gather intelligence and spy on the countries whose governments it has targeted,” Check Point said.
An example infection chain of the Aria-body backdoor. Source: Check Point
Part of Naikon’s modus operandi – as demonstrated in the incident with the WA Premier’s office – is to leverage the infrastructure of one infected government entity to breach another.
As well as sending emails from embassies based in the target country, Check Point also found a C&C server that was configured to “an IP which belongs to the Philippines department of science and technology”.
Although neither Kaspersky nor Check Point have attributed Naikon to any specific nation-state, Threat Connect has previously said the APT group was associated with the Chinese military – specifically an arm of the military focused on disputed areas in the South China Sea.
In a statement to the ABC, Chinese Consul General Dong Zhihua, denied any suggestion that Chinse state-actors were behind Naikon’s alleged cyber espionage campaign.
"The Chinese Government, military and relevant personnel never engage in cyber attacks or cyber theft,” Zhihua said.
"China cherishes its long-standing and strong partnership with Western Australia. Any attempt to undermine this friendship by fabricating groundless accusations against China is doomed to fail."