The New South Wales government is falling short on cybersecurity as state agencies implement less than a third of mandatory protections, an audit has found.
Last week, the Audit Office of NSW released a report that measured state agency compliance with the NSW Cyber Security Policy (CSP).
Analysis of data from the 2023-2024 financial year identified several shortcomings, with the “biggest gaps in cyber resilience” being the implementation of minimum protective controls.
Agencies met only 31 per cent of requirements under the CSP’s ‘Protect’ category, which includes patching, backup, and multi-factor authentication strategies under the Australian Cyber Security Centre’s ‘Essential Eight’, as well as training programs and controls for email and network security.
“The absence of ‘protect’ domain controls increases the likelihood of a successful cyberattack,” read the report.
About 50 per cent of mandatory requirements were met in the policy’s two other categories: ‘Govern and Identify’ and ‘Detect, Respond and Recover’, which include requirements for data management and security event monitoring.
The audit also highlighted shortcomings in risk reporting and mitigation, with a total of 152 “significant, high and extreme” residual cybersecurity risks reported across 27 agencies.
Some 28 of these risks had treatment controls which were either “largely or completely ineffective”, 60 risks “lacked specified timelines to reduce them to an acceptable level”, and 30 had a mitigation timeframe exceeding one year.
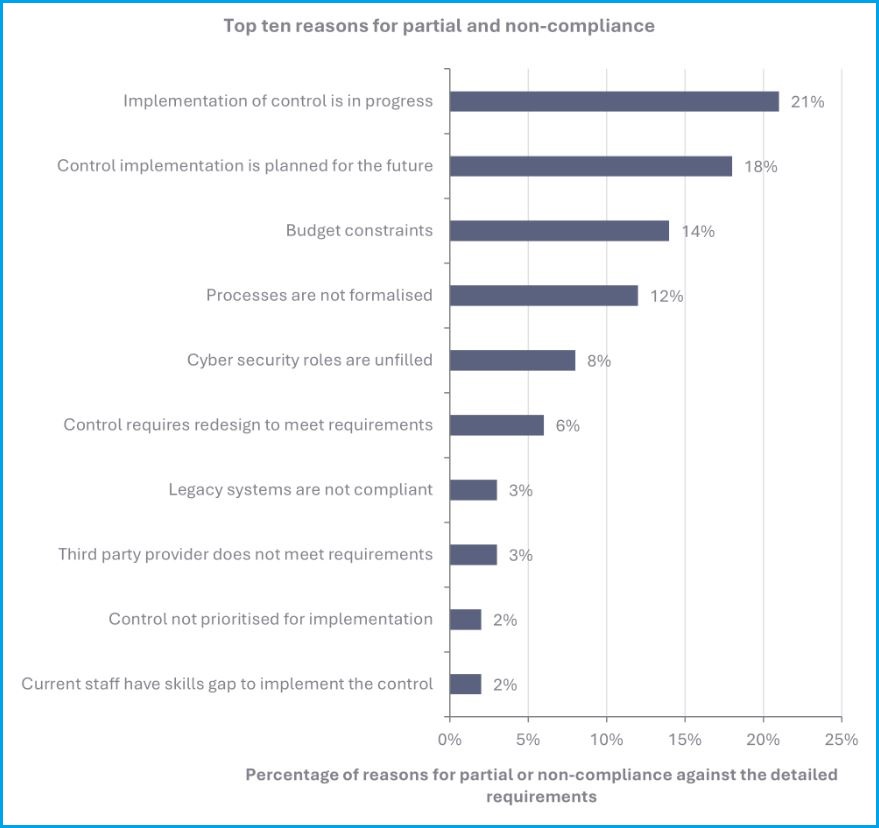
When asked to provide their reasons for failing to meet minimum compliance requirements, agencies most often said cyber uplift programs were in progress or planned.
Other common reasons were budget constraints, a “lack of approved or formalised cyber processes”, and unfilled cybersecurity roles.
Mandy Turner, adjunct lecturer in cyber criminology at The University of Queensland, said it was “important to keep in mind cyber risks can emerge faster than anyone can mitigate”.
“There will always be gaps but the important thing is to be aware of them and work towards ongoing improvements to mitigate emerging risks,” Turner told Information Age.
Source: Audit Office analysis of agency cyber security compliance returns to Cyber Security NSW for 2024
Third-party blind spots
Notably, 22 per cent of all mandatory protection measures were managed by third parties, creating “an absence of clear reporting” which risked agencies and Cyber Security NSW “not knowing” about cases of non-compliance.
Turner said relying too heavily on external vendors without building internal capacity could cause risks such as exposure to supply chain compromises or outsourced teams not fully understanding an “agency’s unique environment”.
“External providers have their place and can be useful to augment internal mechanisms, such as tools, resources and staff — however, the importance of developing capabilities of in-house teams should not be ignored,” she said.
The report arrived days before a data breach at national airline Qantas was attributed to an incident at a third-party customer servicing platform.
Vaughan Shanks, chief executive of Melbourne-based incident response vendor Cydarm Technologies, said although third-party vendors might “be the only viable option” for smaller organisations, decision makers are “still accountable” for cybersecurity outcomes.
“Third-party vendors are not a set-and-forget solution,” said Shanks.
“There must be regular reporting, feedback, and clear division of responsibilities and points of contact.”
Basic protections lacking
The report showed that across 66 reporting agencies, less than 15 were fully compliant with the requirement to implement multi-factor authentication.
Around 15 agencies met requirements to patch applications, about 10 managed to do so for patching operating systems, and less than 25 agencies met requirements to conduct awareness activities, including security awareness training.
At the local level, just 69 per cent of councils trained their staff in cyber awareness and 45 per cent did not conduct phishing simulations whatsoever.
“Cyber awareness training is a cost-effective control that should be mandatory at every organisation, to better defend against social engineering attacks such as phishing emails,” said Shanks.
“The gap in council cyber awareness training presents an opportunity for ransomware gangs, who have demonstrated in recent years that municipal governments are seen as soft targets.”
Indeed, the report pointed out a 2020 phishing attack at Service NSW resulted in 3.8 million documents being stolen and an estimated $30 million in costs, and a 2022 ransomware attack at a NSW council impacted council records, employee financial data, and systems responsible for monitoring water quality.