A ransomware attack has caused the largest oil pipeline in the US to shut down, leading to massive queues at petrol stations amidst fears of a shortage.
Colonial Pipeline, the operator of the pipeline that stretches 8,850km between Texas and New York, took some of its IT systems offline last Friday because of the cyber incident.
Early investigations point to an outdated version of Microsoft Exchange as part of the attackers' intrusion into Colonial's systems, pointing to the cascading effects of not patching for publicly disclosed vulnerabilites.
On Monday local time, the FBI confirmed the Darkside ransomware group conducted the attack on Colonial and said it was still investigating.
Described by cyber security firm Flashpoint as “Russian-speaking threat actors”, Darkside is believed to be a spinoff of REvil – the infamous ransomware-as-a-service group that recently hit an Apple manufacturer and Taiwanese hardware company Acer.
Despite speculation that Russian state hackers were behind the severely disruptive campaign, Darkside itself has denied the ransomware attack was politically motivated.
“We are apolitical, we do not participate in geopolitics,” Darkside said on its dark web leaks site.
“Our goal is to make money, and not creating problems for society.
“From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
Dmitry Peskov, a spokesperson for Russian President Vladimir Putin also denied any involvement in the Colonial Pipeline attack.
“Russia has nothing to do with these hacker attacks, and had nothing to do with the previous hacker attacks,” he said.
“We categorically do not accept any accusations against us.”
Last month, the US issued sanctions against Russia for its involvement in the massive SolarWinds attack that saw multiple US government agencies and Fortune 500 companies breached.
Creating problems for society
But even if Darkside did not intend on creating social problems, it has certainly caused them.
By mid-week, over 1,000 petrol stations on the US East Coast had run dry. With shortages leading to hoarding, some people have resorted to the ill-advised method of filling up plastic bags with petrol.
There has even been footage of a fight breaking out between customers in North Carolina, one of the worst affected areas with an estimated 25 per cent of petrol stations running dry.
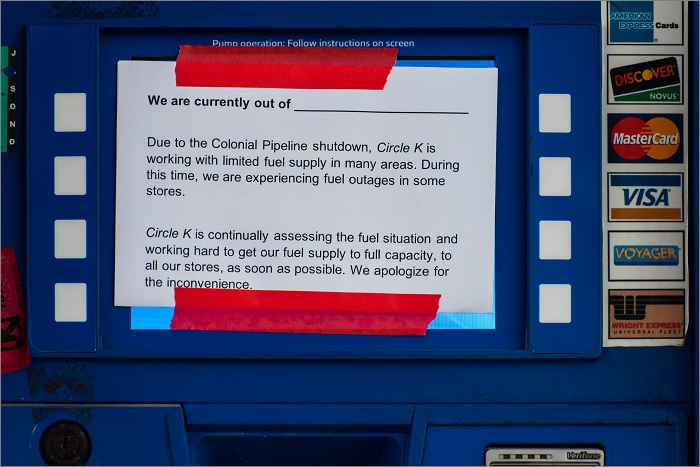
A petrol bowser in North Carolina warning customers of low supply. Image: Shutterstock
On Wednesday, US President Joe Biden said the situation was getting under control again and used the moment to call for better education.
“I have lifted some of the restrictions on the transportation of fuel, as well as access to the United States military providing fuel to places where it’s badly needed,” he said.
“I think we have to make a greater investment in education as it relates to being able to train and graduate more people proficient in cyber security.”
Critical infrastructure
Eric Goldstein, assistant director for cyber security at the US Cybersecurity and Infrastructure Security Agency (CISA), said the attack highlighted the importance of protection against these kinds of attacks.
“This underscores the threat that ransomware poses to organisations regardless of size or sector,” he said.
“We encourage every organisation to take action to strengthen their cyber security posture to reduce their exposure to these types of threats.”
Nearly a week after the attack began and Colonial has confirmed it will finally restart the pipeline after US petrol prices started closing at their highest figure in seven years.
Matt Warren, Professor of Cyber Security at RMIT University, said the Darkside group would likely incur “the wrath of the US government” as result of the lengthy disruption its attack caused.
“The attack is a wake-up call for Australian critical infrastructure providers to look at how a ransomware attack could impact them and cripple key critical services.”
The government is looking to overhaul existing critical infrastructure protections that would give it expanded powers to directly access and control certain non-government IT systems during a cyber emergency.










