Hackers have threatened Qantas and 38 other companies to pay a ransom by the end of the week or face their stolen data being published online.
In June, Australia’s largest airline Qantas suffered a data breach which saw nearly six million customers’ data compromised after cybercriminals convinced a call centre in the Philippines to grant them access to an unnamed, third-party customer service platform.
To date, Qantas has maintained that “there continues to be no evidence the data has been released”, though a prominent hacker collective has since claimed responsibility and demanded a ransom payment.
“Dear Qantas Airways Limited, we ARE coming for you. We will DESTROY you,” the hackers posted to messaging app Telegram on Wednesday.
The threat came five days after the hackers launched a dark web site that listed 39 companies, including Qantas, who had purportedly suffered breaches to their instances of customer management platform Salesforce.
Among these victims were Toyota, Disney/Hulu, McDonald’s, KFC, Fujifilm, HBO Max, Instacart, Puma, Adidas, Google Adsense, Cisco, IKEA, Chanel and more.
Launched by Scattered Lapsus$ Hunters (SLSH) – a collective representing three notorious cybercriminal gangs – the website warned Salesforce and the individual victims to negotiate a ransom, or face their data being released on 10 October, 11.59 PM Eastern Daylight time.
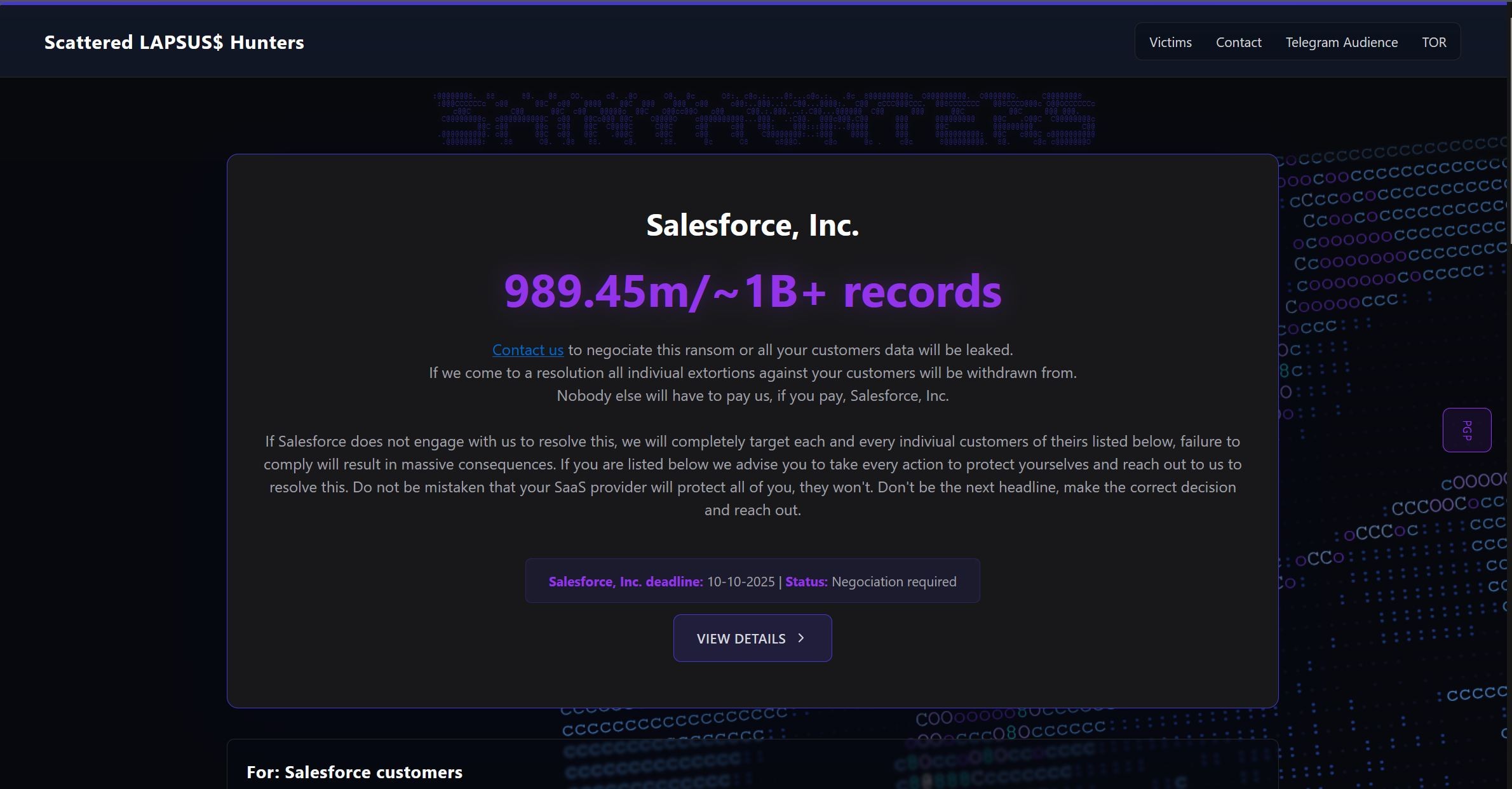
Hackers have threatened to publish more than one billion records on the dark web. Image: Internet
Aiden Sinnot, security researcher at cybersecurity company Sophos’ Counter Threat Unit, said although SLSH’s posts are often “intentional misinformation, mischief and trolling”, it remained “hard to predict what will happen on the 10th”.
“They aren't averse to leaking huge amounts of data so if they do have Qantas data I wouldn't be surprised if they leaked it,” said Sinnot.
Qantas’ compromised data included customer names, email addresses, phone numbers, dates of birth and Qantas Frequent Flyer numbers.
Qantas did not respond to Information Age prior to deadline.
SLSH’s sordid tactics
SLSH’s dark web listings included a date of when each respective victim was allegedly breached, along with a description and sample of the stolen data.
For Qantas, the website described 153GB of data allegedly stolen 28 June.
A sample of the data included what appeared to be structured datasets for customer accounts and contact details.
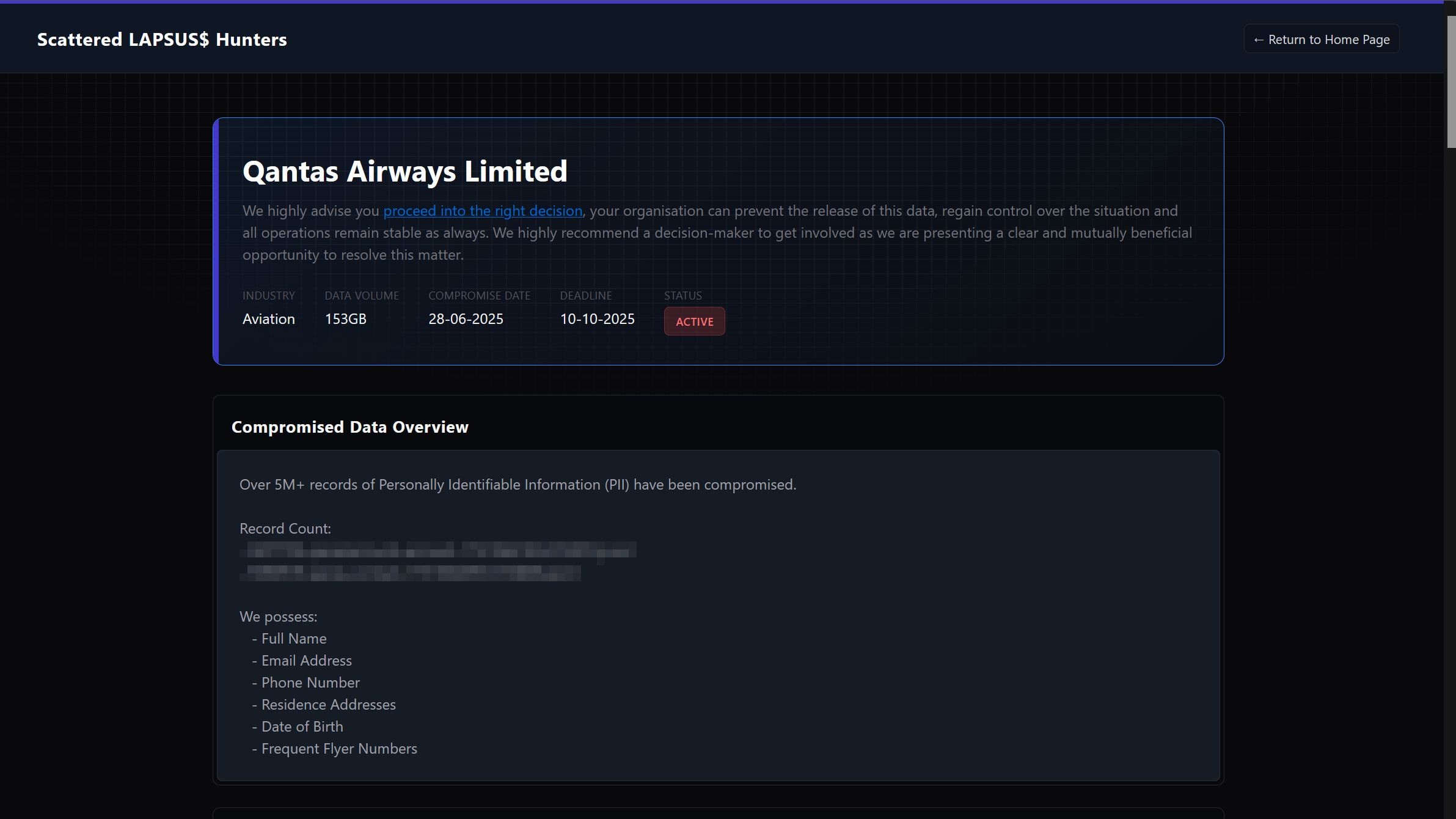
Hackers warn Qantas to make the “right decision”. Image: Internet
Last week, Google Threat Intelligence Group (GTIG) warned of a threat actor which claimed to be affiliated with SLSH participant ‘ShinyHunters’.
Tracked as ‘UNC6040’, GTIG said the “financially motivated threat cluster” specialises in voice phishing campaigns which target organisations’ Salesforces instances for “large-scale data theft and subsequent extortion”.
“Over the past several months, UNC6040 has demonstrated repeated success in breaching networks by having its operators impersonate IT support personnel in convincing telephone-based social engineering engagements,” GTIG found.
“This approach has proven particularly effective in tricking employees, often within English-speaking branches of multinational corporations, into actions that grant the attackers access or lead to the sharing of sensitive credentials, ultimately facilitating the theft of organisation’s Salesforce data.”
Hackers offer money to harass C-suites
On a Telegram channel with 13,888 subscribers, SLSH told its followers to “conduct OSINT [Open Source Intelligence] on C-suites executives” for each company listed on its dark web site.
“You are to send an email to all of the emails listed in the file informing them of their company data listing,” wrote the cybercriminals.
“Find more emails of these executives and do the same task, email them endlessly, harass them.
“The reward for this task is set to a minimum of $100.”
SLSH’s admins meanwhile used the channel to repeatedly and publicly threaten company executives to “make the right choice” and avoid being “the next headline”, while one admin was blatant enough to goad the Australian Federal Police (AFP).
“F**k da AFP we WILL leak QANTAS AIRLINES AND OPTUS DB IF WE ARE NOT PAID ON OCTOBER 10,” they said.
Is this an empty threat?
Speaking with Information Age, Vaughan Shanks, chief executive of Melbourne-based incident response vendor Cydarm Technologies, said the widescale threat to Qantas and Salesforce’s other clients represented a “desperate move by SLSH”.
“Clearly their extortion tactics are not working, so they are trying to escalate the pressure on Salesforce by leveraging the names of Salesforce customers,” said Shanks.
Shanks said although the extortion threat should be “taken seriously”, it was nevertheless “unexpected”, “audacious”, and would “probably lead to a bad outcome for the criminals involved.”
“A threat of this magnitude will no doubt draw the heat from various law enforcement and cyber agencies,” he said.
A Salesforce spokesperson told Information Age the company “will not engage, negotiate with, or pay any extortion demand”.
“At this time, there is no indication that the Salesforce platform has been compromised, nor is this activity related to any known vulnerability in our technology,” Salesforce said.
In July, Qantas obtained an interim injunction in the New South Wales Supreme Court to prevent its stolen data from being accessed or published.










