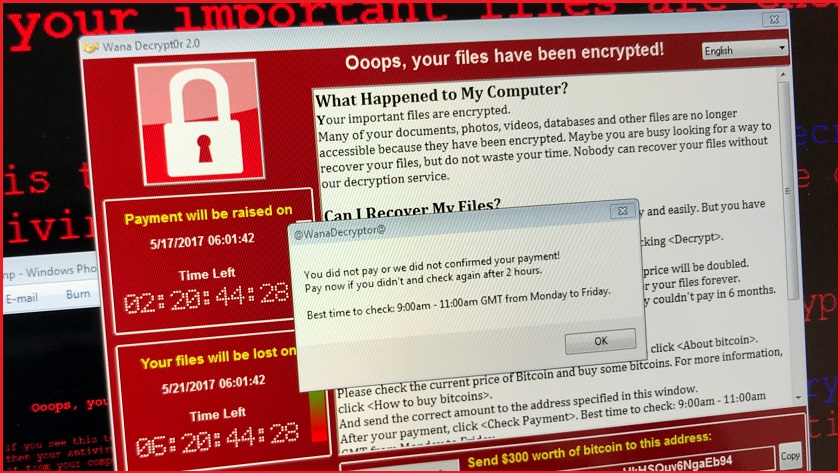
The Australian Signals Directorate (ASD) has admitted it continues to see instances of the WannaCry ransomware – that first surfaced in 2017 – affecting local organisations despite it being years since vulnerabilities the malware targets were patched.
In its latest Cyber Threat report – that provides an overview of the cyber security landscape from the last financial year – Australia’s cyber spy agency said it “still receives periodic reports of WannaCry malware”.
“[This] is likely due to old, infected legacy machines being powered on and connected to networks,” it said.
“Incidents like this highlight the importance of patching as soon as possible, and also demonstrate the long tail of risks that unpatched and legacy systems can post to entities.”
WannaCry was a prominent ransomware strain that used the EternalBlue Windows exploit, developed and kept secret by the US National Security Agency, and was spread by North Korean hackers to lock down machines and demand cryptocurrency payments.
Famously, WannaCry knocked out the UK National Health Service.
The ASD received 94,000 reports of cyber crime in the last financial year, up 23 per cent on the year before. It noted that the cost of cyber crime has gone up by 14 per cent.
Ransomware was once again among the most common complaints, accounting for 10 per cent of incidents the ASD responded to in 2022-23.
The ASD is trying to encourage more individuals and organisations to share cyber security incidents so it can better understand the Australian threat landscape and help protect where possible.
That it continues seeing a retro ransomware strain like WannaCry pop up every now and then points echoes the frustrations of Home Affairs Minister Clare O’Neil who recently expressed disappointment that businesses remain unpatched against known vulnerabilities for months, even years.
ASD recommends patching all internet-facing devices “within 48 hours” of a vulnerability disclosure, adding that “entities with limited security expertise” should lean on cloud and managed services providers to “help ensure timely patching”.
It also acknowledged not everyone can patch immediately, and said that in those instances, organisations should consider other mitigating actions like cutting parts of the system from the internet, “strengthening access controls, enforcing network separation, and closely monitoring systems for anomalous activity”.
Deputy Prime Minister Richard Marles told ABC News Breakfast there has been “a 23 per cent increase in the number of reports of cyber incidents” with the costs of those incidents going up, too.
“So, more reports of incidents and those incidents are costing more to small businesses.”
Professor Nigel Phair from Monash University said the continual increase in number of cyber crime reports was “a consistent pattern” that would keep going “until Australian organisations start putting more effort into cyber security and the risk management of their information assets”.
All eyes on China
As Marles attended morning news programs, hosts repeatedly probed the Deputy Prime Minister on China’s involvement in cyber attacks despite the country only being mentioned by name four times in the report.
"We have the full conversation with China,” Marles told Sky News. “We’ve never said that China is anything other than a deeply complex relationship.”
The ASD report mentions the last time Australia attributed state-based attacks to China back in May when it joined with Five Eyes security counterparts to condemn the actions of Chinese hacking group Volt Typhoon.
Prime Minister Anthony Albanese recently visited China, becoming the first Australian Prime Minister to do so since 2016 in a bid to stabilise the relationship with our biggest trading partner and provide “security and stability” in our region.
Indeed, the ASD report warns that as “the global and regional strategic environment continues to deteriorate”, state actors are “increasingly using cyber operations as the preferred vector to build their geopolitical competitive edge”.
Since the war in Ukraine began, according to the ASD, there has been an increase in cyber activity throughout Europe showing how countries not directly involved in a conflict can find themselves in the cyber crossfire.
“For example, pro-Russian hacktivists, KillNet, have claimed a number of attacks such as the February 2023 DoS attack on numerous German websites, including those for German airports, public administration bodies, financial sector organisations, and other private companies,” the ASD report said.
“Belarus also reported its railway network was disrupted by a cyber attack, allegedly as retaliation for its use in transporting Russian troops.”
It’s a stark warning that shows how the borderless nature of cyber warfare can see nations pay for even the most distant involvement in international conflicts.
The ASD, through this report, is trying to encourage more Australian organisations to partner with its various programs that help share threat intelligence, improve the resilience of critical infrastructure, and generally uplift the national cyber security posture.
Andrew Wilson, CEO of ASX-listed cyber security firm Senetas, said the report offered few surprises and it goes to show how much businesses need to step up and protect themselves.
“The real questions we should be asking are how seriously businesses are taking the insights from these reports and whether they truly comprehend the imminent risk of being targeted next,” he said.
“While the federal government is, commendably, investing in strategic initiatives to bolster national cyber security, their efforts can only go so far.”