Security researchers have found a novel way of hacking a SpaceX Starlink terminal and gaining full access to the local network, raising concerns about the need to properly maintain and secure distributed infrastructure.
In a presentation at last week’s Black Hat conference in Las Vegas, Lennert Wouters demonstrated a way to bypass the in-built hardware security measures of the user terminals, small satellite dishes people use to connect with Starlink satellites.
The hack, which Wouters responsibly disclosed to SpaceX before going public, shows how a dedicated adversary could find and exploit a highly technical and previously unnoticed security flaw, finding a foothold in the satellite internet network, and causing major disruptions.
“As an attacker, let’s say you wanted to attack the satellite itself,” Wouters said via Wired.
“You could try to build your own system that allows you to talk to the satellite, but that’s quite difficult.
“So, if you want to attack the satellites, you would like to go through the user terminal as that likely makes your life easier.”
Starlink launched in Australia last year, offering high speed broadband connections via a constellation of satellites in low-Earth orbit.
Starlink customers install small satellite dishes on their homes, properties, or vans if they work nomadically, which communicate via satellite to ground stations around the world that provides high-speed, low-latency internet connections.
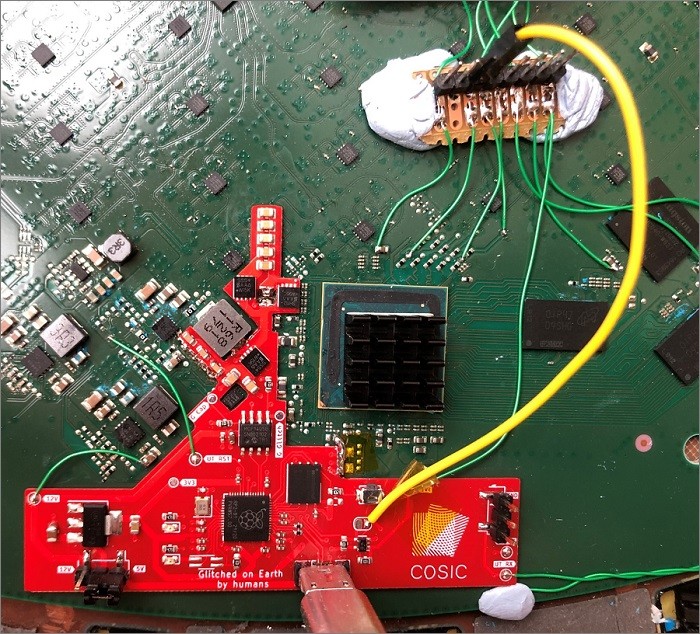
Wouters, intent on finding a way to bypass Starlink’s user controls, cracked open one of these satellite dishes using a heat gun and screwdriver and began poking around.
What he discovered was a small fault injection vulnerability in the boot cycle on the dish’s system-on-a-chip.