Cybercriminals have published 153GB of alleged Qantas customer data after the airline refused to co-operate with ransom demands.
After exploiting a third-party call centre and gaining access to Qantas’ data in June, hackers last week threatened to release over five million records of customer data to the dark web unless the airline paid a ransom.
With a deadline of 10 October, a Qantas spokesperson last week told the ABC an ongoing injunction it obtained meant the airline had “legal protections in place” to prevent the stolen data being “accessed or released”.
On Saturday, however, hackers dumped an apparent five million customer records to both the dark web and the open internet.
“Qantas is one of a number of companies globally that has had data released by cybercriminals following the airline’s cyber incident in early July, where customer data was stolen via a third-party platform,” said Qantas.
In July, Qantas told customers the impacted data included customer names, email addresses, phone numbers, birth dates, and Qantas Frequent Flyer numbers.
The airline confirmed Sunday the types of personal data “contained in the impacted system” have not changed, and that no credit card details, passports, personal financial information or login credentials were compromised.
“The data that was stolen is not enough to gain access to these frequent flyer accounts,” Qantas said.
When asked whether the leaked data was legitimate or if the airline opted to pay hackers a ransom, Qantas directed Information Age to an existing statement.
“Qantas continues to work closely with Australian Government agencies, including the Australian Cyber Security Centre and the Australian Federal Police,” said Qantas.
'My kids are in that dataset'
Troy Hunt, chief executive of breach tracking platform Have I Been Pwned, told Information Age he’d confirmed with a trusted, overseas third-party that the leaked data was legitimate.
The data was first leaked to a clear-web hacking forum at approximately 2.30pm AEDT Saturday, where users could purchase access to it for approximately $27.
About an hour later, the download was made available for free on the dark web.
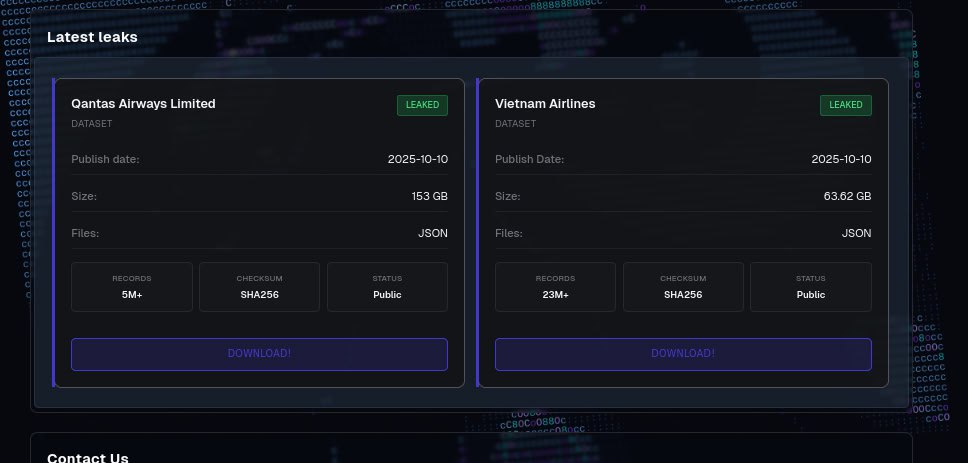
Qantas and other victims were leaked on the dark web. Photo: Supplied
Information Age did not download or view the stolen information – doing so would violate an interim injunction which Qantas obtained through the New South Wales Supreme Court in July – though Hunt said his source was able to locate Hunt’s details as an example of the data.
“They were able to relay my date of birth, my phone number… other things related to Qantas,” said Hunt.
“My kids are in there, and my wife is in there,” he added.
Qantas said it will “continue to share updates” through its website and provide “ongoing access to specialist identity protection services” through its 24/7 support line.
“With the help of specialist cybersecurity experts, we are investigating what data was part of the release,” said Qantas.
Qantas wasn’t the only victim
Earlier this month, hacker collective Scattered Lapsus$ Hunters (SLSH) told some 14,700 followers on encrypted messaging app Telegram it would begin leaking victims of a mass cybercriminal campaign as of 10 October.
In addition to Qantas, SLSH threatened to leak data from 39 companies who had purportedly suffered breaches to their instances of customer management platform Salesforce – including Toyota, Disney/Hulu, McDonald’s, KFC, Fujifilm, HBO Max, Instacart, Puma, Adidas, Google Adsense, Cisco, IKEA, Chanel and more.
A week prior, Google Threat Intelligence Group (GTIG) warned that a matching threat actor tracked as UNC6040 was explicitly targeting Salesforce customers with “voice phishing campaigns” for several months.
Though SLSH was threatening to leak over 1 billion records from its widespread campaign, Salesforce maintained its platform was not compromised, and a company spokesperson told Information Age it would not “engage, negotiate with, or pay any extortion demand”.
When the 10 October deadline arrived, SLSH leaked alleged data for only six of its announced victims, including Qantas, Vietnam Airlines, Fujifilm, Albertsons Companies, GAP, and Engie Resources.
“What was leaked was leaked,” wrote an SLSH member.
“We are not leaking anything else because we can’t.”
The leaks were promptly followed by bouts of in-fighting between the group and its followers, many who criticised SLSH for having bluffed about the extent of their data theft.
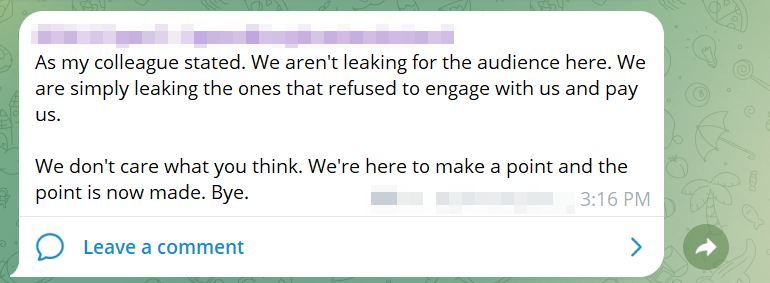
SLSH responded to backlash from a disgruntled audience. Photo: Supplied
SLSH was meanwhile pressured by mounting law enforcement action over the weekend, with the Federal Bureau of Investigation (FBI) reportedly seizing one of its publicly accessible websites on Friday.
Information Age understands the initial download links for the stolen Qantas data were taken down within hours of being released, however, Hunt said the data was likely already in “thousands of hands”.
“Who knows if we’ll see more stuff or not, but clearly, they do have legitimate data,” said Hunt.
Hackers declare war on Australia
Speaking to its followers on Sunday, SLSH declared it was specifically targeting Australian businesses.
“Our war is only with Australia. Not the Americans, not the British, not anyone else,” an SLSH member wrote.
Indeed, members of the group repeatedly claimed responsibility for publishing data from telecommunication provider Optus’ historical 2022 data breach, while another encouraged employees at Australian organisations to “work” with the group for insider attacks.
“Australia, I really hope for the love of god you've learned your lesson this time,” an SLSH member wrote.
“Drop your ego and pride and comply with us in the future.
“We will never stop, see you all in 2026.”
A spokesperson for the Australian Federal Police (AFP) told Information Age it was “aware of reports regarding a threat actor publishing compromised data”, and that Australians should be alert to potential scams.
“Some cybercriminals may use this as an opportunity to make unsolicited contact,” they said.
“It is recommended that you do not respond to unsolicited contact in relation to this matter.”
Australians are encouraged to report cybersecurity incidents at www.cyber.gov.au/report or call the Australian Cyber Security Hotline on 1300 CYBER1 (1300 292 371).










