Paying a ransomware demand makes businesses more likely to be targeted again despite the criminals’ assurances to the contrary, according to new Australian Institute of Criminology (AIC) research that found Australian SMEs receiving multiple ransomware demands.
The research – which surveyed 331 Australian individuals and SME owners who received ransom demands after their devices were disrupted by ransomware – found that a third of the victims owned an SME and two-thirds likely worked for one.
“Business owners are easily identifiable targets as they often have a more visible online presence than other potential victims,” the report’s authors note, with public websites, social media pages and email addresses “allowing anyone to contact the business.”
Confirming that cybercriminals are using the proceeds of data breaches to target victims – HaveIBeenPwned alone added 1.96 billion stolen credentials this month – 58.6 per cent of SME owners reported having personal data leaked in the previous year.
Additionally, four in 10 said had already paid a ransom in a separate incident over the past year – compared to one in 10 of non-owners – suggesting they had either failed to improve security after the first breach, or were being retargeted by the same criminals.
Over half of the business owners had received two or three ransom messages in the preceding 12 months – compared to 27 per cent of those that don’t own an SME – and a further 12.7 per cent had received four or more demands.
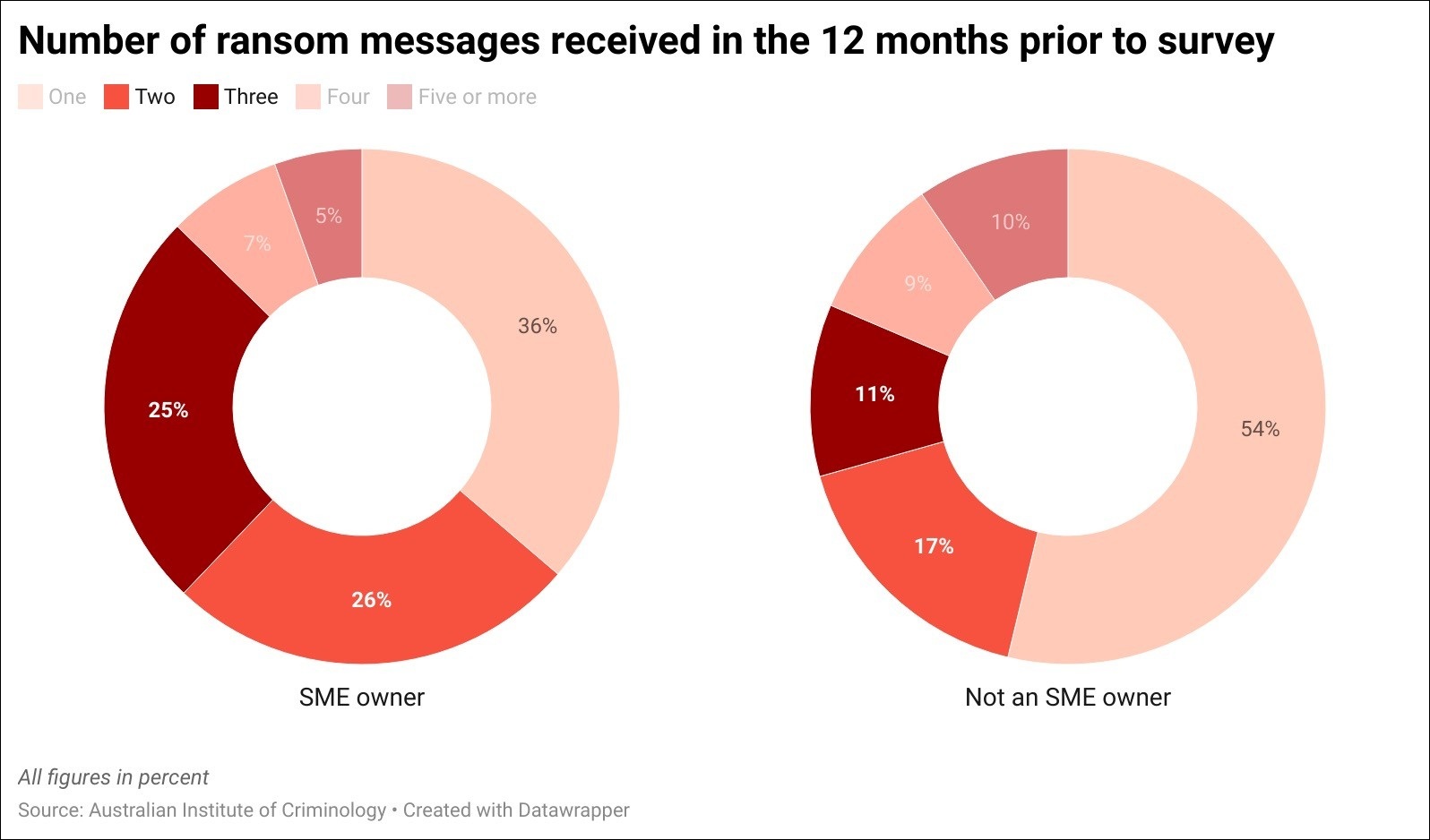
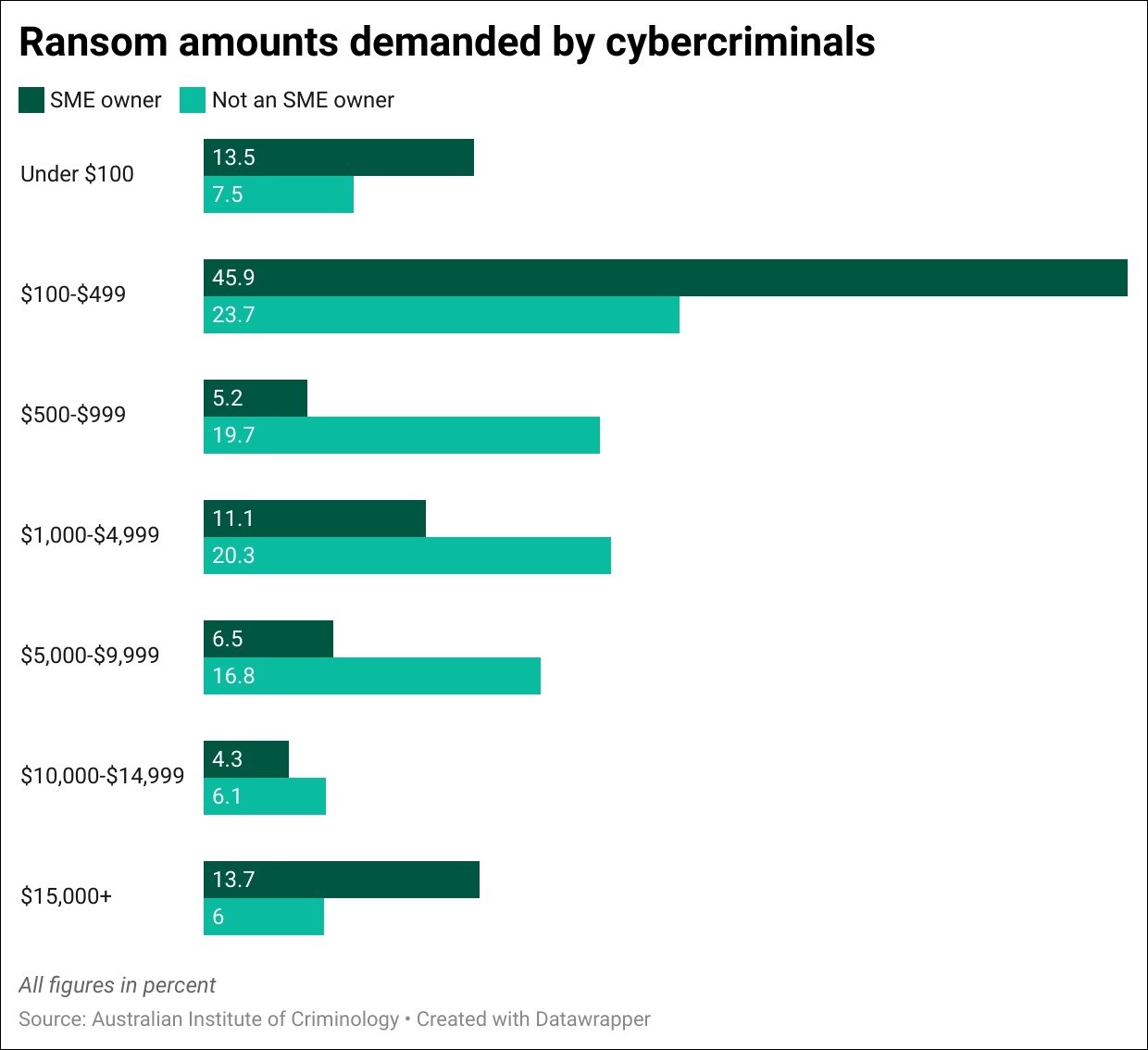
While the dollar amount of the demand was not always large – 59.4 per cent of business owners said the criminals demanded less than $500 – a further 13.7 per cent said they had been extorted for $15,000 or more, reflecting a major cashflow hit for most SMEs.
SME owners were on average given 52 days to pay the ransom, with 22.6 per cent ultimately paying the ransom to restore their data and devices; by contrast, just 7.8 per cent of non-owners paid up, after being given an average of 7 days.
“Aside from the financial impact, ransomware can see business losing all of their important records, including customer data,” AIC Deputy Director Dr Rick Brown said.
“It’s important that we understand the nature of these attacks as they are becoming more targeted, frequent and harmful.”
Pushing back against ransomware criminals
Last year the Australian Cyber Security Hotline received over 42,500 calls – up 16 per cent year on year – and ACSC responded to over 1,200 cyber security incidents, the agency recently reported, with 11 per cent of incidents involving ransomware.
Those attacks cost Australian small businesses an average of $56,600 each – up 14 per cent year on year – while medium and large businesses lost an average of $97,200 (up 55 per cent) and $202,700 (up 219 per cent) each, respectively.
Faced with such prolific, resourceful and successful ransomware gangs, increasingly multinational efforts are tracking down and prosecuting cyber criminals – with Australia recently joining 71 other signatories to adopt the UN Convention Against Cybercrime.
This week, Australia joined the US and UK in sanctioning Russia-based ransomware firm Media Land and a number of its executives, who are accused of harbouring prolific ransomware operations including Lockbit, Blacksuit, and Clop.
These ransomware gangs have actively targeted Australians and Australian financial institutions, with AFP Cyber Command assistant commissioner Richard Chin alleging the sanctioned Russians “provided cybercriminals with a perceived layer of protection.”
That perceived immunity from detection and capture has emboldened ransomware gangs to attack targets with impunity, with individuals earning millions in commissions and victims like Asahi and Jaguar Land Rover suffering billions in damages.
Last week, the US Cybersecurity and Infrastructure Security Agency (CISA) warned that the Akira ransomware gang – which has netted over $377 million ($US244 million) in ransoms by exploiting SMEs – had shifted its focus to large businesses.
Akira poses an “imminent threat to critical infrastructure,” CISA said, outlining a range of exploits and “substantive new information” about new tactics the group is using to expand operations.
Understanding how businesses are compromised
Understanding SMEs’ exposure to ransomware is important not only because of the often devastating nature of the attacks and payments, but because companies with revenues under $3 million aren’t captured by new ransomware reporting requirements.
Survey participants were chosen from the responses to the AIC’s 2023 Australian Cybercrime Survey of 13,887 adults, nearly five per cent of whom had received a ransom message on their devices in the preceding 12 months.
This was up from 2.1 per cent of respondents in an earlier 2021 survey, with owners of SMEs twice as likely as employees – and four times as likely as other respondents – to have had a device encrypted or disrupted by ransomware.
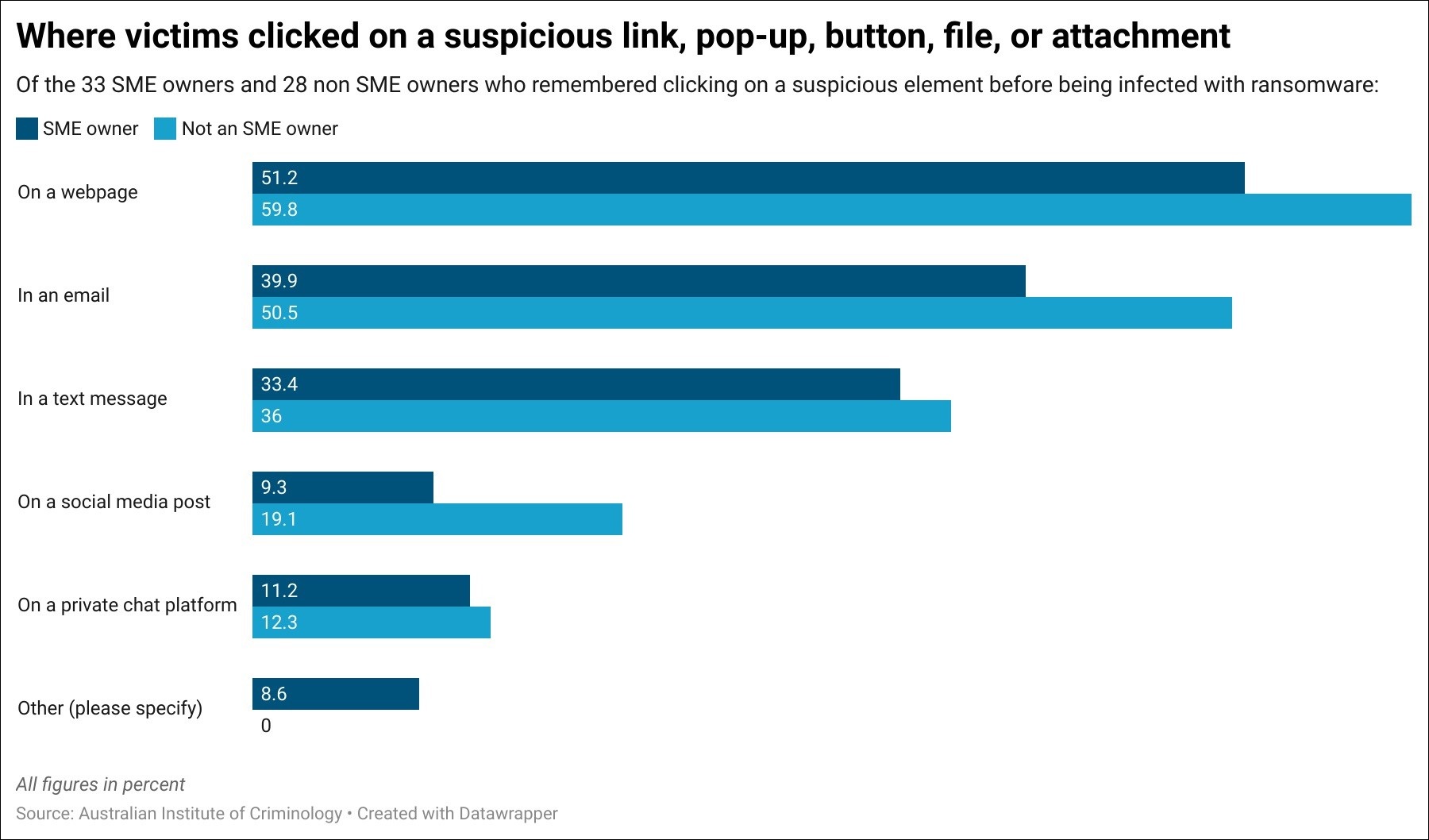
AIC asked victims how they had been compromised, with just 43.2 per cent able to remember clicking on any suspicious links, pop-ups, buttons, files, or attachments – the most common methods of ransomware infection – before their device was locked.
“This speaks to the sophistication of malware attacks,” the report’s authors note, “which makes it increasingly hard to spot malicious elements hidden in websites, texts, emails, and social media posts.”
“The impacts may not be felt until days or weeks later, meaning attributing the ransomware attack to clicking on something specific can be difficult.”










