Australian courier and logistics company, Toll Group, is gradually returning to its usual operations after a ransomware attack devastated its IT systems late last week.
Toll has regularly updated its customers with information about the cyber incident that disrupted business.
“We became of the issue on Friday 31 January and, as soon as it came to light, we moved quickly to disable the relevant systems and initiate a detailed investigation to understand the cause and put in place measures to deal with it,” Toll said.
After locking down affected systems, Toll was forced to rely on “a combination of automated and manual processes” to continue operating.
“We have also increased staffing at our contact centres to assist with customer service,” Toll said.
“Notwithstanding the fact services are being provided largely as normal, some customers are experiencing delays or disruption and we’re working to address these issues as we focus on bringing our regular IT systems back online securely.”
A banner on Toll's website informed its customers of the problems.
The transportation company confirmed that it was infected by a strain of the Mailto ransomware and has shared samples of the malicious software with “law enforcement, the Australian Cyber Security Centre, and cyber security organisations” to help identify and limit the potential of future infections.
The company also said there has “no indication that any personal data has been lost” in the attack but it has not yet explained how the ransomware came to infect its systems.
Toll has no intention of paying the ransom, according to the Australian Financial Review.
AKA Netwalker
So named because it locks affected files into an unusable ‘mailto’ format, the Mailto ransomware has also been known as Netwalker after a related decrypter bearing that name was found by malware researchers.
The ransomware is still new, with early sightings of it going back to October last year.
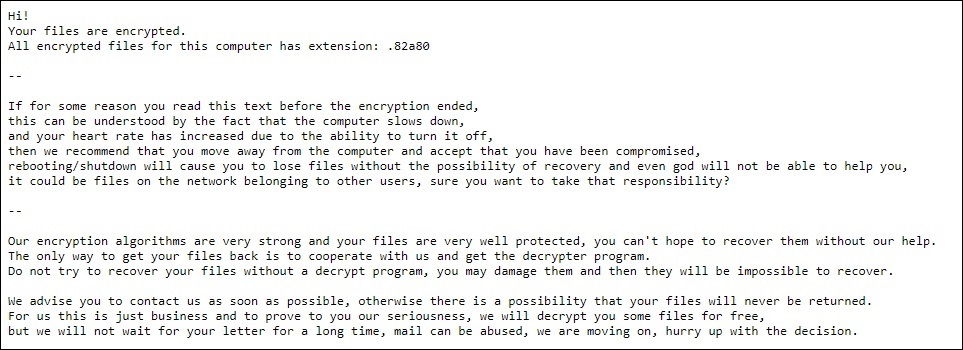
Mailto/Netwalker ransom note. Source: id-ransomware
Self-proclaimed Ethical hacker, Vitali Kremez, told Bleeping Computer that the Mailto/Netwalker ransomware has “one of the more granular and more sophisticated configurations observed”.
2020-02-05:🔥🆕#Netwalker #Ransomware
— Vitali Kremez (@VK_Intel) February 5, 2020
🔩Cfg
1⃣"prc":["psexec.exe","system"]
2⃣net":{"use":true,"ignore":{"use":true,"disk":true,"share":["ipc$","admin$"]
3⃣kill":{"use":true,"task":["reboot","restart","shutdown","logoff","back"]}
h/t @malwrhunterteam
➡️https://t.co/WDyAbzFFqQ pic.twitter.com/BCvqbbVvVX
It is thus far unknown whether or not files encrypted by Mailto/Netwalker can be decrypted, or how easy that task is.
The attack on Toll is the first known case of Mailto/Netwalker taking on enterprise-level systems.
Although Toll appears to have mitigated the effects on its business operations, ransomware can be absolutely crippling for businesses.
Recently, global currency exchange Travelex was knocked offline by what it initially referred to as a ‘virus’.
A week after first going down, Travelex revealed it had been hit by the Sodinokibi ransomware.
Many of Travelex’s websites are still down more than a month later.










