Google has put the kibosh on a massive botnet called ‘Glupteba’ that has controlled an estimated one million compromised Windows devices in order to steal credentials, mine cryptocurrency, and route malicious traffic using Google services.
In a pair of blog posts on Wednesday, Google explained how it had been working to combat the botnet by knocking out its digital infrastructure – much of which had been running through Google’s own platforms.
The tech giant has also launched legal action against the botnet’s alleged operators.
“We’ve terminated around 63 million Google Docs observed to have distributed Glupteba, 1,183 Google accounts, 908 Cloud Projects, and 870 Google Ads accounts associated with their distribution,” Shane Huntley and Luca Nagy from Google’s Threat Analysis Group said.
“Furthermore, 3.5 million users were warned before downloading a malicious file through Google Safe Browsing warnings.”
A botnet is a network of internet-connected devices that are being surreptitiously controlled for nefarious means – like the infamous Emotet botnet that recently resurfaced and which uses compromised machines to send phishing emails that connect more unsuspecting devices to its network.
The malware powering Glupteba was typically distributed through pay-per-install advertising – a type of marketing where the advertiser pays for each installation generated by a campaign – as well as malicious ads, including cryptocurrency scams, delivered through Google Ads.
“In the last few days, our team partnered with internet infrastructure providers and hosting providers, including CloudFlare, to disrupt Glupteba’s operation by taking down servers and placing warning interstitial pages in front of the malicious domain names,” Huntley and Nagy said.
“During this time, an additional 130 Google accounts associated with this operation were terminated.”
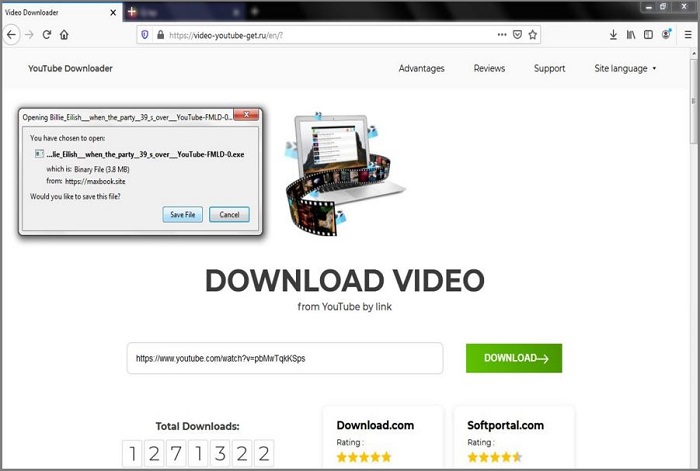
The Glupteba botnet was delivered through dodgy downloads like this fake YouTube downloader. Image: supplied
It’s been a big cleanup effort, but one that doesn’t guarantee the end of Glupteba because of a backup mechanism the network’s operators installed that references the Bitcoin blockchain.
When Glupteba doesn’t hear back from calls to its main command and control servers, as might happen when Google goes around disabling them, it instead pings the most recent transactions from specific Bitcoin addresses that returns an encrypted domain name.
The bot then decodes the domain and uses that server to communicate with its controllers, deliver malware, and just generally run amok.
Writing new server details on the blockchain is an ingenious way for the attackers behind Glupteba to maintain the botnet’s persistence even when its servers get kicked offline – and is the reason why Google decided to take an extra step to fight back: a law suit.
Google filed civil proceedings against the alleged operators of Glupteba, two Russian men named Dmitry Starovikov and Alexander Filippov, who it identified in part because the IP addresses they used to sign up for Gmail accounts matched those used by the Glupteba botnet.
The company is seeking damages from Starovikov and Filippov for a litany of offences against US law as well as the harm they have allegedly caused against not only the owners of infected devices, but Google and “the internet ecosystem as a whole”.
Google hopes the litigation “will create real legal liability” for the people behind Glupteba.