Chinese state actors have started using the coronavirus pandemic to help them deliver malware and conduct spear phishing attacks, signifying a worrying trend identified by cybersecurity researchers.
Emails with subject lines like “COVID-19 Everything you need to know” and “Coronavirus Update” – which might look legitimate – are the opening gambit by attackers looking for a breach in cyber defences.
According to Ben Read, a cyber intelligence analyst at cybersecurity firm FireEye, attackers try to leverage people’s interest to trick them into making one fatal click.
“People are interested in this right now, people are nervous about it, so people will open a document that’s promising new information,” Read said.
“And anything that people are likely to open will be used by malicious actors to install malware.”
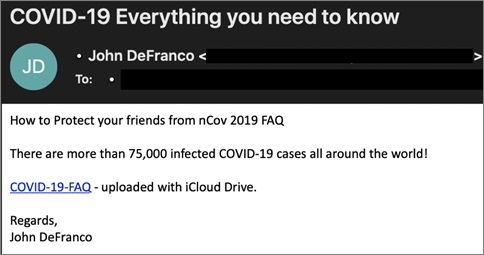
An example of a phishing email with malicious link. Source: FireEye
Read said spear phishing campaigns – in the form of malicious documents attached to emails or embedded links to spoofed websites used to steal login credentials – are the most common form of coronavirus-related cyberattack.
Using data gathered from FireEye’s cyber defence tools, Read’s team has been able to identify certain groups – given the names TEMP.Hex and TEMP.Warlock – who are operating these campaigns.
“TEMP.Hex is a group doing these attacks on behalf of the Chinese government,” he said.
“They tend to target nations in South East Asia and are going after government institutions.
“On the other hand, TEMP.Warlock are a criminal group so they’re financially motivated. They’re targeting individuals, businesses to get in and try to monetise that access in different ways.”
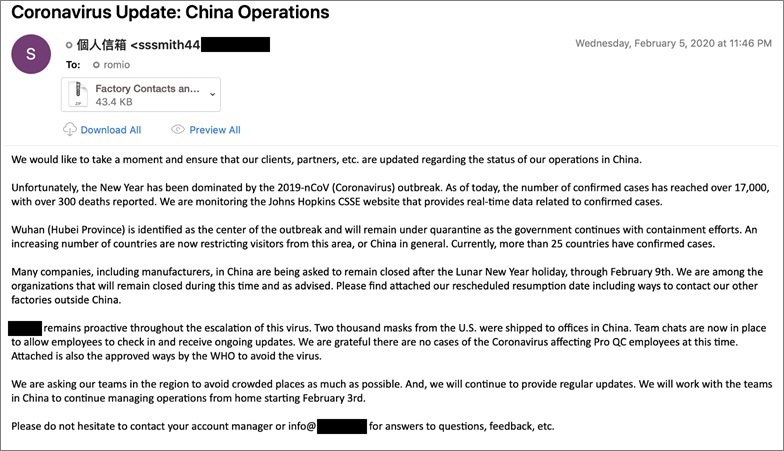
Emails can look legitimate but contain malicious attachments. Source: FireEye
Read’s team study and track the methods of attack for patterns which can be attributed to certain actors. Things like the command and control infrastructure of spoofed web addresses or specific forms of malware can help researchers understand the modus operandi of cyber attackers.
As long as coronavirus keeps drawing media attention and public panic, the threat of coronavirus-related phishing campaigns will continue, Read said.
“The best thing you can do is make sure you’re expecting something like this,” he said.
“Obviously companies are sending out notices to their employees but try and be especially wary of attachments or links.
“And be careful extra careful to make sure a site is legitimate before you enter your login credentials.”










