Some Australian businesses must now report to the government if they have paid a ransom after being extorted during a ransomware attack, under a new law which takes effect from Friday, 30 May 2025.
Ransomware — a type of malicious software (malware) which effectively locks up or encrypts a victim’s data and demands a ransom payment for files to be made available again — has become a key cybersecurity threat to Australian organisations.
Here’s what you need to know about the new mandatory ransomware payment reporting obligations.
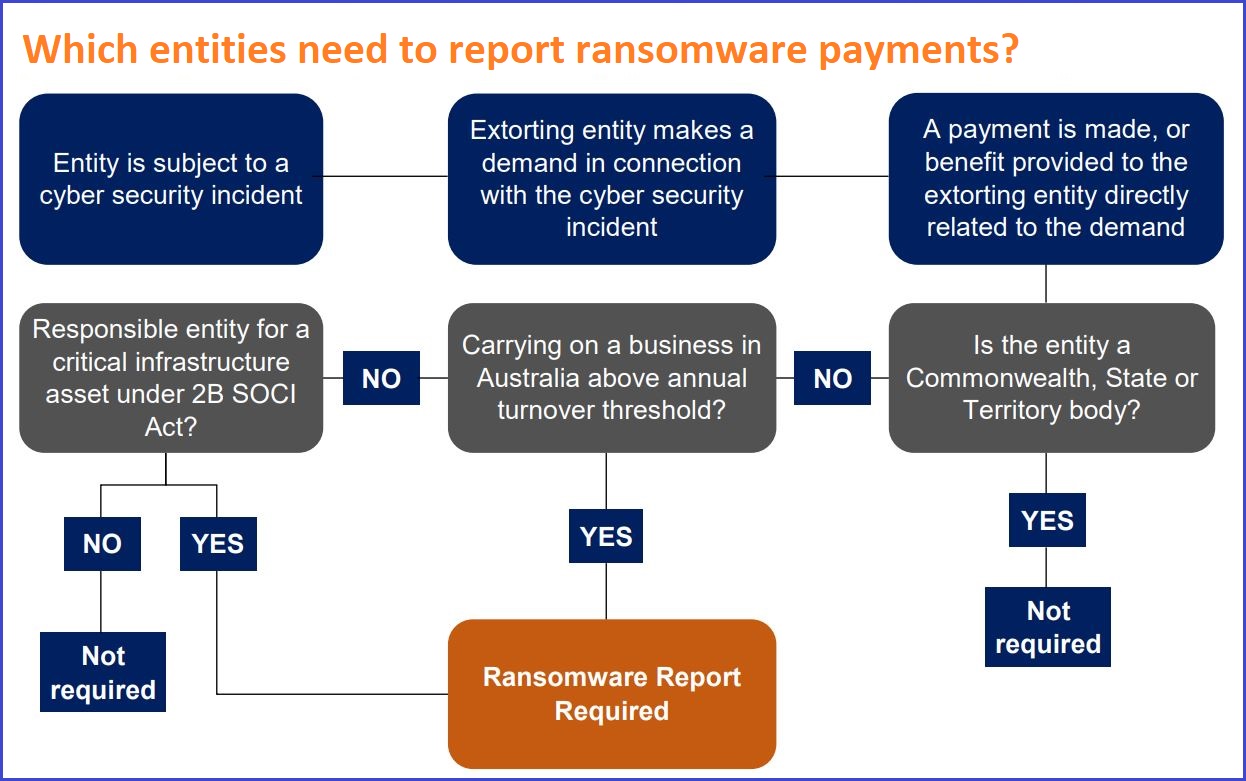
Who must report ransomware payments?
Australian businesses with an annual turnover of $3 million or more that are not Commonwealth or state bodies are obliged to report ransomware payments, as well as certain bodies which are responsible for critical infrastructure assets.
Reports will also need to be made if the extorting entity does not demand Australian currency and instead seeks a ransom paid in cryptocurrency, information, or a service.
The $3 million threshold was decided on following industry feedback, the government said, and was designed to “balance the need to get a clear whole-of-economy picture of the threat landscape, and to avoid imposing regulatory burden on small businesses”, according to the Department of Home Affairs.
More than 90 per cent of Australian businesses have annual turnover of less than $2 million and would be exempt from reporting ransomware payments, according to the latest Australian Bureau of Statistics data.
Entities reporting ransomware payments will be asked for information such as when the incident occurred, when the organisation was made aware of it, what impact the incident had, what demands and payments were made, and what communications occurred with the threat actor.
Organisations which experienced other types of cyber extortion, such as a ransom payment made after data was exfiltrated or stolen, may also need to make a report under the scheme.
The government says businesses with annual turnover of $3 million or more must report ransomware payments. Image: Department of Home Affairs (heading added)
Are there penalties for not reporting ransomware payments?
Yes, there will be financial penalties for non-compliance, but the government says it will offer warnings to some businesses.
Companies will face fines of $19,800 if they do not report a ransomware payment within 72 hours of the payment being made or the company becoming aware a payment had been made on its behalf.
While businesses face fines for not complying, the government said it would take “an education-first approach” in the first six months of the regulation.
The Department of Home Affairs said it would “prioritise warnings, meetings and engagements, before pursuing civil penalties, especially in respect of small and medium enterprises”.
David Tuffley, a senior lecturer in applied ethics and cybersecurity at Griffith University, told Information Age that while some businesses “might be tempted to stay quiet to avoid reputational damage”, the risk of fines and the government’s pledge to educate “will discourage that”.
“Plus, reporting is protected, so it’s safer for businesses to comply than to risk being caught out for non-reporting later,” he said.
Why was the rule introduced, and what impact could it have?
The government decided to take action on ransomware payments because of the crime’s increasing impact on Australians, with the reforms included as part of Australia’s first Cyber Security Act, a spokesperson for the Department of Home Affairs told Information Age.
Industry group the Australian Cyber Network (ACN), which represents local cybersecurity businesses, recently found more than two-thirds of Australian businesses had been hit by ransomware in the past five years, and most opted to pay ransoms.
Federal intelligence body the Australian Signals Directorate (ASD) said in November that ransomware posed “significant operational, financial and reputational risk to Australia”, and confirmed it had responded to 121 such incidents in the 2023-24 financial year.
“Ransomware is one of the most destructive and pervasive forms of cybercrime in Australia, costing the economy millions of dollars in damages each year,” the Department of Home Affairs spokesperson said.
David Tuffley from Griffith University said the new rule would push businesses to strengthen their defences and help the government “track trends, spot patterns, and respond faster” when it came to ransomware campaigns.
"It helps everyone understand the real scale of the problem and improves support for those businesses under attack,” he said.
“It means businesses will need to tighten up their cyber defences and have clear incident response plans.”
Aaron Bugal, the chief information security officer in the Asia-Pacific and Japan for cybersecurity firm Sophos, said the mandatory reporting of ransomware payments marked “a major step toward transparency and accountability in cybercrime response”.
“Being required to disclose any ransomware payments will force a need for a review of and an update to policies, incident response plans and ensuring board-level awareness,” he said.
“While this adds a layer of compliance, it also encourages better cyber hygiene and may reduce the likelihood of a ransom payment as an easy way out after an attack.”

The Australian Cyber Network (ACN) has found most local businesses hit by ransomware in the past five years opted to pay ransoms. Image: Shutterstock
What’s the government’s stance on whether ransoms should be paid?
The Australian government continues to not condone the payment of ransoms to perpetrators of ransomware, which include highly organised ransomware gangs.
Minister for Cybersecurity, Tony Burke, said in October, “No business or individual should ever pay a ransom to cybercriminals.
“If a ransom is paid, there is no assurance that data will be recovered or that data will not be on-sold or released.”
David Tuffley said this was the right stance to take.
“Paying ransoms only encourages more attacks and doesn’t guarantee a fix,” he said.
“The government isn’t punishing victims, just discouraging payments while offering support.
“It’s about breaking the cycle and making Australia a tougher target for cybercriminals.”
How should businesses report ransomware payments?
Businesses and entities which are obliged to report ransomware payments should do so through the cyber.gov.au website, the federal government says.
It has also released an interactive guide to ransomware called the Ransomware Playbook, which provides advice on preparing for, responding to, recovering from, and reporting ransomware incidents.
Cybersecurity assistance is also available 24/7 through the government’s Australian Cybersecurity Hotline on 1300 CYBER1 (1300 292 371).
Will ransomware payment reports be made public?
While reports of ransomware payments will not be published publicly, they can be used or disclosed by the Department of Home Affairs and the ASD under so-called “permitted purposes”.
These include when assisting in cybersecurity incidents and working with Commonwealth and state bodies, the National Cyber Security Coordinator, intelligence agencies, and government ministers, according to a Home Affairs fact sheet.
Information included in ransomware payment reports is not admissible in most criminal and civil court proceedings, or when the reporting entity is put before a tribunal — with some limited exceptions such as Royal Commissions or coronial enquiries.