Received a payment demand for an overdue toll or shipping fees?
Ignore it: it may be part of a ‘ghost tapping’ scam in which cybercriminals take over your credit card by tricking Apple Pay and Google Pay to bill you for their purchases.
The past year has seen law enforcement authorities worldwide increasingly concerned about ghost tapping, which starts with a ‘smishing’ attack or phishing email that alleges a fictitious debt and pressures you to click a link where you can enter your payment details.
If you actually do so, you’ll be directed to a screen where you will enter your card number, expiration date and phone number.
You’ll then get a verification code, which is allegedly to confirm the payment – but is actually the verification code sent by Apple or Google as a cybercriminal adds your card to their own phone’s Apple Pay or Google Pay digital wallet.
Once they’re done, they can use your card to pay for purchases at point-of-sale (POS) terminals – or, by using hacking tools originally created by German researchers years ago, transfer the details for use by an accomplice anywhere in the world.
Ghost tapping victim Ian Williams recently told ABC about his 2022 discovery of $1,388 in suspicious card charges made at a Coles supermarket 150km from his home – and the legal saga that has him eyeballing a $300 million judgement against the NAB.
The bank and its U-Bank subsidiary should have detected the fraud, he alleges, but failed and then accused him of lying – arguing that he authorised the transactions by scanning his thumbprint on his phone – but he flat-out rejects this as impossible.
The person who actually scanned their thumbprint to verify the payments, it now seems clear, was a cybercriminal who ensnared Williams in a ghost tapping scam and added his card details to one of the many card-filled phones being hawked on darkweb sites.
Security firm Resecurity found Chinese cybercriminals building ‘farms’ of typically Android-based phones that are loaded with a half dozen stolen credit cards each to “automate fraud at scale” and using custom apps to control the phones’ built-in NFC chips.
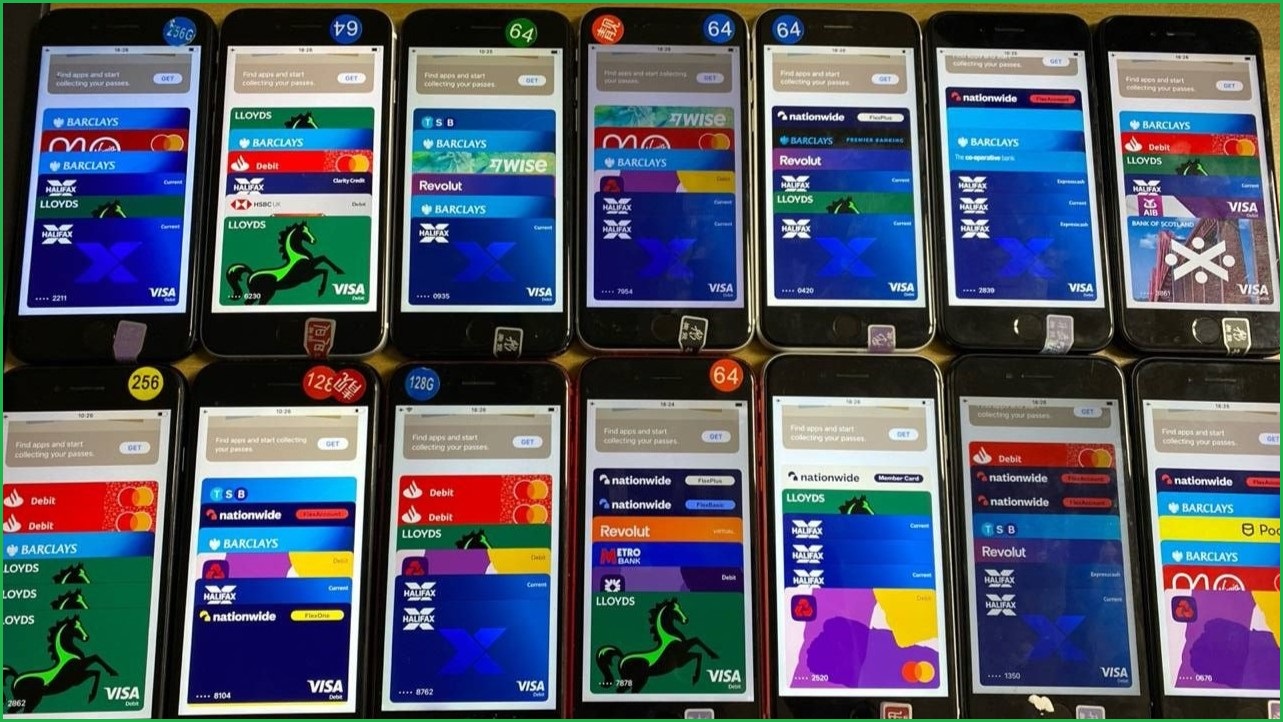
Chinese cybercriminals are using and selling Android phones preloaded with credit cards from the likes of Barclays, Lloyds, Revolut, and other institutions. Source: Resecurity
Was Apple right about NFC security?
NFC (near-field communication) chips – built into all modern smartphones and watches – allow phones and smart watches to make purchases by sending card data to the NFC readers built into shops’ POS terminals.
Apple previously got into a protracted bunfight with the NAB and other Australian banks because it wouldn’t let their banking apps directly access customers’ NFC chips – something that would have let the banks bypass Apple Pay’s fees and technical controls.
The banks claimed Apple was forcing them to route customer payments through Apple Pay, allowing the tech giant to clip customers’ tickets on the way through; Apple insisted that opening up the NFC chips to all and sundry was just handing criminals the keys to the kingdom.
The dispute persisted until European Union regulators walked Apple to the end of a regulatory gangplank and it finally relented – opening up its NFC chips to certain other payment providers amidst warnings that security would be the first casualty.
It can hardly be coincidence that, months later, authorities noticed a surge in ghost tapping – with one client of Dutch security firm ThreatFabric asking it to explore why customers seemed to be making purchases in two far flung geographic locations at the same time.
“We stumbled across this by the end of 2024 when we saw these unexplained spendings and our customer asked us why their customers seemed to teleport,” ThreatFabric vice president of engineering Eward Driehuis told the ABC.
“For the first time last year, we saw criminals were doing this and selling these [phones] online for other criminals,” he continued, noting that “once your information is social engineered, it’s actually very easy to provision cards on new mobile phones.”
Changing data
Card theft is only part of the story, however: in 2020, students at Germany’s Technical University of Darmstadt wrote a tool called NFCgate that can monitor and change the NFC data sent between phones and POS terminals.
It was created as a “research toolkit”, but NFCgate was soon appropriated by cybercriminals who used it to build a tool called NGate – which was discovered in August – that can reroute payment data from a compromised phone to another phone anywhere in the world.

Criminals no longer need a physical credit card to scam you. Photo: Shutterstock
This meant a cybercriminal can use your card to ‘pay’ for purchases by routing Google Pay transaction data to the phone of an accomplice anywhere in the world, feeding it to the POS terminal through the NFC chip on the accomplice’s phone.
In October, the FBI issued a formal advisory about Track2NFC, an app that – like others that use Host Card emulation (HCE) techniques to make the phone act like a physical NFC chip – tricks POS terminals into offline mode to process and queue the transactions without validating them.
Don’t be spooked by ghost tapping
Surveillance video reviews confirmed that the transactions on Williams’s card were made by two young men, supporting his protestations and motivating the NAB to offer a refund – yet as he pursues a potential windfall in the Supreme Court, he’s just one victim of many.
The problem, Dreihuis said, is that many people don’t take the time to read incoming text messages and consider what’s happening; ghost tapping victims that had done so would, he said, quickly realise that the request for a confirmation code was from Apple or Google.
Williams, it turns out, did get such a message days before the transaction went through – asking him to confirm his intention to add his card to a Google Pay account – but he doesn’t recall even seeing it.
As ever, vigilance is key to protecting yourself from ghost tapping: read your messages carefully, don’t tap on links or provide personal or financial details to anybody that contacts you to request them, and don’t provide confirmation codes for anything to anybody.
“If you’ve given up your information,” he said, “it means you not only have the ability to be defrauded, but you have the possibility that a criminal maybe days or months later will use that information to fraud you [and] you likely [won’t] remember that text message that led to it.”










