Considering that great-sounding new dev job you saw online?
Tread carefully: North Korean cybercriminals have been caught posting job ads that are nothing more than a bait-and-switch designed to trick applicants into installing malware on their systems.
Posted through legitimate channels like LinkedIn, Facebook and Reddit, the jobs sound real enough, with one role for a remote ‘Backend Developer (Blockchain & FinTech)’ offering a salary of $170,000 to $225,000 ($US120,000 to $US160,000).
“We’re on the hunt for a backend developer who’s fluent in fintech, blockchain, and crypto exchange systems,” the ad read, promising applicants that they would “help us design and scale secure platforms that move money, data, and trust across the globe.”
Another role, posted by ‘Carol’ for a DevOps engineer with “2+ years slaying in DevOps or SRE” and “hands-on wizardry with Kubernetes and Docker”, similarly offered a six-figure salary to “work with a fast-growing AI startup redefining enterprise operations”.
The catch: these and numerous other job ads, cybersecurity company ReversingLabs has discovered, were part of an ongoing campaign called ‘graphalgo’ engineered by North Korea’s Lazarus Group, whose resume also includes last year’s $2.1 billion ($US1.5 billion) Bybit crypto heist.
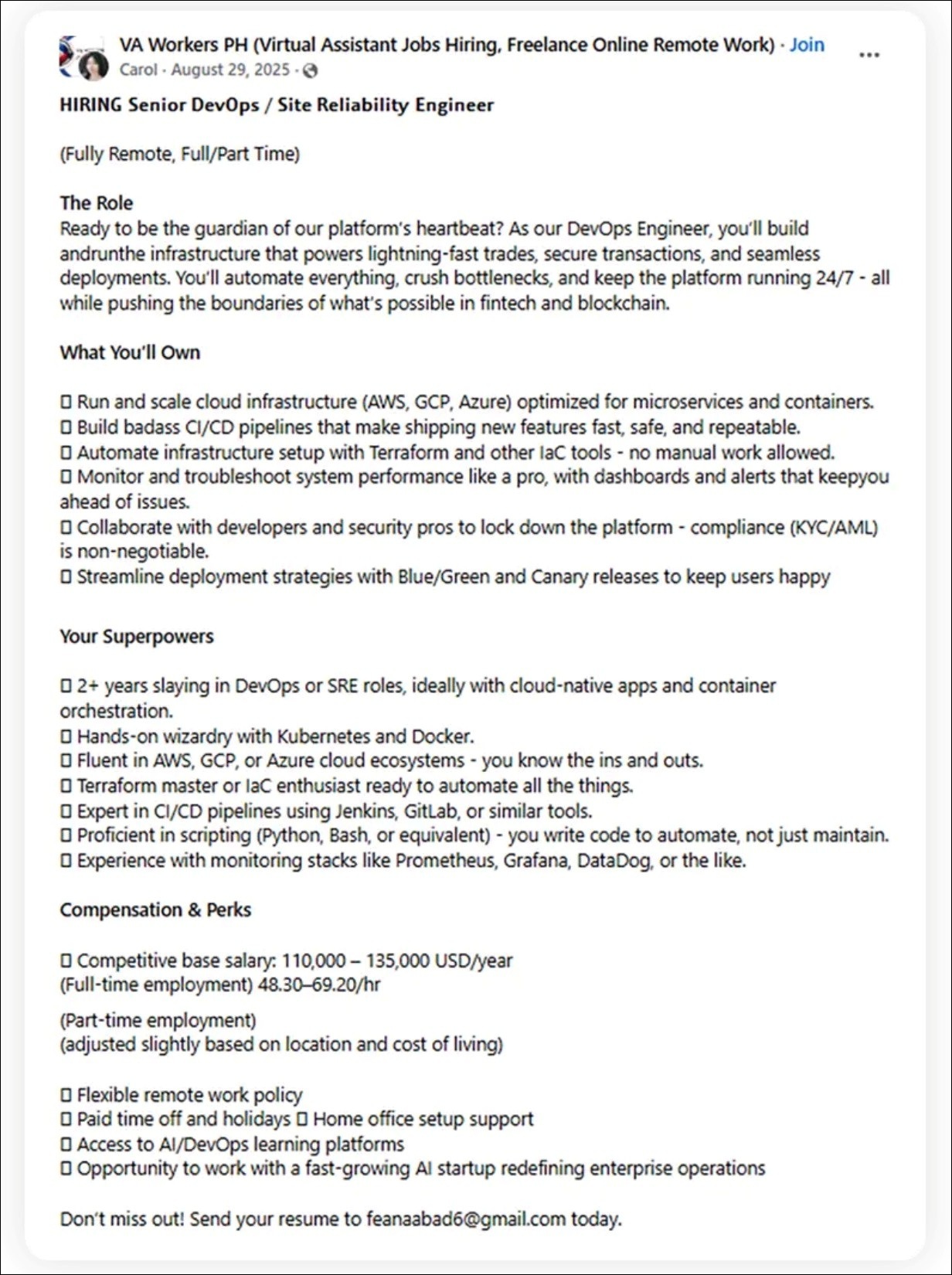
This LinkedIn job post is completely fake, and not just because it uses the word 'badass'. Just don't. Image: Supplied
The firm supposedly offering the roles, Veltrix Capital, is a shell company whose domain name was set up in April 2025 with a website filled with generic, AI generated content that is there, ReversingLabs said, “to create a sense of trustworthiness”.
The site is just the first gate in a multi-stage application process that directs them to the veltrix-capital GitHub repository, with a range of Python and Javascript projects that address a range of common DevOps and crypto-related tasks.
While that code is clean, the analysts said, once developers get stuck into the code things go downhill quickly, since the code challenges incorporate a number of malware-ridden dependencies hosted on the npm and PyPI package repositories.
Applicants are told to “run, debug, and improve the system as a DevOps engineer” but, ReversingLabs explains, “everything after ‘run’ is not important, because at that moment the malicious dependency is installed and executed on the victim’s machine.”
%20malware.jpg)
North Korean cybercriminals have carefully designed a recruitment process that tricks applicants into installing remote access trojan (RAT) malware on their system. Image: Supplied
Lazarus Group is gaming the recruitment process
It’s the latest case in which the North Korean group – a collective of crypto thieves and malware architects that has also been blamed for the massive and destructive WannaCry ransomware attack – has been caught manipulating Western recruitment.
The FBI warned in 2023 that “thousands of skilled IT workers” were moving abroad from North Korea and setting up as freelance IT professionals, warning recruiters to be wary of remote workers who won’t join video calls or behave in otherwise cagey ways.
The next year, security firm KnowBe4 realising it had hired a North Korean spy after the corporate MacBook that it sent to the new hire began launching malware attacks within moments of it being received.
Last year, US Department of Justice raids in 16 states saw the arrest of fake ‘workers’ who had secured jobs in over 100 US companies and used stolen identities to secure regular salary payments.
And last December, Amazon said it had blocked over 1,800 job applications believed to be lodged by North Koreans using stolen or fake identities – up 27 per cent year on year – with chief security officer Stephen Schmidt warning that things are getting worse.
“Identity theft has become more calculated,” he said, noting that the cybercriminals hijack dormant social media accounts and “target actual software engineers who provide real credibility, rather than people with minimal online presence.”
Claimed bona fides often don’t measure up, Schmidt added, with many applicants’ supposed CVs claiming changing educational backgrounds – California and New York universities are currently favoured – and claims of degrees those unis don’t offer.
“This isn’t Amazon-specific,” he said, but “is likely happening at scale across the industry” – urging recruiters to watch for common patterns in CVs, emails, phone numbers, as well as “anomalous technical behaviour” like “unusual remote access”.
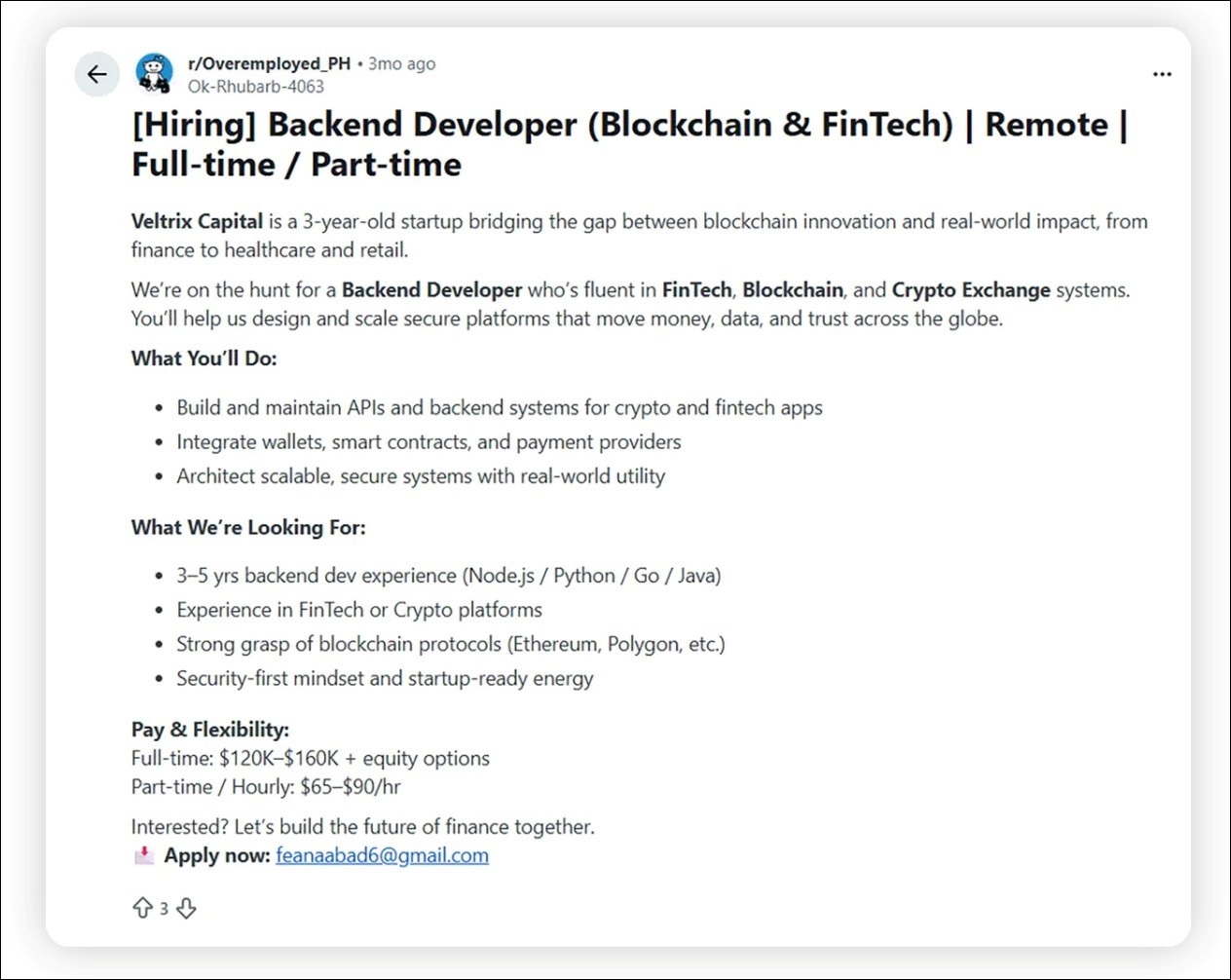
This Reddit job post lures applicants to apply for a fictitious role at a fictitious company. Image: Supplied
Be wary of red flags
The fake recruitment supply chain has proved tempting for well-intentioned job seekers, who may have ended up compromising their current employers’ systems after being tricked into installing remote access trojan (RAT) malware.
The firm warns prospective job seekers to be wary of red flags, such as being approached by purported recruiters gushing over their profiles and arguing that their experience would be a great fit for their “fully remote, flexible roles”.
Smaller signs – for example, strangely impersonal Gmail addresses, the addition of a +1 before contact numbers (something US recruiters rarely do), or being ghosted once applicants start asking more about the company – should set off warning bells.
And even with the Veltrix Capital scams exposed, ReversingLabs warns that the scheme can be easily repurposed under another company name: “the malicious payload and infrastructure responsible for its delivery doesn’t need to be changed,” it notes.
“The threat actor only needs to prepare a new fake company and job offering,” the firm said, adding that “such a modular approach shifts the burden of campaign support from expensive technical modifications to cheap social engineering activities.”