Is your Android device up to date?
If not, you may be leaving yourself open to Rafel RAT – a remote administration tool which quietly funnels sensitive data to ransomware criminals.
According to researchers at cyber security firm Check Point, the Rafel RAT malware has been observed in 120 different malicious campaigns, and is most commonly used for surveillance and ransomware operations on infected Android devices.
To bait users into installing the malware, Rafel RAT often impersonates popular apps such as Instagram, Whatsapp, various e-commerce platforms and, ironically, antivirus programs.
Once installed, it bolsters itself by enabling certain device permissions and in some cases ‘allowlisting’ itself in order to remain “fully undetectable”.
From here, attackers can start a game of surveillance or extortion – observing and extracting sensitive data or using their foothold to conduct ransomware attacks.
“The malware commences its operations in the background immediately upon activation,” wrote Check Point researchers Antonis Terefos and Bohdan Melnykov.
Phones at hackers’ fingertips
Much of Rafel RAT works via a customised ‘command-and-control centre', which hackers can log into remotely to both monitor and influence infected devices.
Image: Check Point
Once logged in, attackers can access information about the device, such as model specifics, its Android version, country and location, SIM operator details, and how much charge is left in the battery.
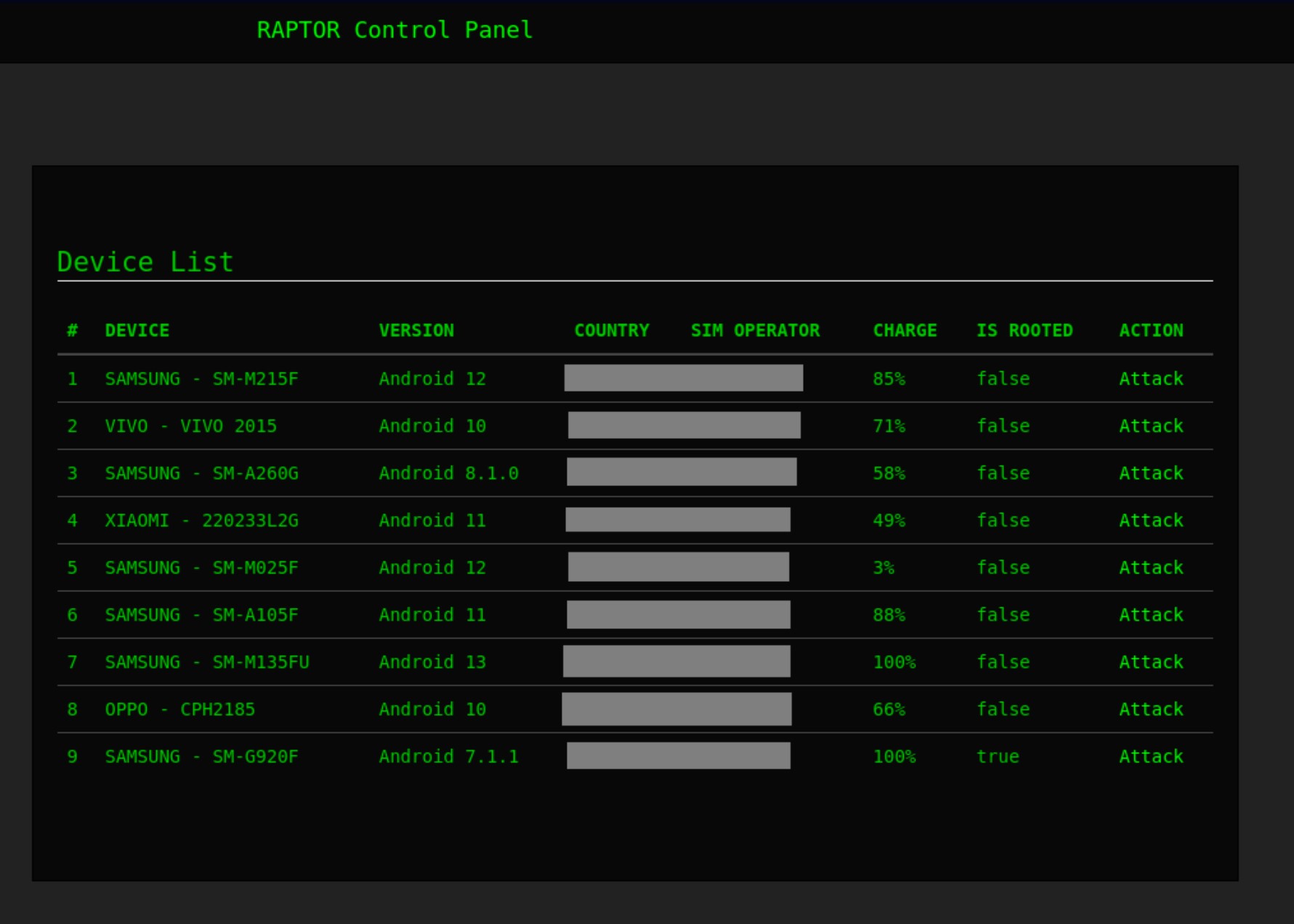
Image: Check Point
Furthermore, the command-and-control centre grants access to a suite of phone features and malicious commands which hackers can execute remotely on the infected device.
While some of these commands may seem relatively innocuous – such as its ability to change wallpapers, vibrate infected devices or retrieve call logs – Rafel RAT is most frightening when it comes to data theft and file manipulation.
The ‘GetContact’ command, for example, supplies contact details such as names and phone numbers from a victim’s device – enabling potential social engineering attacks or identity theft – while the GetSMS command allows threat actors to retrieve SMS messages.
Notably, Check Point observed malicious actors abusing this functionality to steal SMS two-factor authentication (2FA) details.
Check Point also observed the most frequently used commands were related to file encryption, file uploads, screen-locking, phone vibrations and voice-to-message commands – indicating Rafel RAT is most widely deployed for ransomware purposes.
For example, a hacker might upload a malicious file, encrypt sensitive content such as photos, messages or confidential notes, lock the screen, then bombard the victim with voice-to-text messages regarding a ransom exchange.
“In its fundamental iteration, the Rafel application possesses all the essential features required for executing extortion schemes effectively,” wrote Terefos and Melnykov.
Furthermore, Check Point found the malware is capable of sending messages through the Application Programming Interface (API) of popular messaging platform Discord.
Not only does this enable attackers to move quickly by notifying them as soon as a new victim has installed Rafel RAT, but the communication method is also used to intercept and forward device notifications, potentially exposing sensitive information and 2FA codes from installed apps.
To make matters worse, Rafel RAT is open-source meaning it can be easily picked up and distributed by multiple threat actors.
“High-profile” global targets
Check Point noted in some cases, Rafel RAT has been used to successfully target high-profile organisations, including those within the military sector.
While the majority of known victims reside in the US, China, and Indonesia, Check Point observed the malware has also targeted devices in Australia, New Zealand, Russia and other countries.
In one case, a threat actor successfully used the malware while hacking a Pakistani government website.
Phone manufacturer Samsung was most targeted by the malware, with the Samsung Galaxy Note, A and S models comprising more than a quarter of known attacks.
Rival brands Xiamoi, Vivo and Huawei comprised the second-largest group among known victims, while Google Pixel and LG Nexus owners comprised approximately 11 per cent of victims respectively.
The word of the day is “update”
Check Point researchers noted more than 87 per cent of victims are running Android versions that are “no longer supported and, consequently, not receiving security fixes”, with infections being most prevalent on Android 11, followed by versions 8 and 5.
“Despite the variety of Android versions, malware can generally operate across all,” wrote Terefos and Melnykov.
“However, newer versions of the operating system typically present more challenges for malware to execute its functions or require more actions from the victim to be effective.”
As for how to avoid Rafel RAT and similar malware, Check Point recommended users update their Android operating system and apps regularly.
Furthermore, the firm stressed users should only download and install apps from trusted sources such as the Google Play Store, and should be cautious of apps with fewer downloads or poor reviews.
“As attackers employ increasingly sophisticated techniques to evade detection and compromise devices, understanding the nature of Android malware, its distribution methods and effective prevention and mitigation strategies become paramount,” wrote Terefos and Melnykov.










