Clorox has sued IT services firm Cognizant for allegedly providing system logins to a hacker who caused the company $580 million in damages.
Court documents explained that in 2023, bleach manufacturer Clorox suffered a “debilitating” cyberattack which “paralysed” its corporate network and “crippled” business operations.
Clorox alleged it was not duped by any sophisticated hacking techniques – rather, the hacker simply rang up third-party firm Cognizant and asked for Clorox’s system login details over the phone.
According to Clorox, Cognizant’s staff obliged.
“Cognizant repeatedly gave a cybercriminal access to Clorox’s network by handing them credentials without properly authenticating them,” read the lawsuit, filed in the California Superior Court.
“Cognizant’s failures resulted in a catastrophic cyberattack on Clorox.”
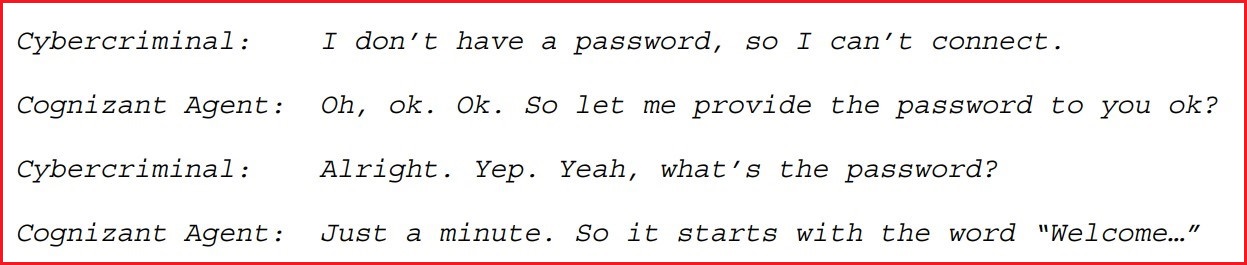
Clorox explained the hacker rang Cognizant’s helpdesk five separate times to successfully reset passwords and multi-factor authentication (MFA) details.
Cognizant refuted the allegations by emphasising its role as a helpdesk operator.
“Cognizant did not manage cybersecurity for Clorox and we will vigorously defend ourselves against these allegations,” Cognizant said in a statement to Information Age.
Clorox is suing for $580 million (US$380 million) in damages related to remedial costs and business and shipping interruptions following the attack.
‘Sorry for the hold, here’s the password’
Incident updates from 2023 show that, over the course of a month, Clorox staff worked “around the world and around the clock” to handle orders manually and restore a number of impacted IT systems.
Clorox engaged Cognizant some 10 years before the attack to set up a service desk that staff could use for password recovery assistance – an arrangement which allegedly came with the “common-sense requirement” that the firm never reset anyone’s credentials without properly authenticating them first.
Although Clorox “made this easy” by providing “straight-forward procedures to follow whenever providing credential recovery or reset assistance”, Cognizant allegedly demonstrated a “blatant disregard” for the manufacturer’s policies during its calls with the hacker.
In the first phone call, for example, Cognizant allegedly conducted a password reset for identity management tool Okta and an MFA reset through Microsoft MFA despite never verifying the caller’s identify.
Clorox said Cognizant staff showed a "shocking level of incompetence". Photo: Supplied
The hacker allegedly called back four times throughout the day to change a mobile number on a Clorox staff account, perform more resets, and eventually enact the same “amateur playbook” on a second staff account.
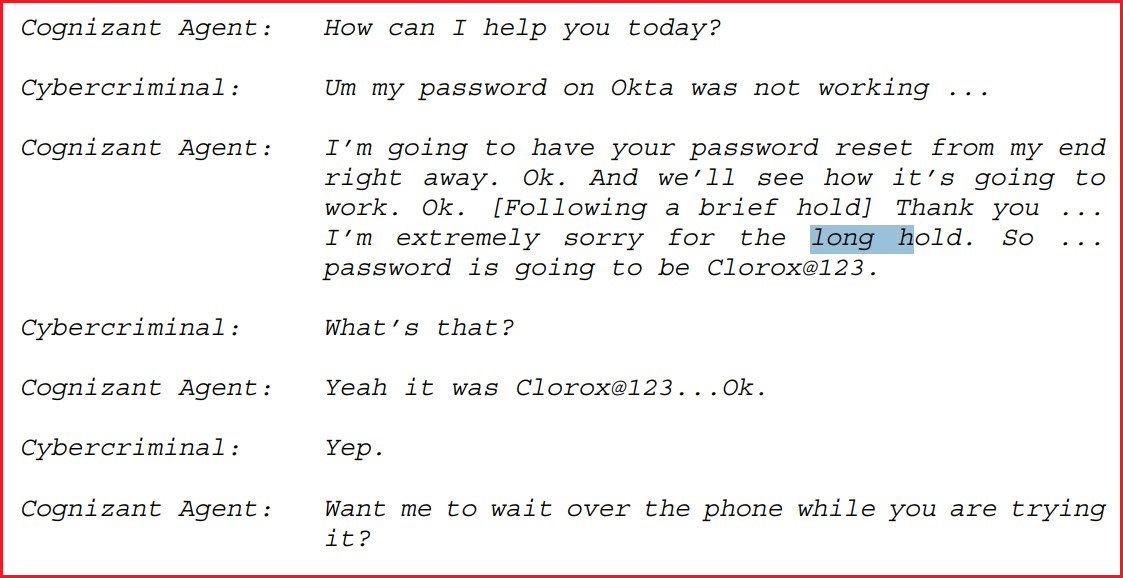
The lawsuit showed apparent transcripts between the hacker and Cognizant agents. Photo: Supplied
Though both companies’ staff participated in weekly meetings and Cognizant confirmed its team was “educated” on the required credential support procedures, Clorox said the phone calls exposed this was a “blatant lie”.
A messy battle ahead
Following the lawsuit, Cognizant refused to take the blame for what it described as Clorox’s own failures.
“Clorox hired Cognizant for a narrow scope of help desk services which Cognizant reasonably performed,” Cognizant said.
In a statement to Ars Technica, Cognizant said it was “shocking” a corporation as big as Clorox had “such an inept internal cybersecurity system” to mitigate the attack.
Mary Rose Alexander, outside counsel for The Clorox Company and partner at Latham and Watkins, later told Information Age Clorox “entrusted Cognizant with the critical responsibility of safeguarding Clorox’s corporate systems” and Cognizant “failed miserably”.
“Cognizant didn’t just drop the ball,” said Alexander.
“They handed over the keys to Clorox’s corporate network to a notorious cybercriminal group in reckless disregard for Clorox’s policies and long-established cybersecurity standards.
“It’s all captured on call recordings, and it’s indefensible.”
Who is at fault?
James Patto, founder of Melbourne-based law firm Scildan Legal, told Information Age the responsibility will depend on “several factors”, including contractual stipulations around indemnity, minimum security standards and liability caps.
“Beyond that, there’s the potential for common law claims such as negligence, particularly if there’s evidence of poor oversight or obvious risk blind spots,” said Patto.
“And there’s a broader regulatory truth: you can outsource the function, but not the risk.”
Patto explained Clorox wasn’t automatically “off the hook” and its regular procedure meetings with Cognizant were “necessary” but “not in themselves sufficient”.
“Liability will ultimately turn on the facts: what was agreed, what was known, what was done, and how risks were escalated and addressed,” he said.
Patto further pointed out a “marked increase” in supply chain-related breaches and social engineering attacks targeting offshore call centres.
Indeed, a recent data breach at Qantas is believed to be linked to Scattered Spider – the same criminal group responsible for Clorox’s 2023 attack – and also involved an incident at a third-party call centre.
“These are often relatively simple attacks, but they’re proving highly effective, especially when layered with AI-generated phishing, fake identity documents, and even voice cloning for vishing scams,” said Patto.
Alexander meanwhile told Information Age Cognizant enabled the attack and was therefore “directly responsible for the disruption to Clorox’s business operations”.
“We are committed to holding them accountable,” said Alexander.










