Just minutes after Home Affairs Minister Clare O’Neil chastised Optus in parliament for a massive breach which saw the personal details of 9.8 million Australians stolen and calling on the telco to provide free credit monitoring, Optus has come to the party.
In question time on Monday afternoon, O’Neil said responsibility for the breach fell fairly and squarely on the shoulders of Australia’s second-largest telco.
“Responsibility for the security breach rests with Optus and I want to note that the breach is of a nature that we should not expect to see in a large telecommunications provider in this country,” O’Neil said.
“We expect Optus to continue to do everything they can to support their customers and former customers.
“One way they can do this is providing free credit monitoring to impacted customers.”
About half an hour later, Optus issued a press release, “offering the most affected current and former customers whose information was compromised because of a cyberattack, the option to take up a 12-month subscription to Equifax Protect at no cost.”
Optus said these “most affected” customers will be contacted in the coming days with details on how to start their subscription to the credit monitoring and identity protection service.
“Please note that no communications from Optus relating to this incident will include any links as we recognise there are criminals who will be using this incident to conduct phishing scams,” Optus said.
Some Optus customers are still to be notified about the breach.
O’Neil added that “a very substantial reform task will emerge from a breach of the scale and size and there is a number of policy issues that I think the public will soon become quite aware of.”
“One significant question is whether the cyber security requirements we place on large telecommunications providers in this country are fit for purpose.
“I also noted that in other jurisdictions, a data breach of this size will result in fines amounting to hundreds of millions of dollars.”
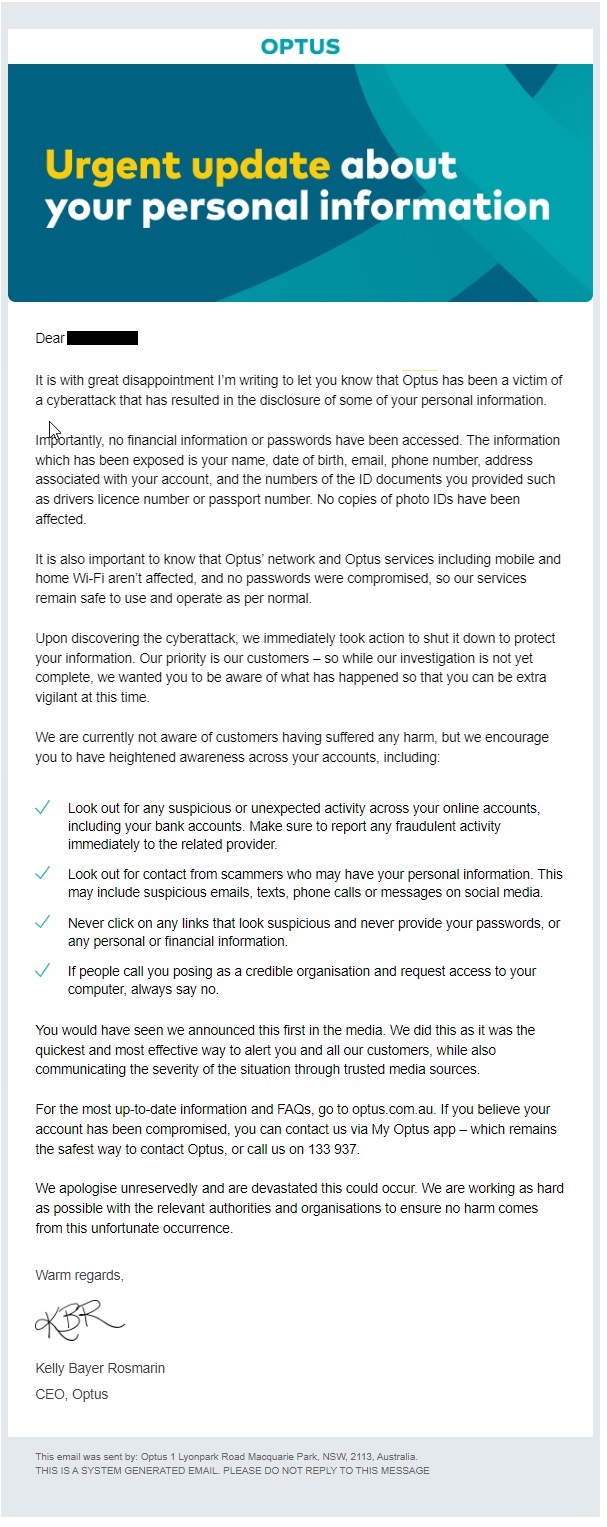
The letter sent to Optus customers. Photo: Supplied
AFP closes in
The Australian Federal Police (AFP) said it is working with overseas law enforcement to identify the hackers behind the Optus breach as part of its newly formed ‘Operation Hurricane’.
The AFP said it is aware of reports the stolen data has been placed up for sale but declined to disclose the information it had obtained since the breach was reported on 22 September.
“We are aware of reports of stolen data being sold on the dark web and that is why the AFP is monitoring the dark web using a range of specialist capabilities,” said Assistant Commissioner Cyber Command Justine Gough.
“Criminals, who use pseudonyms and anonymising technology, can’t see us but I can tell you that we can see them.
“A key focus, which we have had success in the past, is to identify those criminals.
“It is an offence to sell or buy stolen identification credentials, with penalties of up to 10 years’ imprisonment.
“Our presence and focus extends outside Australian borders, and AFP specialised cyber investigators are permanently based in the United Kingdom, United States, Europe and Africa.
“We will use all our technical capabilities and tools to protect the public from cybercrime but we also need the public to be extra vigilant.
Class action
Law firm Gordon and Slater has moved quickly to investigate a possible class action by present and past customers against Optus.
“This is potentially the most serious privacy breach in Australian history, both in terms of the number of affected people and the nature of the information disclosed,” Class Actions senior associate Ben Zocco said.
“We consider that the consequences could be particularly serious for vulnerable members of society, such as domestic violence survivors, victims of stalking and other threatening behaviour, and people who are seeking or have previously sought asylum in Australia.
“Given the type of information that has been reportedly disclosed, these people can’t simply heed Optus’ advice to be on the look-out for scam emails and text messages. Very real risks are created by the disclosure.”
Interested Optus customers can register their expression of interest here.
Unrest continues
Cyber professionals and researchers across Australia continue to voice their concerns over the Optus breach.
“Given the sensitive information required by telcos for a customer to open an account, this breach should send a collective shiver down the spine not just of every Optus customer, but every business tasked with protecting important customer data,” Adapt Senior Director of Strategic Research Matt Boon said.
"While it's still too soon to understand the full impact of this breach, this is without a doubt one of the most significant cyber-attacks Australians have ever seen.
“Over a third of the population is nervously watching and waiting to see if they've been affected.
Boon criticised Optus’ advice to customers to “increase their vigilance”, saying it was simply not good enough, as it isn’t their responsibility to fix.
He said Optus should engage in a rapid, in-depth assessment of exactly who was affected and to what extent; an information campaign specifying, to each customer, the type of data that has been affected; advise unaffected customers so they can stop worrying; and post-breach, rapidly bolster cyber defences.
StickmanCyber CEO Ajay Unni said it was “extremely sad to see Australia under attack from cybercriminals who are finding success in exploiting vulnerabilities to gain unauthorised access to businesses and critical infrastructure.”
People, he said, will always be the weakest link in cyber security.
"The findings of the Australian Cyber Security Centre’s investigation into Optus’s data breach will reveal the true nature of the attack – whether it was the work of cybercriminals or a state-sponsored attack.
"Telcos like Optus carry large amounts of information about their customers such as call patterns, incoming/outgoing phone numbers, data/internet usage and other forms of personal information that can be easily exploited.
"The data exposed can now be maliciously used to create fake identities or as a launchpad to further target users individually through spear-phishing campaigns. These campaigns will now be even more effective as cyber criminals have access to more information than just an email address.”
Phillip Ivancic, APAC head of Solutions Strategy, at security testing software company Synopsys commended the “hardworking Optus IT Security teams for their swift actions.”
“The fact their CEO, Kelly Bayer Rosmarin, was able to provide initial details and a public statement seemingly within hours on a national public holiday means that Optus must have a well-established, and well-practised, Incident Response Plan,” he said.
“The early reports indicate that the breach was picked up as a part of their continuous assessment framework another example of important and multi-layered defences.”
Advice from AFP
For cyber safety tips, visit: https://www.cyber.gov.au/acsc/individuals-and-families
Those who believe they have fallen victim to cybercrime should immediately contact ReportCyber on: https://www.cyber.gov.au/acsc/report
If you are concerned that your identity has been compromised, contact the national identity and cyber support service IDCARE: https://www.idcare.org/










